Enterprise network security: 10 best practices to secure your enterprise network
The average cost of a data breach in 2023 was $4.45 million. That’s a 15% increase from 2020 and a concerning trend for enterprises since they have extensive networks that are highly targeted.
That’s part of the reason enterprises are investing heavily in network security. A 2022 security spending benchmark report shows that companies in tech and business services spent 13% of their IT budget on cybersecurity.
Strengthening an enterprise’s network security isn’t straightforward, however. There’s software to monitor, hardware to secure, customers and vendors connecting through public networks, and employees to teach and surveil.
This guide covers all these factors, including practical steps you can take. First, let’s explore the significance of network security, and then we’ll explain enterprise network security best practices.
In full, here’s what you’ll learn:
The benefits of enterprise network security
Enterprise network security refers to processes and policies that increase the security of data, accounts, endpoint devices, and servers related to an enterprise network.
Enterprises need tight security because a breach can lead to sensitive data leaks, data held for ransom, and the destruction of business-critical data or programs. That’s not the only reason, though. Consider the following motivations.
Compliance
Enterprises must comply with data security regulations applicable to their operating regions. Network security practices are undoubtedly crucial to prevent cyberattacks, which can expose sensitive data like customers’ personal and financial information. This, in turn, exposes enterprises to legal backlash.
Business continuity
A hacker can hold data for ransom or bring down an enterprise’s network entirely. This could jeopardize the company’s day-to-day operations. Cybersecurity is, therefore, essential to ensure the enterprise has a reliable uptime.
Consumer trust
Cyberattacks often aim to compromise user data, like passwords and personally identifiable information. Consumers usually lose trust in a company that leaks their sensitive data. Consequently, this impacts the enterprise’s customer retention and acquisition.
The major security threats to enterprises
Enterprises with complex networks often face distinct security threats. Keep reading to get familiar with the important ones.
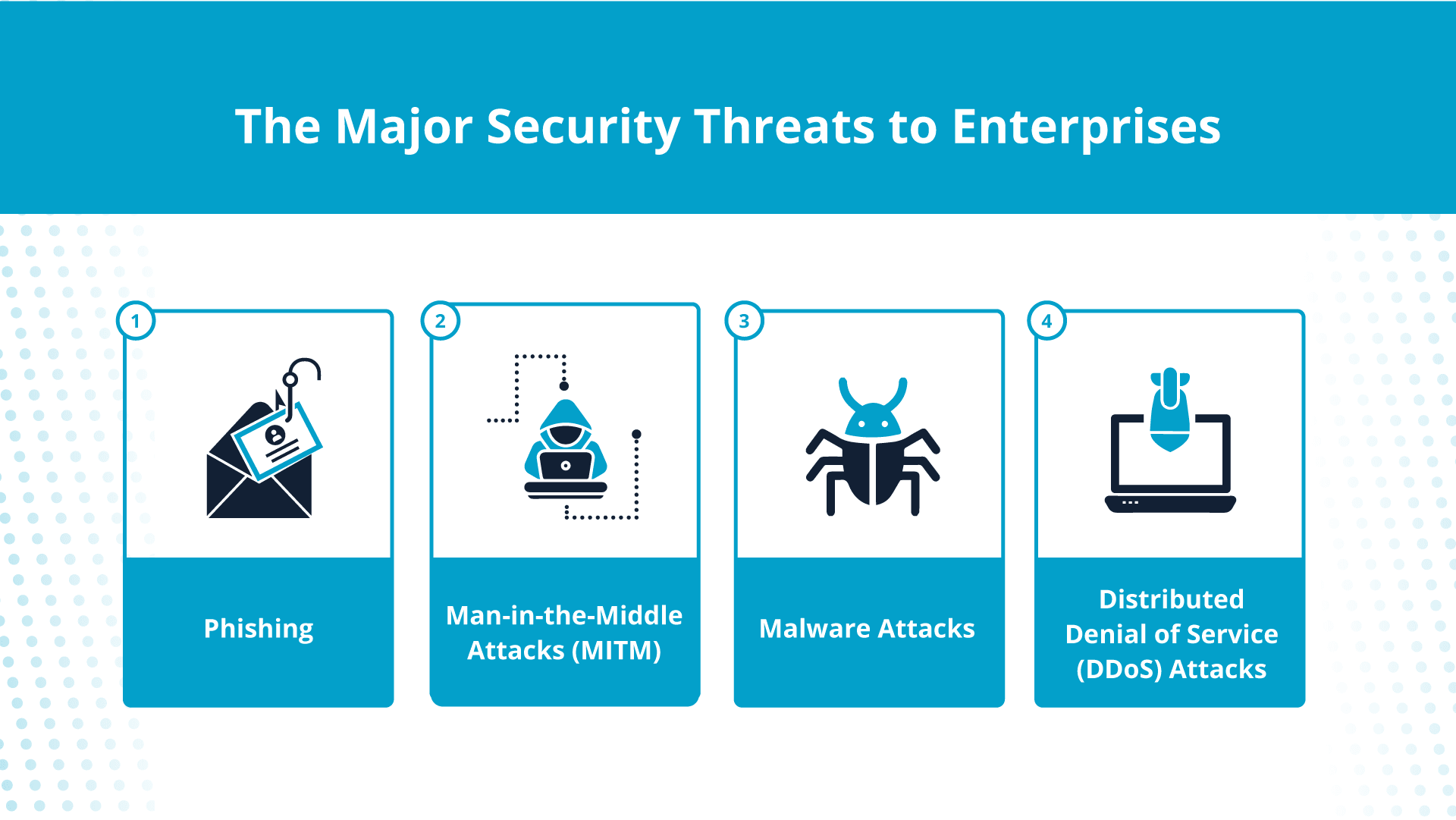
Phishing
Phishing involves an attacker sending someone an email or message disguised as legitimate communication from a trusted sender. It’s a form of social engineering, which means the attacker manipulates or deceives the victim into compromising network security by:
- Downloading malware.
- Clicking on malicious links.
- Sharing sensitive information.
In 2022, phishing was the most prevalent cybercrime, accounting for 53.2% of cyberattacks worldwide.
Spam filters can filter out phishing emails to some extent. However, sophisticated phishing attacks are hard to detect by automated systems and need trained humans to identify them.
Man-in-the-middle (MITM) attacks
In an MITM attack, hackers hijack a server and client communication. They use packet sniffer or modifier tools to intercept data between the two endpoints.
Often, MITM attackers aim to read sensitive data or modify it to include malicious content. The attacker does this quietly with neither the client nor the server detecting an issue.
MITM attacks often happen due to vulnerabilities like a lack of Secure Sockets Layer (SSL) or Transport Layer Security (TLS) protocols. For the strongest protection against MITM attacks, avoid using websites that don’t adhere to HTTPS or SSL protocols.
Malware
Malware is malicious software that can damage an enterprise network and extract confidential information. Here are a few common types of malware:
- Ransomware: Locks the enterprise network and denies access until the victim pays a ransom.
- Spyware: Hides in the enterprise network, eavesdrops on communications, extracts data, and sends it to the attacker.
- Trojan: Mimics legitimate code until the hacker is ready to launch a malicious attack.
- Worm: Replicates quickly and spreads through the enterprise network, overloading servers, consuming bandwidth, and slowing down operations.
Distributed denial of service (DDoS) attacks
In a DDoS attack, the attacker sends a massive volume of traffic into network devices like routers and servers. This flood of traffic overloads the enterprise network, leading to downtime and lost revenue while the servers are unavailable.
DDoS attacks can also be a way to camouflage a malware attack. The malware enters the network through the flood, undetected.
Significantly, there was a tenfold increase in DDOS attacks from 2005 to 2022, making it a top priority to address with best practices for enterprise network security.
Insider threats
A network security threat can originate from within an enterprise. An employee or a third-party vendor could intentionally or unintentionally assist in a malicious attack. A lack of network security awareness could play a role — but don’t rule out an intentional scheme.
In a 2023 survey of 2,300 cybersecurity professionals, 68% were concerned about insider threats.
You now understand how a network security breach can originate and affect both an enterprise’s operations and reputation.
Now, let’s explore some best practices that strengthen an enterprise’s network security and ability to prevent, detect, and respond to attacks.
Enterprise network security best practices
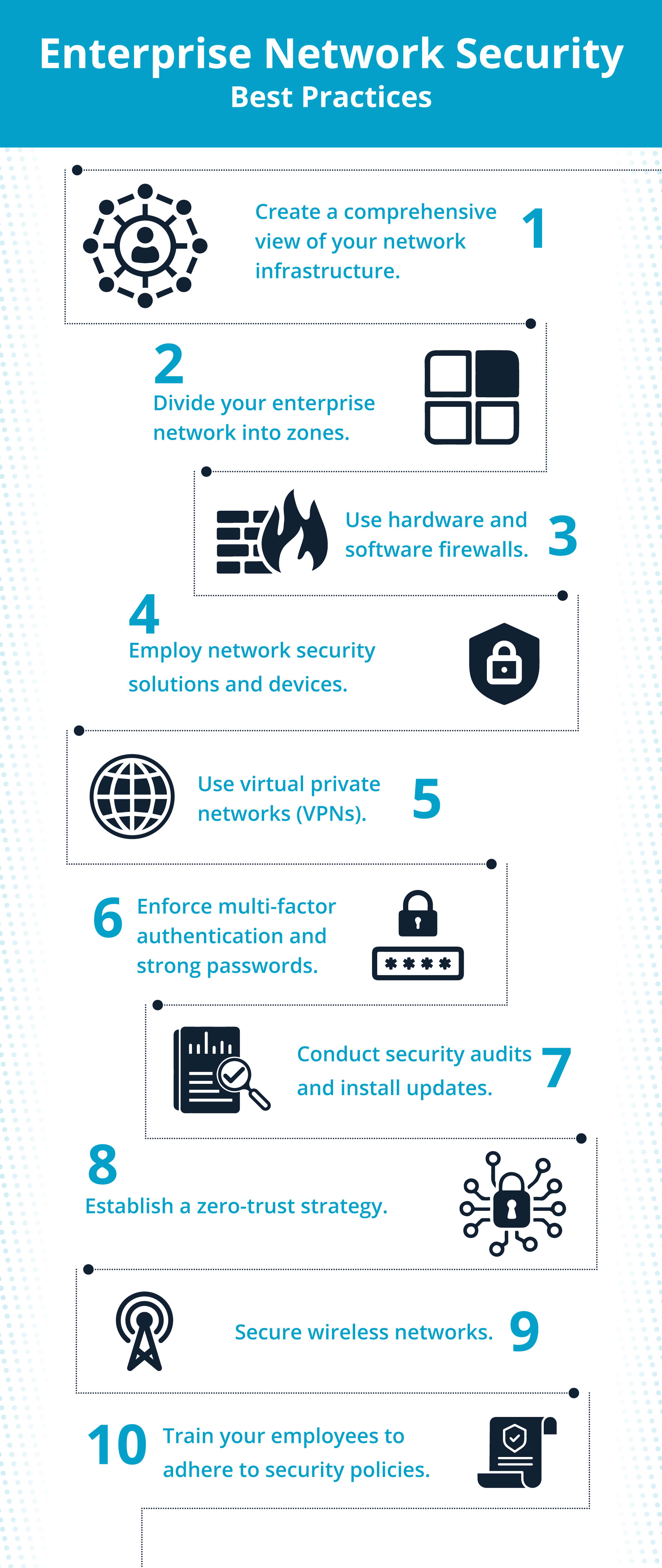
- Create a comprehensive view of your network infrastructure.
- Divide your enterprise network into zones.
- Use both hardware and software firewalls.
- Employ network security solutions.
- Secure wireless networks.
- Use virtual private networks (VPNs).
- Enforce both multi-factor authentication (MFA) and strong passwords.
- Establish a zero-trust strategy.
- Train your employees to adhere to security policies.
- Conduct security audits and install updates.
Take a closer look at each of these network security best practices.
1. Create a comprehensive view of your network infrastructure
Enterprises often have their data and applications spread across multiple servers, accessed through public and private networks. Therefore, the first step in enterprise network security is to gain a comprehensive understanding of your network infrastructure.
Start with the following components:
- Hardware: Routers, hubs, switches, and firewalls.
- Software: Intrusion prevention systems and network access control systems.
- Endpoints: Desktops, laptops, and mobile phones.
It’s a good idea to create a network diagram that shows how network devices and endpoints are interconnected. The depiction will put into perspective how many local area networks (LANs), wireless networks, and wide area networks (WANs) are critical to your enterprise.
When you have a solid big-picture understanding, your decision-making improves.
2. Divide your enterprise network into zones
Divide a huge enterprise network into logical zones. Each zone should segregate the network based on the information included and who needs access. For example, create separate zones for each department — or each local area, like floors.
After segmentation, configure firewalls between zones. A firewall is a device or software that moderates traffic in and out of a network.
Network segmentation makes a hacker’s work painstaking, as they must attack each zone, and jumping from zone to zone isn’t easy. If a network zone is under attack, you can disconnect it from other zones to isolate the threat.
3. Use both hardware and software firewalls
Firewalls often come as standalone network devices you place between your enterprises’ network zones.
The firewall will analyze the data transfer between these zones and restrict malicious or sensitive data packets. Most routers and switches have built-in firewalls, so it's good practice to double-check they’re configured correctly.
While the enterprise firewall can prevent threats from outside, software firewalls protect endpoints from any internal threats. Enterprise cybersecurity teams should enforce software firewalls on each network endpoint, like laptops, desktops, servers, and mobile devices.
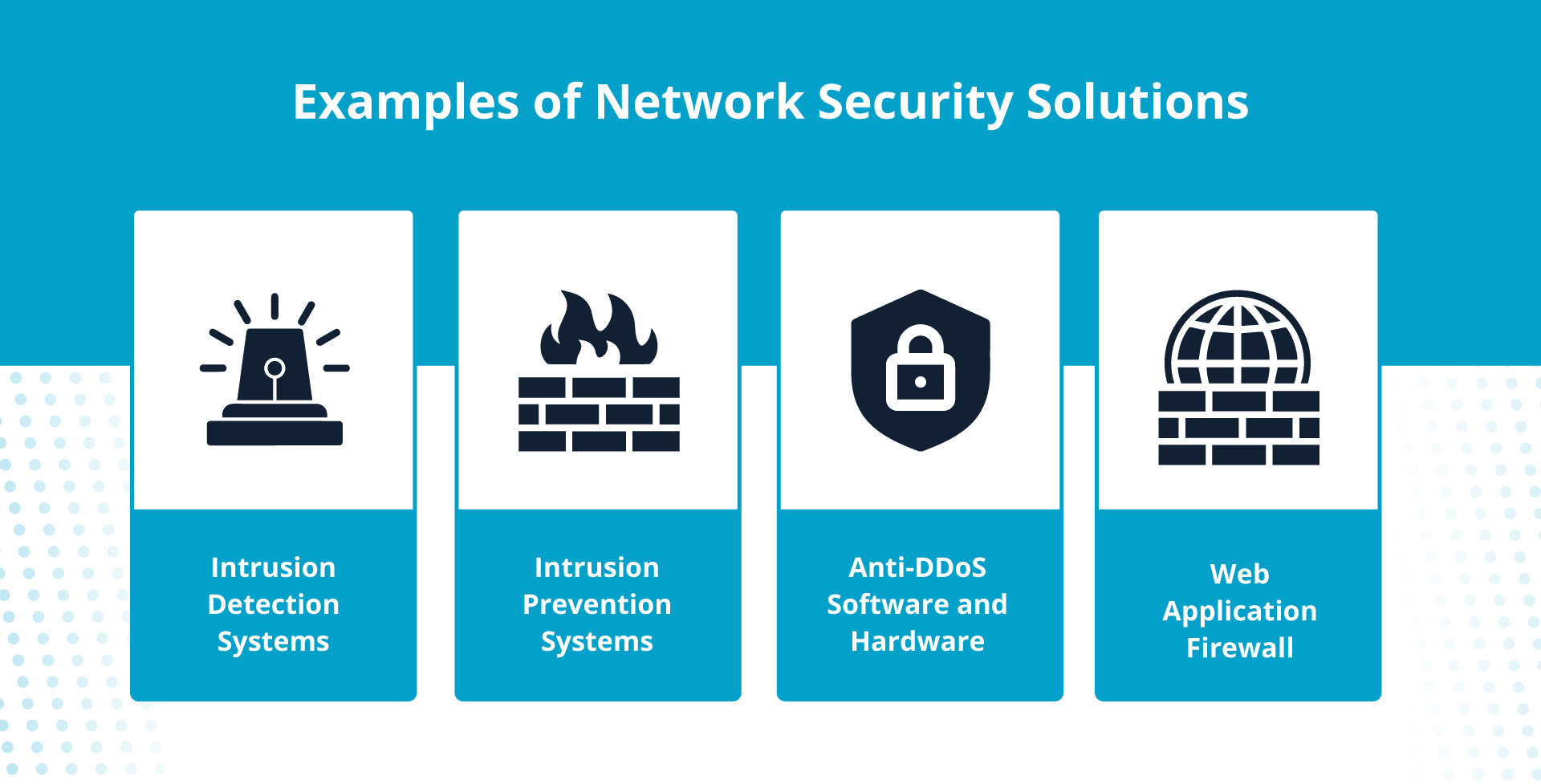
4. Employ network security solutions
Certain security devices and applications will help thwart cyberattacks.
Intrusion detection and prevention systems
An intrusion detection system (IDS) identifies malicious attacks on your network. An intrusion prevention system (IPS) is similar, with the extra function of preventing the attack.
An IDS will compare cyber activities with attack signatures — the characteristic features of a cyberattack — and flag abnormal online activity like the following:
- Unauthorized file transfers.
- Changes in administrative privileges.
- Suspicious network speed decreases.
On the other hand, an IPS is a machine learning system that automates threat detection and prevention.
Anti-DDoS software and hardware
Anti-DDoS programs monitor your network traffic, filter out suspicious data packets, and block malicious server requests; this prevents volume-based cyberattacks while allowing legitimate requests to reach your server.
Usually, anti-DDoS software has a price tag, but Liquid Web hosting includes DDoS protection at no extra cost.
Web application firewall (WAF)
In addition to an enterprise firewall, use a web application firewall to protect your business from attacks that target web applications, such as:
- SQL injection: Injecting malicious SQL code into a database.
- Cross-site scripting: Injecting harmful scripts into a trusted website.
- Cookie poisoning: Forging or manipulating a cookie to access a user’s account.
A WAF will monitor the traffic between your web application and a client. It analyzes the data packets to filter out anything suspicious.
5. Secure wireless networks
Wireless networks introduce more security challenges than wired networks. Wireless access points are vulnerable to unauthorized access, which leaves room for hackers to:
- Packet sniff to intercept unencrypted data.
- Remotely access your enterprise’s files.
- Mimic legitimate access points to trick users.
It’s a network security best practice to secure your enterprise’s wireless network. Use wireless IDS and IPS systems. Encrypt wireless data using Wi-Fi Protected Access protocols, namely WPA2 or WPA3.
Creating both a guest WiFi network for visitors and using wireless isolation techniques to make enterprise information inaccessible from guest wireless networks is vital.
6. Use virtual private networks (VPNs)
Many enterprises have a global workforce that clocks in from their homes and other remote locations. The remote workers connect to the enterprise network via the Internet, a public network, consequently presenting a risk to enterprise network security.
VPN software solves this by creating an encrypted, private connection between the remote computer and the enterprise network through the Internet. Since the VPN provides a secure channel, the user can now safely use the public Internet to access the enterprise network.
Mandate VPN usage whenever employees connect remotely.
7. Enforce both multi-factor authentication (MFA) and strong passwords
Strong authentication techniques are an essential part of network security.
MFA requires more than one authentication method before granting access to a network. The user has to validate their identity using a combination of the following:
- Personally set passwords.
- Codes sent to their email or phone.
- Biometric validation, like facial scans.
- Physical keys that plug into their device.
If MFA isn’t practical for your organization, consider using other authentication methods.
For example, the active directory authentication method requires users to provide their login credentials to an authenticating server (AS), which verifies the credentials and gives the user an authentication token that grants access for a limited time.
Regardless, what’s non-negotiable is insisting employees use strong passwords and change them frequently.
8. Establish a zero-trust strategy
An enterprise firewall protects the organization’s internal network from outside threats, but internal threats can also bring an enterprise network down.
This is why zero-trust network access (ZTNA) is the most popular emerging IT technology enterprises implement.
The zero-trust strategy is to authorize and authenticate every user, even if they connect from a trusted device on an internal network. ZTNA uses as many data points as possible to authenticate users, such as their credentials, locations, and device health.
A zero-trust strategy gives users the least possible access needed to complete their work. This access is granted for a limited time and ends once the job concludes.
9. Train your employees to adhere to security policies
Security measures rely on employees and users who follow protocols and policies. A 2023 report on the identity security threat landscape revealed that 74% of participants were concerned about data loss due to employees, ex-employees, and third-party vendors.
Hence, training your employees to conform to enterprise network security practices is crucial. Invest in training until employees at your enterprise know how to:
- Avoid using unsafe file transfer methods.
- Use both strong passwords and multi-factor authentication.
- Maintain uptime on both firewalls and malware protection tools.
- Detect and report phishing emails.
- Both use a VPN and stick to secure websites.
10. Conduct security audits and install updates
It’s not enough to configure security devices, tools, and software once. Run a routine audit of your security configurations, network devices, and endpoints periodically.
Any new network device needs double-checking for the correct settings. Test that your firewalls, VPNs, MFA, intrusion prevention software, and all other security devices are working as intended.
It’s also crucial to update your network devices and endpoints. This includes the following:
- Updating both anti-virus and anti-malware software.
- Installing new security patches and feature updates.
- Replacing network device hardware with the latest version.
Final thoughts: Enterprise network security best practices
Enterprise network security is indeed a serious concern for large organizations. Enterprise networks are susceptible to cyber threats — but now you know how to implement best practices like network segmentation, multi-factor authentication, and zero-trust strategy.
Once network security best practices are in place at your enterprise, look forward to complete compliance with data security regulations, smooth and secure operations, and increasing customer trust.
The ideal hosting partner will help you reach that goal quicker. Get a head start with Liquid Web’s enterprise hosting solution; it markedly comes with DDoS protection, antivirus and malware scanning, vulnerability assessments, and intrusion detection systems.
Related Resources

Luke Cavanagh
Product Operations Manager at Liquid Web. Devoted husband and Tween wrangler. Synthwave enthusiast. Jerry Goldsmith fan. Doctor Who fan and related gubbins.
Keep up to date with the latest Hosting news.



