What is a virtual machine?
A virtual machine (VM) is a simulated computer system that runs within a physical computer. The physical device, called a host or parent server, houses the VMs called guest or child server instances. Virtual machines include the following components:
- Memory.
- A virtual CPU.
- Disk storage space.
- A network interface.
These components mean you can have a parent server running VMs with entirely different operating systems (OSs).
For example, a parent server running on Windows could run multiple virtual machines on Ubuntu Linux, macOS, Windows 10, Solaris, or CentOS operating systems. This feature is possible because all VMs are entirely separate from their parent machine.
Virtual machines work because the physical host distributes resources to the virtual environment (as in creating a virtual Python environment in Ubuntu 16.04). The resource distribution is customizable to fit each user’s needs. For example, users can set specific CPU usage or storage space limits on each virtual machine.
Usually, these settings are created and applied during the installation/setup of a virtual machine. An internal layer of software, known as the hypervisor, actually controls the resource allocation.
This process is called virtualization, and it allows users to run multiple virtual machines using the available resources of the parent OS. When a VM is not running, resources revert to your host machine (the physical server that hosts your VM). Therefore, your host machine can leverage these resources when your VM is powered down.
How Do Virtual Machines Work?
Virtual machines operate using virtualization technology. As mentioned earlier, these virtualization applications use specialty software (a hypervisor) to effectively create an isolated virtual space in which different operating systems run and separate resources are distributed to each VM. Meaning you could have multiple VMs running on your host server.
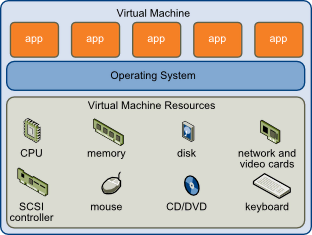
Each server instance with an operating system running under the host server is a guest VM. Since these guest VMs are isolated from the parent and other guest operating systems, any changes do not impact the system’s parent server or other VMs.
What is a Hypervisor?
A hypervisor is what makes the virtualization of a managed private cloud possible. It’s an internal software that controls the resources of the parent system. So answering the question “what is a virtual machine?” requires discussing hypervisors.
Think of it as a layer on top of the parent operating system or installed directly on the hardware. Its primary responsibility is to take the available resources on the parent server and distribute them to one or more VMs. The hypervisor also acts as a barrier between the host operating system and the virtual machines, effectively making it two completely separate entities on one physical device.
Types of Hypervisors
There are two main types of hypervisors:
- Bare Metal Hypervisors (process VMs), also known as Type-1 hypervisors.
- Hosted Hypervisors (system VMs), also known as Type-2 hypervisors.
The differences between the types of virtualization are not always crystal clear. For example, in the Linux host kernel, a module was introduced in 2007 that effectively modifies the host operating system to a Type-1 hypervisor. A Type-1 hypervisor is a hybrid that can be both hardware and software-based.
Bare-Metal Hypervisor (Process VM)
A bare metal or Type-1 hypervisor runs directly on the host’s hardware to control and manage the guest operating systems. Bare metal hypervisors are primarily used in enterprise environments, as they allow for the over-allocation of physical resources.
This over-allocation means a Type-1 hypervisor can designate additional resources, like memory, to a group of VMs. You may be wondering how you can add memory you don’t have available. Essentially, the hypervisor only allocates the RAM required for a VM to be fully-functional. While Liquid Web’s VMware Private Cloud solution does not allow over-allocation of RAM, it does allow for CPU core overcommitment.
One typical example of a Type-1 hypervisor is a Kernel-based virtual machine (KVM). KVM allows the kernel to function as a hypervisor running unmodified Linux or Windows images. Using KVM, users can run numerous virtual machines, each having its own disk space, graphics adapter, network card, etc.

Hosted Hypervisor (System VM)
A Hosted or Type-2 hypervisor will run inside the operating system of a physical host server, making it hosted. The main difference between Type-1 and Type-2 hypervisors is their platform. Type-1 hypervisors run on hardware, and Type-2 hypervisors run on software within the host operating system.
Type-2 hypervisors are commonly used in environments where fewer servers are needed. They don’t allow for the over-allocation of resources but use the total amount of assigned RAM. If too many virtual machines exist, it can crash the host machine.
Ease of management is a significant advantage of using a Type-2 hypervisor. The tasks of a Type-2 hypervisor happen on the host server, providing easy access to the host server’s management console. Since VMs created with a Type-1 hypervisor focus more on isolation, this type of flexibility isn’t possible.
The management console also allows for other features to be utilized like monitoring, snapshots, or creating templates with pre-installed applications. The Liquid Web Support Team can help configure these templates to automatically be deployed on VMware.
Defining Virtualization
So, what is VM virtualization? Virtualization is the process of running one or more virtual machines (VMs) inside a server. The idea of virtualization was introduced in the 1960s. Systems analysts at that time were looking for ways to logically divide the system resources between different applications inside a mainframe computer.
Today, modern computers and servers have significantly more processing power and storage space. Nevertheless, most servers don’t optimize the use of these resources.
Virtualization technology helps to prevent the improper utilization of these resources. The multiple virtual machines created can run from a single hardware unit or server. The cloud is an example of how virtualization can improve resource utilization and processing power. A managed private cloud can leverage virtualization to distribute resources and make computing very cost-efficient.

There are three main types of server virtualization. Let’s take an in-depth look at each one down below.
Full Virtualization
The idea behind full virtualization is that a virtual machine is completely isolated from the guest OS. The VM will simulate the hardware but is completely disconnected from the actual hardware by a virtualization layer.
A few typical examples of full virtualization seen today are:
- KVM.
- VMware Fusion.
- Microsoft Virtual PC.
- VirtualBox.
Hardware-Assisted Virtualization
Hardware-Assisted Virtualization uses the host’s physical devices to support the software which creates and manages the virtual machines. This method allows VMs to execute privileged instructions directly on the parent processor without affecting the host. The type of hypervisor used is a crucial component of this kind of virtualization.
OS-Level Virtualization
In this type of virtualization, the kernel of an OS allows for numerous, separate user-space instances. This kernel-based virtualization module enables these VM instances to run over an existing host operating system.
What makes this type of virtualization effective is that it occurs at the machine level. OS-level virtualization can create isolated partitions on a single physical server. Each of these instances works independently of the others but share the same physical resources available on the host server. Naturally, this can limit the amount of resources available to each virtual machine.
Each instance type has multiple names depending on the OS itself. Some common names are containers, virtual private servers, or virtual environments (such as virtualizing python on Ubuntu 18.04). OS-level virtualization is commonly used in general hosting and VPS hosting.
What is the Difference Between VMs and Containers?
One of the main differences between virtualization vs containerization is their relationship to the parent operating system. Containers run on the underlying operating system while VMs have their own operating system using hardware VM support. Hypervisors manage VMs while a container system will provide services from the underlying host OS and isolate the applications using virtual memory hardware.
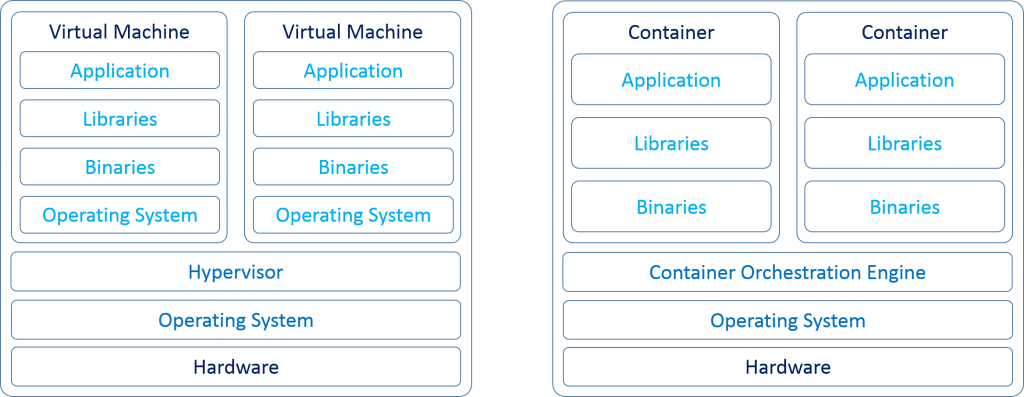
Essentially, a VM will use its hypervisor to virtualize its necessary hardware. On the other hand, the container works by virtualizing the operating system.
Containers are generally smaller and don’t have built-in operating systems like VMs. They thrive in environments where they are used for specific tasks. An example would be testing a software application throughout the development process.
If you’re wondering what is a virtual machine compared to a container, a VM acts as a more authentic version of a mini-computer. VMs can mimic entire servers, networks, databases, etc. Any resources necessary to process complex computing tasks are found within each VM partition on the parent server.
Why Use a Virtual Machine?
| Advantages | Disadvantages |
| Flexibility | Less Productive |
| Hardware Cost | Resource Consumption |
| Control | Security |
| Disaster Recovery |
Advantages
Flexibility
Virtualization allows the rapid deployment of different kinds of virtual machines. All of them are customizable in terms of the operating system and resource utilization. Most, if not all, hypervisor vendors will also allow us to create specific templates that can be deployed simply by the click of a button.
For example, imagine a parent server hosting several virtual machines. If one gets infected with malware, the recovery process would be simple. The virus attack is isolated to only the affected VM, and you could redeploy the VM with all the same software already installed.
This ease of redeployment models the importance of knowing what a VM template is. They can be valuable tools. For example, deploying the VM from a template allows users to minimize the damage caused by malware attacks. Templates also save time in setting up new machines.
Hardware Cost
IT hardware costs can be a challenge for any business. While virtual machines may still need power and software licensing, VMs are a much more cost-effective solution. The usage of virtual machine resources is much more controllable. These resources can be limited and allocated with much more precision than systems requiring multiple hardware endpoints.
Control
Again, virtual machines run via a centralized management scheme which allows for rapid deployment and control from a single point. This is much more efficient than managing multiple workstations, particularly when workstations are spread across various locations.
Disaster Recovery
There is little risk of data loss due to hardware failure since virtual machines make regular backups. Everything can be redeployed quickly and easily, saving valuable time to recover and redeploy the VM. The recovery ability of virtual machines is bolstered even more by using virtualization templates.
Disadvantages
Less Productive
Virtual machines can be less efficient than dedicated servers since they do not access hardware directly. In other words, they do not have hardware of their own but must rely on communication through the operating system, which can slow down response time from the parent hardware (known as latency).
Resource Consumption
VMs can take up a significant amount of system resources from the host. Resource depletion only increases as more VMs are added.
Additionally, if resource distribution is not set up correctly, the host and all other VMs within the system can crash.
Security
IT experts challenge the assertion that VMs have any security drawbacks since VMs exist in isolation from the rest of the operating system. But, the fact remains that they are still a software platform and are always subject to vulnerabilities and attacks by their very nature.
An effective malware attack can potentially jeopardize the security of a VM. If an attacker can infiltrate to the hypervisor level, all the virtual instances could be in jeopardy. In such situations, if sufficient fail-safes aren’t in place, there could be no way of knowing that your VMs are compromised. This type of scenario could be devastating to a large-scale virtualization operation running hundreds or thousands of virtual machines.
Wrapping Up
What is a virtual machine? These mini-computers are a more cost-effective solution that allows control of an IT environment’s entire workflow and efficiently distributes resources.
Many virtualization applications exist, from cloud computing to simply testing a new operating system. With the future of computers in the cloud, virtual machines will eventually become necessary to optimize your IT estate’s efficiency.
While both containers and VMs have pros and cons, the best choice for your business depends on your current project needs. However, both can be outstanding solutions to better cost-effective computing.
If you haven’t made the jump into virtualization in your own business, let us help. Consider talking to our Solutions team at Liquid Web about our dedicated virtual server hosting or other services.If this article answers the question “what is VMware?” for you, and you think it’s the right choice for your business, our VMware Private Cloud solution is the perfect framework to help you take your company’s digital assets to the next level. Contact our sales team today for an evaluation call.
 Danny Jensen
Danny Jensen