Top 10 Web Server Security Best Practices
How Can You Ensure Security on a Server?
It is important to secure your server to prevent data loss or security compromises. Because security is such a challenging subject for many, it often goes unheeded. Many are caught unaware when an issue arises. By following these best practices, you can significantly lower your risk of being compromised by a malicious actor.
Server Security Best Practices
1. Server Management
Proper server management ensures all activity continues to meet organizational standards and maintains peak server operations performance. This includes hiring qualified system administrators and implementing physical and internal security measures.
2. Physical Security
Implementing physical security controls helps prevent unauthorized personnel from physically accessing components such as routers, wiring closets, and servers. Controlled access via physical access control (PAC), such as locks, biometric authentication, and other devices like badges, is essential in any organization.
Traditional doors and locks are the most basic form of a physical access control system, but enterprise-grade physical access control systems go much further. Access controls may be more stringent in certain areas of a building, such as organizations that have public access areas and restricted access areas.
Maintaining the credential database and deleting any deactivated users is a security best practice. Also, adding different kinds of PACs is a good formula for more secure control of physical access to vulnerable or essential departments in a business.
3. Update Software and Operating Systems
Maintaining an updating cycle on software and operating systems (OS) is the single most significant security precaution you can take for your server. Updates range from critical vulnerability patches to minor bug fixes. Many software vulnerabilities are patched when they become public, adding to the urgency with which users should install updates.
Since server systems tend to have a complex relationship with software environments, faults can go unnoticed. Failing to maintain your operating system and any other software on your server up to date will inevitably expose it to common vulnerabilities. Businesses must plan to execute regular updates and patches within a reasonable amount of time to maintain security.
4. Secure Connections
SSH
When command line (terminal) access to the server is needed, utilize a secure shell (SSH) connection. SSH creates a secure pipe for data travel. This connection secures only the information sent through the terminal from the computer to the server.
Something else to consider is the SSH port. The SSH default port is #22. Best practice suggests avoiding this port and using a port range of 32768 to 61000 for extra integrity. This change prevents automated attacks on the connection and primary hacking radars.
SSH Keys
Instead of an SSH password for accessing the server, use an SSH key instead. They disable the SSH feature necessary to access the server as the root user, eliminating the need to use a root password. It provides an additional layer of security when connecting to the server than using a password alone.
Using SSH keys also allows us to create a cryptographically secure keypair that stores unique connection information locally on your computer and the server. Because SSH key pairs generate cryptographically, the larger the key size is, the more secure it is.
A proxy server is an option as an additional security measure since they hide any network users behind the proxy's IP address and host firewalls. This setup makes it more difficult for hackers to target specific devices for access.
Multi-Factor Authentication (MFA)
SSH keys are mainly a single-factor authentication method. A two or multi-factor authentication would require the user to give out different kinds of information (phone number, email, government ID) to access sensitive data.
VPN
A virtual private network (VPN) is a private connection to a local, private network from a remote location. It ensures private data remains secured and maintains the confidentiality and integrity of that information. A VPN grants privacy and protection in online communications and browsing, making the connection between your equipment and the Internet confidential.
Fail2Ban
Fail2ban is a server software that prevents intruders by penalizing or blocking remote connections that attempt brute-force access. It allows you to monitor the impact and frequency of attacks, and updates to firewall rules are issued to block suspect IP addresses for a specified time. Fail2Ban can monitor several protocols, including HTTP, SSH, and SMTP. By default, Fail2Ban only monitors SSH but is a helpful security deterrent for any server.
SSL/TLS
Another effective safeguard is server security certificates, such as Secure Sockets Layer (SSL) and Transport Layer Security (TLS). These security certificates are cryptographic protocols for authentication and encryption, with TLS being a newer version of SSL. TLS fixes some security vulnerabilities in older SSL protocols, and these certificates are required for user authentication.
Server security certificates protect network communications by scrambling sensitive data sent over the internet, such as passwords, usernames, and credit card information, allowing servers to validate entities.
Restricting Root Access
SSH should be restricted to a limited subset of users. To do this, add the following information to the /etc/ssh/sshd_config file.
PermitRootLogin no
Protocol 2Then, add the SSH users group to the /etc/ssh/sshd_config file.
AllowGroups sshusers5. Disable Unnecessary Services
Audit Services
Service auditing explores what services are actively running on the server, the protocols they are using, and the ports with which they interact. Being conscious of these factors will help lessen any attack vectors in the system.
Most servers come with certain services enabled by default, allowing you to use multiple features available on the server. If these extra services are not in use, it is best to disable them. Running specific commands on a Red Hat-based system helps you find and disable unnecessary services.
Red Hat/CentOS Enabled Services
To view the enabled services in Red Hat or CentOS, run the following command.
systemctl list-unit-files | grep enabledThis is the output.
[root@host ~]# systemctl list-unit-files | grep enabled
var-lib-snapd-snap-core-7917.mount enabled
var-lib-snapd-snap-hello\x2dworld-29.mount enabled
var-lib-snapd-snap-snapcraft-3440.mount enabled
acpid.service enabled
auditd.service enabled
autovt@.service enabled
crond.service enabled
dbus-org.fedoraproject.FirewallD1.service enabled
firewalld.service enabled
getty@.service enabled
irqbalance.service enabled
microcode.service enabled
NetworkManager-wait-online.service enabled
postfix.service enabled
qemu-guest-agent.service enabled
rhel-autorelabel.service enabled
rhel-configure.service enabled
rhel-dmesg.service enabled
rhel-domainname.service enabled
rhel-import-state.service enabled
rhel-loadmodules.service enabled
rhel-readonly.service enabled
rsyslog.service enabled
sonarpush.service enabled
sshd.service enabled
systemd-readahead-collect.service enabled
systemd-readahead-drop.service enabled
systemd-readahead-replay.service enabled
tuned.service enabled
snapd.socket enabled
default.target enabled
multi-user.target enabled
remote-fs.target enabled
runlevel2.target enabled
runlevel3.target enabled
runlevel4.target enabled
[root@host ~]#The following command shows the running services.
systemctl | grep runningThe output is as follows.
[root@host ~]# systemctl | grep running
session-2969.scope loaded active running Session 2969 of user root
acpid.service loaded active running ACPI Event Daemon
auditd.service loaded active running Security Auditing Service
crond.service loaded active running Command Scheduler
dbus.service loaded active running D-Bus System Message Bus
firewalld.service loaded active running firewalld - dynamic firewall daemon
getty@tty1.service loaded active running Getty on tty1
irqbalance.service loaded active running irqbalance daemon
polkit.service loaded active running Authorization Manager
postfix.service loaded active running Postfix Mail Transport Agent
rsyslog.service loaded active running System Logging Service
serial-getty@ttyS0.service loaded active running Storm management console on Serial Getty ttyS0
snapd.service loaded active running Snappy daemon
sonarpush.service loaded active running LiquidWeb Sonarpush Monitoring Agent
sshd.service loaded active running OpenSSH server daemon
systemd-journald.service loaded active running Journal Service
systemd-logind.service loaded active running Login Service
systemd-udevd.service loaded active running udev Kernel Device Manager
tuned.service loaded active running Dynamic System Tuning Daemon
dbus.socket loaded active running D-Bus System Message Bus Socket
snapd.socket loaded active running Socket activation for snappy daemon
systemd-journald.socket loaded active running Journal Socket
systemd-udevd-control.socket loaded active running udev Control Socket
systemd-udevd-kernel.socket loaded active running udev Kernel Socket
[root@host ~]#To disable a service, such as Bluetooth, use this command.
systemctl disable bluetoothDebian/Ubuntu Running Services
The following command shows you the running services on a Debian or Ubuntu-based server.
service --status-all |grep '+'Here is the output.
root@host ~# service --status-all |grep '+'
[ + ] apache-htcacheclean
[ + ] apache2
[ + ] apparmor
[ + ] apport
[ + ] atd
[ + ] binfmt-support
[ + ] cron
[ + ] dbus
[ + ] ebtables
[ + ] grub-common
[ + ] irqbalance
[ + ] iscsid
[ + ] lvm2-lvmetad
[ + ] lvm2-lvmpolld
[ + ] lxcfs
[ + ] procps
[ + ] rsyslog
[ + ] ssh
[ + ] udev
[ + ] ufw
[ + ] unattended-upgrades
root@host ~#This command lists the state of the services regulated by systemV. The plus (+) and minus (-) symbols indicate whether the service is active.
systemctl | grep runningThe following shows the output.
root@host ~# systemctl | grep running
proc-sys-fs-binfmt_misc.automount loaded active running Arbitrary Executable File Formats File System Automount Point
init.scope loaded active running System and Service Manager
session-1726.scope loaded active running Session 1726 of user root
accounts-daemon.service loaded active running Accounts Service
apache2.service loaded active running The Apache HTTP Server
atd.service loaded active running Deferred execution scheduler
cron.service loaded active running Regular background program processing daemon
dbus.service loaded active running D-Bus System Message Bus
getty@tty1.service loaded active running Getty on tty1
irqbalance.service loaded active running irqbalance daemon
lvm2-lvmetad.service loaded active running LVM2 metadata daemon
lxcfs.service loaded active running FUSE filesystem for LXC
networkd-dispatcher.service loaded active running Dispatcher daemon for systemd-networkd
polkit.service loaded active running Authorization Manager
rsyslog.service loaded active running System Logging Service
serial-getty@ttyS0.service loaded active running Storm management console on Serial Getty ttyS0
snapd.service loaded active running Snappy daemon
ssh.service loaded active running OpenBSD Secure Shell server
systemd-journald.service loaded active running Journal Service
systemd-logind.service loaded active running Login Service
systemd-networkd.service loaded active running Network Service
systemd-resolved.service loaded active running Network Name Resolution
systemd-timesyncd.service loaded active running Network Time Synchronization
systemd-udevd.service loaded active running udev Kernel Device Manager
unattended-upgrades.service loaded active running Unattended Upgrades Shutdown
user@0.service loaded active running User Manager for UID 0
dbus.socket loaded active running D-Bus System Message Bus Socket
lvm2-lvmetad.socket loaded active running LVM2 metadata daemon socket
snapd.socket loaded active running Socket activation for snappy daemon
syslog.socket loaded active running Syslog Socket
systemd-journald-audit.socket loaded active running Journal Audit Socket
systemd-journald-dev-log.socket loaded active running Journal Socket (/dev/log)
systemd-journald.socket loaded active running Journal Socket
systemd-udevd-control.socket loaded active running udev Control Socket
systemd-udevd-kernel.socket loaded active running udev Kernel Socket
root@host ~#To disable a service, use the following command.
systemctl disable apacheRemove X Windows From the System.
The X Window System (also called X11, or just X) is a windowing system for bitmap displays, standard on Unix-like OSs. It provides a basic framework for a windowed graphical user interface (GUI) environment. The X Windows system included in CentOS, Red Hat Enterprise Linux (RHEL), and Fedora Linux is called X.org.
Most servers do not require a GUI for general server administration tasks, while others use a management panel. It is helpful to know how many open paths there are to the server and only enable the ones you need. It is good to remove X Windows if it comes installed and your server does not require it.
Use this command to remove the X Windows system.
yum groupremove "X Window System"6. Keep Backups
Losing critical information can be catastrophic for any business. Luckily, numerous reliable backup solutions are available, including server backup software that can support both physical and virtual servers.
Liquid Web offers multiple options for backups. Some tools allow you to quickly perform and automate backups and recovery rates and easily monitor backup profiles to avoid data loss. When putting together your backup plan, the best practice is using the 3-2-1 rule of backup retention.
The 3-2-1 Rule

Three: Create three copies of your data. These copies should consist of one primary copy and two backups.
Two: Store the copies of your data on at least two different types of storage media. You may store one copy on your local hard drive and another on an external drive, network-attached storage (NAS), or a locally kept storage server.
One: Store one data copy offsite. This option can be a storage server held at another location or a cloud storage solution with a hosting provider.
7. User Management
Monitor Login Attempts
Host intrusion detection systems (HIDS) is a type of application that monitors devices and networks for suspicious activity. It examines accessed files, used applications, and data in the kernel logs.
Network intrusion detection systems (NIDS) is an application that monitors network traffic for suspicious activity. It evaluates the flow of data between devices within a network.
HIDS are used for a more well-rounded solution, and NDIS is used for a local area network (LAN) based solution.
Here is a list of HIDS:
- OSSEC
- Wazuh (A fork of OSSEC that offers more reliability and scalability)
- Tripwire
- Samhain
- Security Onion
NIDS and HIDS can be used in conjunction to form a solid and comprehensive intrusion detection system strategy. Some recommendations include:
Limit User Permissions
To ensure only the needed users have access to critical systems, limit the permission sets they have to 644 or 444 for files and 755 for folders.
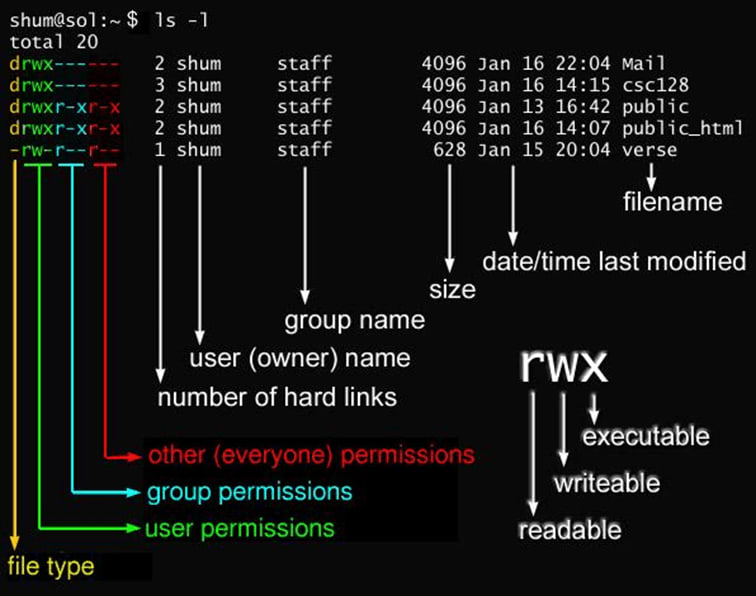
Perform User Testing
Set a specific date to perform a security audit and inform users before it comes. Define your expectations and hold them accountable for any noted deficiencies.
Ongoing Security Training
Send out monthly reminders and do training every three months, with six-month dry runs across multiple areas (email, network, and physical), and track failures to improve and add additional training in those areas.
Travel Security
Security does not just end at the front door of your business. Setting up security parameter training for employees traveling abroad is a wise choice in today's world, even more so now with many companies going fully remote or scheduling remote weeks for some departments.
8. Use SELinux
SELinux is a kernel-based security module that provides a mechanism for supporting access control security policies, including mandatory access controls (MAC). It is primarily used as a means to adjust access control requirements.
With SELinux, you can designate what a process or user can do. It can limit operations to their domain, so actions can only interact from allowed domains with certain file types or other processes.
SELinux can exist in any of these three possible modes:
- Enforcing - SELinux actively enforces the defined policy.
- Permissive - Mainly used for testing. Enforcement is not applied but is logged.
- Disabled - The system is inactive.
9. Awareness and Education
Essential things go unnoticed if you don't know what to look for or the questions to ask. While you don’t need to be a security expert to be protected, you must be aware of the dangers that seek to harm your business.
A common misconception is that a fully managed server offering is all the security you need. However, hosting providers work with you and your team to ensure your environment’s security. The hosting provider ensures that the hardware, network, and facilities are secure, but your data is your responsibility. You and your team must educate yourselves on common security issues and how to keep your websites and applications secure from them.
10. Securing the Filesystem
There are several steps to secure the server filesystem. For starters, always mount filesystems with user-writable directories on separate partitions. Also, use nosuid, nodev, and noexec in the /etc/fstab file using the text editor of your choice.
Here are some additional settings to be aware of:
Set /boot to Read-Only
Ensure that the /boot folder is set to RW mode by default, despite only being used for reading or loading modules and the kernel. Use the following command to accomplish this.
/dev/sda1 /boot ext2 defaults ro 1 2Also, set /boot to read-only in the /etc/fstab file.
Disable Booting From Removable Media
This setting is optional, depending on your server use. To disable booting from removable media, you will need to modify the bios setting to disable booting from removable media like a USB stick.
Set a GRUB Bootloader Password
If someone has physical access to the server, they can get into it. Another wall between an attacker and server access is setting a password on the GRUB bootloader. You can accomplish this by setting up a password to limit access. First, backup the current grub.conf file.
root@host ~# cp /etc/grub.conf /etc/grub.conf.bakNext, generate a secure password. Create a file, then create the password using the grub-md5-crypt command. You will then be prompted twice to enter a password. Then, copy the created password from the secure file into the grub.conf file.
root@host ~# touch secure
root@host ~# grub-md5-crypt > secureAfter this, copy the password and paste it into the grub.conf file after the first line (in RedHat), as shown below. Then, save and exit the file.
splashimage=(hd0,0)/grub/splash.xpm.gz
password --md5 JnK!xdBep53lt1NVk@K6wb!js%!HEI#^You will need to reboot the server for the changes to take effect.
Prompt For Root Password Before Entering Single-User Mode
If a malicious actor has physical access to the server, they can select a specific kernel to boot into from the GRUB menu item by pressing the e key. This action allows someone to edit the first boot option to enable booting into single-user mode without being asked for a password.
Your system should be configured to prompt for the root password before entering single-user mode to limit possible exploitation. Following the instructions outlined in the Set a GRUB Bootloader Password section accomplishes this task.
Final Thoughts
Security is a shared concern. Follow these server security best practices and partner with your hosting provider. All of this gives your server environment the security it needs to flourish.
While this article helps with your end of the security bargain, finding a reliable hosting provider is another challenge. The Most Helpful Humans In Hosting® at Liquid Web offer industry-leading support for your hosting environment. Contact our sales team and get started today if you have not looked at our managed hosting options.
Related Articles:

About the Author: Michael Flores Feliz
Michael Flores Feliz is a Linux Technician at Liquid Web and an up-and-coming DevOPs engineer. He is also a big car fanatic. His motto is long live Linux and Linux support.
Our Sales and Support teams are available 24 hours by phone or e-mail to assist.
Latest Articles
In-place CentOS 7 upgrades
Read ArticleHow to use kill commands in Linux
Read ArticleChange cPanel password from WebHost Manager (WHM)
Read ArticleChange cPanel password from WebHost Manager (WHM)
Read ArticleChange the root password in WebHost Manager (WHM)
Read Article


