Securing RDP by Changing Default RDP Port Numbers & More Tips
Remote Desktop Protocol (RDP) is the easiest and most common method for managing a Windows server remotely. RDP is a type of service that enables users to remotely access and configure a Windows server or a computer from anywhere in the world. It provides a convenient way to work on a remote system as if you were physically present at the machine. RDP is commonly used by businesses and individuals for remote administration, technical support, and telecommuting.
How Does RDP Work?
RDP operates by establishing and maintaining a connection between a user's computer and a remote computer or server. The client computer runs an RDP client software, while the remote host runs an RDP server software. When a user initiates an RDP session, the client software sends commands and input signals to the server, which processes them and sends back the results to the client, effectively mirroring the remote system's display on the client's screen.
How Widely Available is RDP?
Included in all versions of Windows Server, RDP also has a built-in client on all Windows desktops. There are also free applications available for Macintosh and Linux-based desktops. For an entire list of supported client operating systems, refer to our How to Access Your Windows Server Using Remote Desktop article. For group administration guidance, refer to our How to Configure Windows Remote Desktop Users Group article
Are There Security Risks Using RDP?
Unfortunately, because it is so widely used, RDP is also the target of a large number of brute force attacks on the server. Malicious users will use compromised computers to attempt to connect to your server using RDP. Even if the attack is unsuccessful in guessing your administrator password, just the flood of attempted connections can cause instability and other performance issues on your server. Fortunately, there are some approaches you can use to minimize your exposure to these types of attacks.
Common Use Cases for RDP
RDP has various use cases in both professional and personal settings. Some common scenarios include:
- Remote Administration: IT administrators often use RDP to remotely manage and troubleshoot servers and workstations.
- Telecommuting: RDP allows remote workers to securely access their work computers from anywhere in the world.
- Collaboration: RDP enables remote teams to work together on shared projects and resources.
- Technical Support: Support personnel can use RDP to remotely assist customers and resolve technical issues.
- Virtual Desktop Infrastructure: RDP is often used to deliver virtual desktop environments to users,
providing a centralized and secure computing environment.
The Liquid Web Knowledge Base contains a helpful Remote Desktop Protocol (RDP) Remote Troubleshooting Guide for customers leveraging these kinds of remote connections. One such scenario is when a user gets locked out of RDP.
5 Tips on Securing Remote Desktop Protocol (RDP) Connections
So are you curious wow to better secure RDP connections after learning they can be the target for hackers or bad actors? While it is true that RDP offers convenience and flexibility, it also poses security risks if not adequately secured. The following five tips will guide you on how to secure RDP.
Securing RDP Tip #1 — Using a VPN
A Virtual Private Network (or VPN) creates a secure, encrypted tunnel between your device and the remote desktop and it represents an important step in securing RDP. By using a VPN, you can ensure that all the traffic between your local machine and the remote system is protected from eavesdropping and tampering. It adds an extra layer of security by authenticating and encrypting the communication, making it difficult for unauthorized individuals to intercept sensitive information.
Using a VPN is one of the best ways to protect your server from malicious attacks over RDP. Using a VPN connection means that before attempting to reach your server, a connection must first be made to the secure private network. This private network is encrypted and hosted outside your server, so the secure connection itself does not require any of your server’s resources.
Once connected to the private network, your workstation is assigned a private IP address that is then used to open the RDP connection to the server. When using a VPN, the server is configured only to allow connections from the VPN address, rejecting any attempts from outside IP addresses (see our Scoping Ports in Windows Firewall article). The VPN not only protects the server from malicious connections, but it also protects the data transmitted between your local workstation and the server over the VPN connection. For more information, see our article What is a VPN Tunnel?
Securing RDP Tip #2 — Using a Hardware Firewall
Deploying a hardware firewall is another effective measure to secure remote desktops. A hardware firewall is situated between your local network and the internet, inspecting incoming and outgoing traffic for potential threats.
By configuring the firewall to only allow RDP connections from trusted IP addresses or specific network segments, you can significantly reduce the risk of unauthorized access. Additionally, a hardware firewall can provide additional features, such as intrusion detection and prevention, further enhancing the security of your remote desktop environment.
Like using a VPN, adding a hardware firewall to your server infrastructure further protects your server from malicious attacks. You can add a Liquid Web hardware firewall powered by Ciscoto your account to allow only RDP connection from a trusted location. Our firewalls operate in much the same way that the software Windows firewall operates, but the functions are handled on the hardware itself, keeping your server resources free to handle legitimate requests. To learn more about adding a hardware firewall to your account, contact our Solutions Team. If you already have a Liquid Web firewall in place, our Support Team can verify that it is correctly configured to protect RDP connections.
Securing RDP Tip #3 — Identify Trusted IP Addresses
It is essential to identify and whitelist trusted IP addresses or IP ranges that are allowed to connect to your remote desktops to minimize the risk of unauthorized access. By restricting access to known IP addresses, you can effectively block connection attempts from unknown or potentially malicious sources. Regularly reviewing and updating the list of trusted IP addresses is crucial to ensure that only authorized individuals can establish an RDP connection.
An integral part of securing your server is identifying trusted IP addresses that are not limited in scope by the firewall. This allows selected connections filtered by IP to gain access to the server. To accomplish this, we open a web browser from all the computers that are permitted to connect to the server. Then, browse to the Liquid Web Internet Web Hosting Toolkit > IP checker Tool and note the reporting IP address presented on that page. With that information, we then proceed to the next section on "scoping" a port or adding a firewall rule.
If you have issues, please see our article on troubleshooting RDP connections. Alternatively, if you simply need to find your public IP address, use this link. As well, the What’s My DNS? article can be of help.
Securing RDP Tip #4 — Scoping the RDP Firewall Rule
When configuring your network firewall to allow RDP connections, it is important to scope the rule appropriately for securing RDP efficiently. Limit the allowed source IP addresses to only those that require RDP access and avoid exposing RDP ports to the entire internet. Furthermore, consider using Network Address Translation (NAT) to map a specific external port to the standard RDP port (3389) on the internal network. This way, you can add an extra layer of obscurity and reduce the likelihood of automated scanning and brute force attacks targeting the default RDP port.
Similar to using a VPN, you can use your Windows firewall to limit access to your RDP port (by default, port 3389). The process of restricting access to a port to a single IP address or group of IP addresses is known as “scoping” the port. When you scope the RDP port, your server will no longer accept connection attempts from any IP address not included in the scope. Scoping frees up server resources because the server doesn’t need to process malicious connection attempts, the rejected unauthorized user is denied at the firewall before ever reaching the RDP system.
Here are the steps necessary to scope your RDP port:
- Log in to the server, click on the Windows icon, and type Windows Firewall into the search bar:

- Click on Windows Firewall with Advanced Security.
- Click on Inbound Rules:
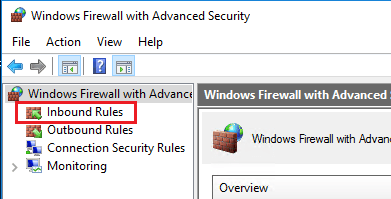
- Scroll down to find a rule labeled RDP (or using port 3389).
- Double-click on the rule, then click the Scope tab:
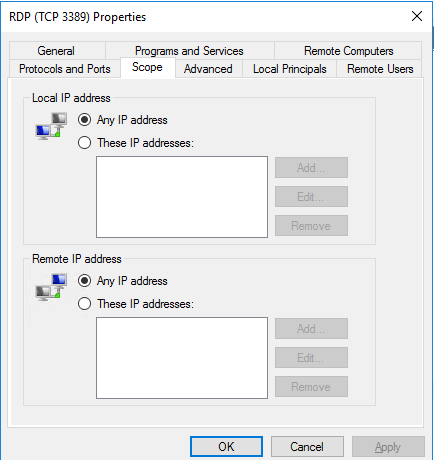
- Make sure to include your current IP address in the list of allowed Remote IPs (you can find your current public IP address by our Liquid Web IP Checker link.
- Click on the radio button for These IP Addresses: under Remote IP addresses.
- Click OK to save the changes.
Securing RDP Tip #5 — Changing the RDP Port
Changing the default RDP port is a simple yet effective security measure. Since many attackers target the standard RDP port (3389), changing it to a non-standard port can make it harder for them to locate and exploit your remote desktops. However, keep in mind that changing this port will require updating the RDP client software settings accordingly to establish a successful connection.
While scoping the RDP port is a great way to protect your server from malicious attempts using the Remote Desktop Protocol (RDP), sometimes it is not possible to scope the port. For instance, if you or your developer must use a dynamic IP address connection, it may not be practical to limit access based on IP address. However, there are still steps you can take to improve performance and security for RDP connections.
Most brute force attacks on RDP use the default port of 3389. If there are numerous failed attempts to log in via RDP, you can change the port that RDP uses for connections. Follow these steps to change the RDP port:
- Before changing the RDP port, make sure the new port you want to use is open in the firewall to prevent being locked out of your server. The best way to do this is duplicate the current firewall rule for RDP, then update the new rule with the new port number you want to use.
- Log into your server and open the Registry editor by entering regedit.exe in the search bar.
- Once in the registry navigate to the following: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp.
- Once there scroll down the list till you find PortNumber.
- Double-clicking on this will bring up the editor box.
- Change it from HEX to DEC so it's in numbers.
- Set the port number here and click OK. You can use whatever port number you wish, but you should pick a port that already isn’t in use for another service. A list of commonly used port numbers can be found on the StationX Common Ports Cheat Sheet page.
- Close the registry editor and reboot the server.
- Be sure to reconnect to the server with the new RDP port number.
FAQs on Securing RDP
1. What are other RDP risks that must regularly be monitored and managed?
Answer: In addition to the tips provided, it is important to regularly monitor and manage risks such as weak passwords, brute force attacks, credential theft, and outdated RDP client/server software versions. Conducting security assessments and employing intrusion detection systems can help in detecting and mitigating possible vulnerabilities.
2. What are some secure remote access alternatives to RDP?
Answer: There are several secure remote access alternatives to RDP, including Virtual Private Network (VPN) solutions, remote desktop software with built-in encryption, and remote access tools that utilize secure protocols such as SSH (Secure Shell) or HTTPS (Hypertext Transfer Protocol Secure).
3. Should I replace RDP or just better secure it?
Answer: The answer depends on your specific needs and requirements. If you are satisfied with the functionality and benefits of RDP but want to enhance its security, implementing the recommended security measures can be an effective approach. However, if you have specific concerns or require additional features, exploring alternative remote access solutions might be worth considering.
Wrapping Up
Securing RDP is of great importance when it comes to protecting sensitive information and preventing security breaches. By implementing the tips mentioned above on how to secure RDP, such as using a VPN, employing a hardware firewall, identifying trusted IP addresses, scoping the RDP firewall rule, and changing the RDP port, you can significantly enhance the security of your remote desktop environment.
Remember that securing RDP is a continuous process. You should regularly monitor and manage other RDP risks, such as employing strong authentication mechanisms, using complex passwords, applying security patches and updates, and conducting regular security audits. Check out our Security & Compliance product add-ons to get started improving your overall site security.
Join Us Today!
For your web hosting requirements, Liquid Web offers VPS Hosting,Cloud Dedicated Servers,VMWare Private Cloud Solutions, Private Parent Servers, and a Dedicated Servers — within our comprehensive portfolio of hosting products.
Our team of experienced Linux support technicians and talented system administrators is always available to assist you with any concerns and provide assistance. Contact our sales team to launch your outstanding website online. We pride ourselves on being The Most Helpful Humans In Hosting®!
Original Publication Date
This article was originally published in November 2020. It has since been updated for accuracy and comprehensiveness.
Related Articles:

About the Author: David Richards
David Richards has been an educator, a Technology Director, and now a Technical Writer for 20+ years. He’s an English major with a love for technology and helping others find ways to use technology more effectively. In his free time, Dave loves to read, play games, and spend time with his family.
Our Sales and Support teams are available 24 hours by phone or e-mail to assist.
Latest Articles
In-place CentOS 7 upgrades
Read ArticleHow to use kill commands in Linux
Read ArticleChange cPanel password from WebHost Manager (WHM)
Read ArticleChange cPanel password from WebHost Manager (WHM)
Read ArticleChange the root password in WebHost Manager (WHM)
Read Article


