Author: Echo Diaz
Throughout Echo's four year stint as a technical support specialist, her passion for breaking down complex concepts had to lead to a career in professional writing. As a former top tier support specialist, she added a distinctive element to her written work that spoke to customer feedback and concerns. Echo occasionally pops her head out from behind her computer to watch her dog energetically run around the yard and unabashedly shovels money into buying tickets to see her favorite musical artists.
Troubleshooting: Could Not Resolve Host
You may find the “can’t resolve hostname” or “temporary failure in name resolution” error when using retrieval command like wget, cURL, ping or nslookup. There are many reasons why these commands can cause an error, including file corruption. For the sake of brevity, we look towards commonalities between these commands to solve the issue.
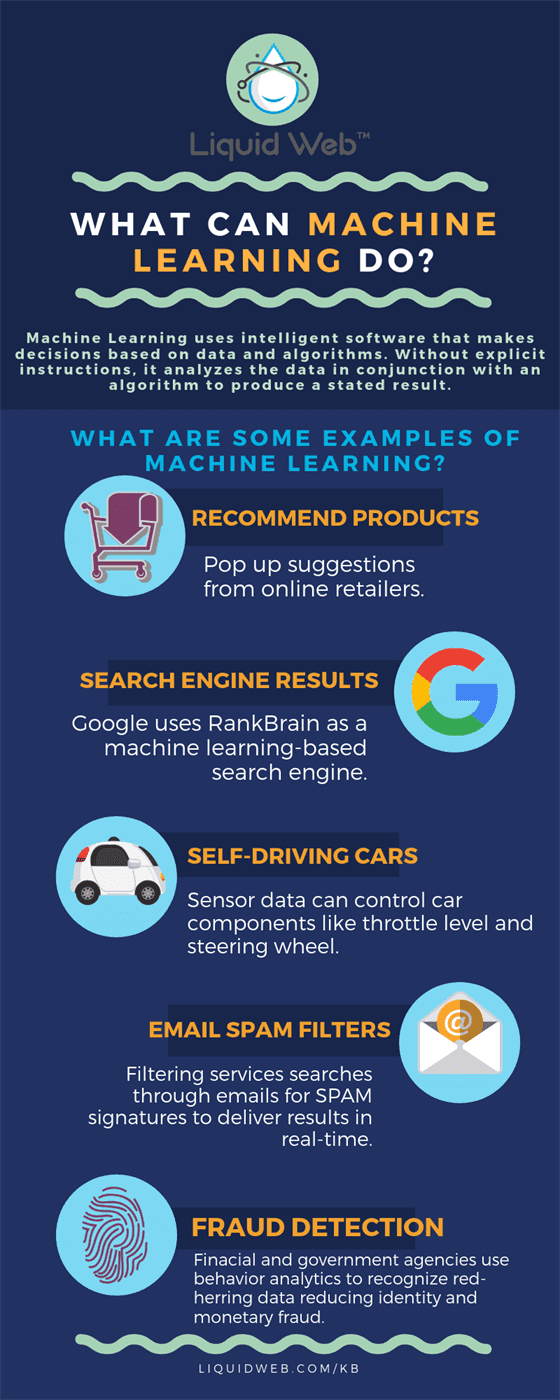
What Can Machine Learning Do? [Infographic]
Similar to Dropbox and Google Drive, Nextcloud is self-hosting software that allows you to share files, contacts, and calendars. But, unlike Dropbox and Google Drive, your files will be private and stored on your server instead of a third-party server. Nextcloud is a GDPR and HIPAA compliant hosting solution, so your files will be encrypted along with the ability to audit. For this tutorial, we’ll be installing our Nextcloud instance on our Ubuntu VPS server.
Troubleshooting: MySQL/MariaDB Error #1044 & #1045 Access Denied for User
When using PhpMyAdmin, it’s essential to have the correct user permissions to create edits/writes to the database. Otherwise, insufficient permissions can lead to errors like the ones pictured below “#1044 – Access denied for user …[using password: YES]” and “#1045 – Access denied for user…[using password: YES]”. In our tutorial, we’ll show you how to correct this issue using the command line terminal. Let’s get started!
How to Setup Let’s Encrypt on Ubuntu 18.04
Sites with SSL are needed more and more every day. Its ubiquitous enforcement challenges website encryption and is even an effort that Google has taken up. Certbot and Let’s Encrypt are popular solutions for big and small businesses alike because of the ease of implementation. Certbot is a software client that can be downloaded on a server, like one of our Ubuntu VPS servers, to install and auto-renew SSLs. It obtains these SSLs by working with the well known SSL provider called Let’s Encrypt. In this tutorial, we’ll be showing you a swift way of getting HTTPS enabled on your site. Let’s get started!
How to Install MariaDB on Ubuntu 18.04
MariaDB is a drop in replacement for MySQL, and its popularity makes for several other applications to work in conjunction with it. If you’re interested in a MariaDB server without the maintenance, then check out our high-availability platform. Otherwise, we’ll be installing MariaDB 10 onto our Liquid Web Ubuntu VPS server, let’s get started!
Apache Tomcat is an accessible, open-source application server used to house many of today applications. It's free, stable, lightweight and is utilized to render Java coding as well a range of other applications.
What Does Varnish Do?
Varnish is a website accelerator. It’s designed to decrease the time it takes for your website to load and an ideal tool for improving performance on busy, mission-critical sites.
Install and Configure Git on Ubuntu 18.04
What is the purpose of Git?
Git gives you a way to not only track changes in source code, but it can also be used to track changes in files. It then stores the data in what is called a repository, also known as a repo. In short, Git is a tool used as a version control system (VCS), allowing you to distribute changes from your local machine to the repo and vice versa. In this tutorial, we’ll be instructing on how to install and configure git onto an Ubuntu 18.04 server.
How to Install Java on CentOS 7 (Java 8)
In this tutorial, we’ll be showing you how to install Oracle’s Java 8 programming language specifically onto a CentOS 7 server. This simple object-oriented language is used for many of the applications and websites you come across today. Let’s jump right in!
Our Sales and Support teams are available 24 hours by phone or e-mail to assist.