What is a Virtual Private Network and How Does it Work?
What is a VPN?

A Virtual private network (VPNs) creates a secure connection between a remote computer and another network. The connection itself is encapsulated and encrypted which provides a protected communications channel between the two points.
A VPN is becoming more crucial in today's security-related society. Due to increasing safety concerns, the proportional use of these services is growing exponentially. This technology targets several critical aspects of our online experience: mainly privacy and security.
To better appreciate how VPNs work, we first need to understand how we navigate the internet. Any device connected to a network, whether public or private, is issued an IP address. An IP address is a set of four numbers called octets used to identify a particular device within that network. For instance, if we want to reach Google's site, we send a request from our browser to a Google server over the internet. This request establishes a communication channel with the server to gather the information we are searching for.
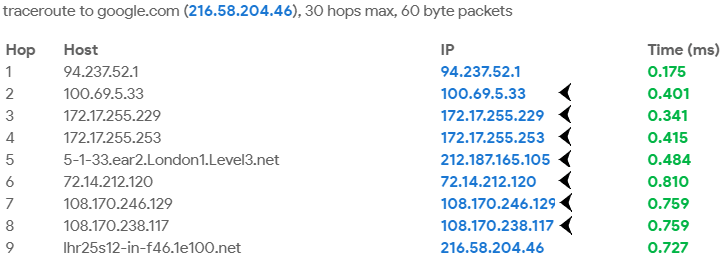
In the image below, we can see the path that a browser request (from IP 94.237.52.1) takes to connect to Google (216.58.204.46). Each IP listed in this traceroute is a network device or node used to reach Google. Each node is a considered public connection from which a malicious actor can use to intercept our request. These attackers can track down these IP addresses and gather a great deal of sensitive information.
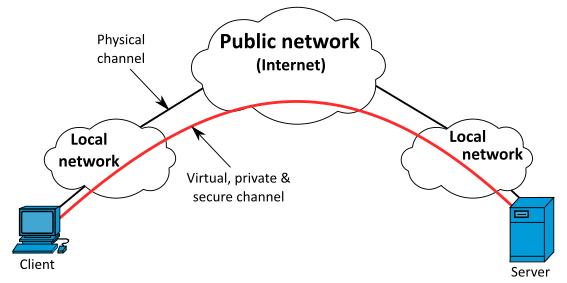
What is a VPN Tunnel?
To provide a quick reference, let's say we connect to the World Wide Web via a transparent pipe. In this pipe, data flows like water back and forth from our browser to the websites. If anyone looks at this pipe, they can see the type of traffic passing through that pipe. A VPN initiates an opaque pipe that both encapsulates and encrypts the data from prying eyes inside the original pipe to provide a more secure connection. Basically, a VPN tunnel rearranges our data into a different form, typically using encryption, which hides the true nature of the traffic running through the tunnel.
VPN Set Up
To set up a connection like this, companies need a unique combination of hardware and software. At first, many companies tended to set up their own VPN servers and remote connections. However, managed VPN solutions became more useful and widely accepted. This relieved companies of the burden of purchasing new software and equipment needed to run a VPN server.
In short, we can imagine a managed VPN service in the same way we think of managed servers. Hosting companies provided the necessary infrastructure for their clients to run websites, whereas managed VPN providers implemented the essential network infrastructure to access those websites securely.
What Can a VPN do for You?
A VPN has several advantages to protect your privacy and your business in most online activities.
Overcome Internet Censorship
When a VPN server is used, users can defeat location-based restrictions. Depending on the VPN server's actual location, users can access content blocked by a country or avoid government surveillance.
Hide Sensitive Information
Given the nature of VPN protocols, browsing the web using a VPN connection is inherently safer. Since the VPN server makes the requests, it hides the original IP from the destination server, making your data less vulnerable to attackers. It also creates a defense when using a public Wi-Fi network since the data transmitted is encrypted by the VPN tunnel.
Access a Secure Remote Environment
Among other indispensable considerations, setting up a managed VPN is vital in providing a secure environment for users to connect to the office remotely. This service decreases investments in costly equipment and time spent in setting up configurations. A VPN is essential to a business's continuity to ensure information is safety and security transmitted, especially during the difficult times we currently face.
Provide Access to Isolated Networks
A VPN is essential when a company has a server that stores sensitive information in an isolated environment within the network. Typically, isolation works well to protect data at the cost of being inaccessible unless we are physically on location. A VPN solves this dilemma. It can serve as a bridge to communicate remotely with the remote server. This communication is tunneled and encrypted. Only authorized users will be able to access it, enhancing productivity while maintaining high levels of confinement.
Enhanced Connectivity
A VPN is OS agnostic and not restricted by location. Therefore, it is one of the best methods to allow for remote operations between uses in a company. A VPN reduces the possibility of compromising communication integrity while promoting the positive culture of working remotely, which is essential nowadays.
Limitations and Disadvantages
Using a VPN regularly may have some small drawbacks and restrictions. We will be reviewing some of the most relevant in this article.
Performance
Workers using a VPN can slow the overall speed of the network and increase latency and software performance. For example, suppose a user is in San Francisco, connecting to a VPN server in New York while accessing a Salesforce software node based in Atlanta. In this case, latency will be a significant factor. How does this occur? The impact of performance degradation will depend on several factors, as seen below:
- The distance of the client to the VPN server.
- The distance from the VPN server to the destination server
- The encryption and decryption processes
- The number of concurrent users on the servers at any given point in time
Of course, a dependable VPN service provider will consider those problems when advising you on a solution. However, compared to a standard connection, the network speed will vary and rarely remain the same.
VPN Detection Services
Some ISP, content providers, and streaming services have anti-VPN software in place. These companies entirely block some protocols, and end-users are at risk of getting accounts banned using a low-quality VPN.
Activity Log
With all the advantages of using a VPN, most of them rely on the provider we choose. We need to ensure our activity is not being monitored or logged by the VPN provider as this information can later be sold to a third party, defeating the purpose of using a VPN service at all.
Untraceable
There are other disadvantages of using VPNs, such as the complex set up for non-managed services, inconsistent network connectivity, obscure provider policies, software compatibility. Even though a VPN adds a layer of protection, we might think we are completely anonymous, but there are ways to be targeted and tracked online. Luckily, there are up-to-date security practices that will make tracking that much harder.
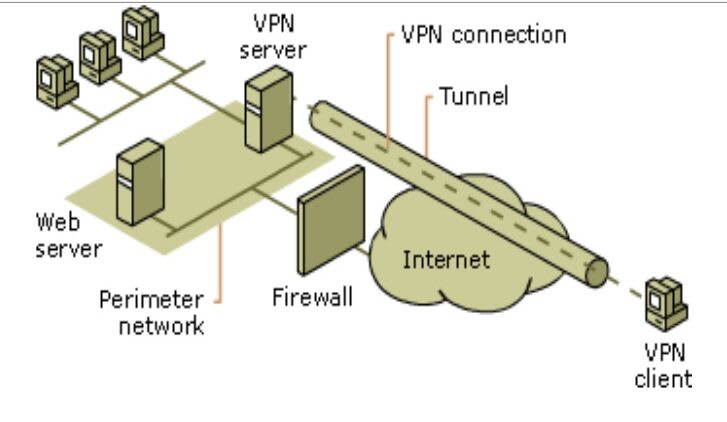
VPN Security
The interception of traffic has been a problem since the early days of the internet. Even more so now that enterprise users began to exploit this revolutionary technology. VPN usage has now become the focus of protecting intellectual property and sensitive data while still being able to transfer sensitive information as needed. A VPN (or virtual private network) is a technology that consists of creating tunneled private network connections between the VPN server and the end-user (VPN client). This virtual tunnel is encrypted using unique protocols when connecting over a public network.
VPN Protocols
One of the decisive characteristics of a VPN is the protocol used. These five primary protocols determine the encryption method, algorithms, and how to issue and verify encryption keys. We will provide an overview of the most common tunneling protocols that make this technology possible.
OpenVPN
OpenVPN is both a protocol and a software client. It is the most popular VPN software in this category. Because OpenVPN is an open-source protocol that uses AES-256 bit key encryption with a 2048-bit RSA authentication, it provides a robust and secure encryption algorithm. It is widely used and compatible with almost every platform. OpenVPN has a stable development history, a large support community, and independent auditors who approve of its open codebase.
Point to Point Tunneling Protocol (PPTP)
PPTP has existed since the dawn of VPN protocols. It has aged well in the context of fast-growing technologies. Originally developed by Microsoft for low-speed dial-up connections, PPTP is still relevant today because it provides the fastest connections. Unfortunately, this is due to the weaker encryption and security methods. The encryption techniques employed by PPTP are compromised and have fallen into disuse. PPTP is primarily limited to applications in which heavy encryption is not a significant factor.
Secure Socket Tunneling Protocol (SSTP)
This protocol was exclusively designed by Microsoft and released along with Windows Vista. Given that it only worked with Windows during launch, it never achieved much popularity. SSTP makes use of 2048-bit SSL/TLS certificates for the authentication process and SSL keys as an encryption method. Although SSTP is a reliable option, it has the typical constraints of any other proprietary software, such as lack of configurability, limited compatibility, etc.
Internet Key Exchange version 2 (IKEv2)
Cisco and Microsoft developed IKEv2 and has become one of the most popular VPNs protocols due to its focus on speed without compromising security. IKEv2 secures data at the IP level and supports 256-bit encryption along with the most modern ciphers (chacha20poly1305, camelia, AES, 3DES, etc.).
Layer 2 Tunnel Protocol / Internet Protocol Security (L2TP/IPSec)
L2TP is a significant improvement over PPTP, prioritizing security, and anonymization over speed. It is widely used alongside IPSec, which provides AES-256 encryption, making the combination robust in security.
Secure Your Network With a Liquid Web VPN
Setting up a VPN service with Liquid Web is easy. Our VPN service was designed with small to medium businesses in mind to provide our users with the latest security and encryption features. The advantages of our VPN service include:
- Fully Managed: You tell us what you need, and we manage the rest. We handle the security and infrastructure and provide the most helpful humans in hosting if you need assistance in troubleshooting your account.
- Available for Dedicated and Cloud Servers
- Scalability. No matter the size of your business, we have you covered.
- Enterprise Encryption and Security, even for the most sensitive environments.
- You do not need to worry about the network's state, as a primary goal is to keep critical systems online.
Want to Know More?
Interested? You can visit our VPN Products page to set one up in a few clicks. Alternatively, you can open a live chat with us or give us call us at 1-800-580-4985. Our technical support staff is always available to assist with any issues related to this article, 24 hours a day, 7 days a week 365 days a year.
Support is also available, via our ticketing systems by emailing us at support@liquidweb.com, by phone (at 800-580-4986) or via a LiveChat.
We work hard for you so you can relax!
Related Articles:

About the Author: Misael Ramirez
A former support technician, I have a degree in mechatronics; the career suited me because I'm always trying new things. I have a wide range of interests, but mainly I love music, movies (old ones), and physics.
Our Sales and Support teams are available 24 hours by phone or e-mail to assist.
Latest Articles
How to use kill commands in Linux
Read ArticleChange cPanel password from WebHost Manager (WHM)
Read ArticleChange cPanel password from WebHost Manager (WHM)
Read ArticleChange cPanel password from WebHost Manager (WHM)
Read ArticleChange the root password in WebHost Manager (WHM)
Read Article


