Network Security: Exploring Cloud-Based Firewalls and Their Advantages
Regardless of how you may deal with customers’ data, privacy laws require you to protect critical information from prying eyes.
Still, that’s easier said than done with rising cybersecurity attacks and malicious actors. According to Verizon’s 2023 Data Breach Investigation Report (DBIR), 83% of data breaches involved external factors.
In short, you need to protect your business from external attacks.
While there are many ways to do that, your best option is to stop shady traffic from entering in the first place.
And if you’re hosting your website or application on a cloud, that’s what a cloud-based firewall is for.
Let’s see what a cloud-based firewall is, what it offers, and how to configure it properly.
- What Is a Cloud-Based Firewall?
- How Do Cloud-Based Firewalls Work?
- Cloud-Based Firewalls vs Traditional Firewalls
- Benefits of Cloud-Based Firewalls
- Types of Cloud-Based Firewalls
- How To Select a Cloud-Based Firewall
- Best Practices for Managing a Cloud-Based Firewall
- Final Thoughts: Cloud-Based Firewalls — Boosting Cybersecurity With Ease
What Is a Cloud-Based Firewall?
Cloud-based firewalls are software-based filters that allow or disallow the flow of content between your cloud infrastructure and the Internet.
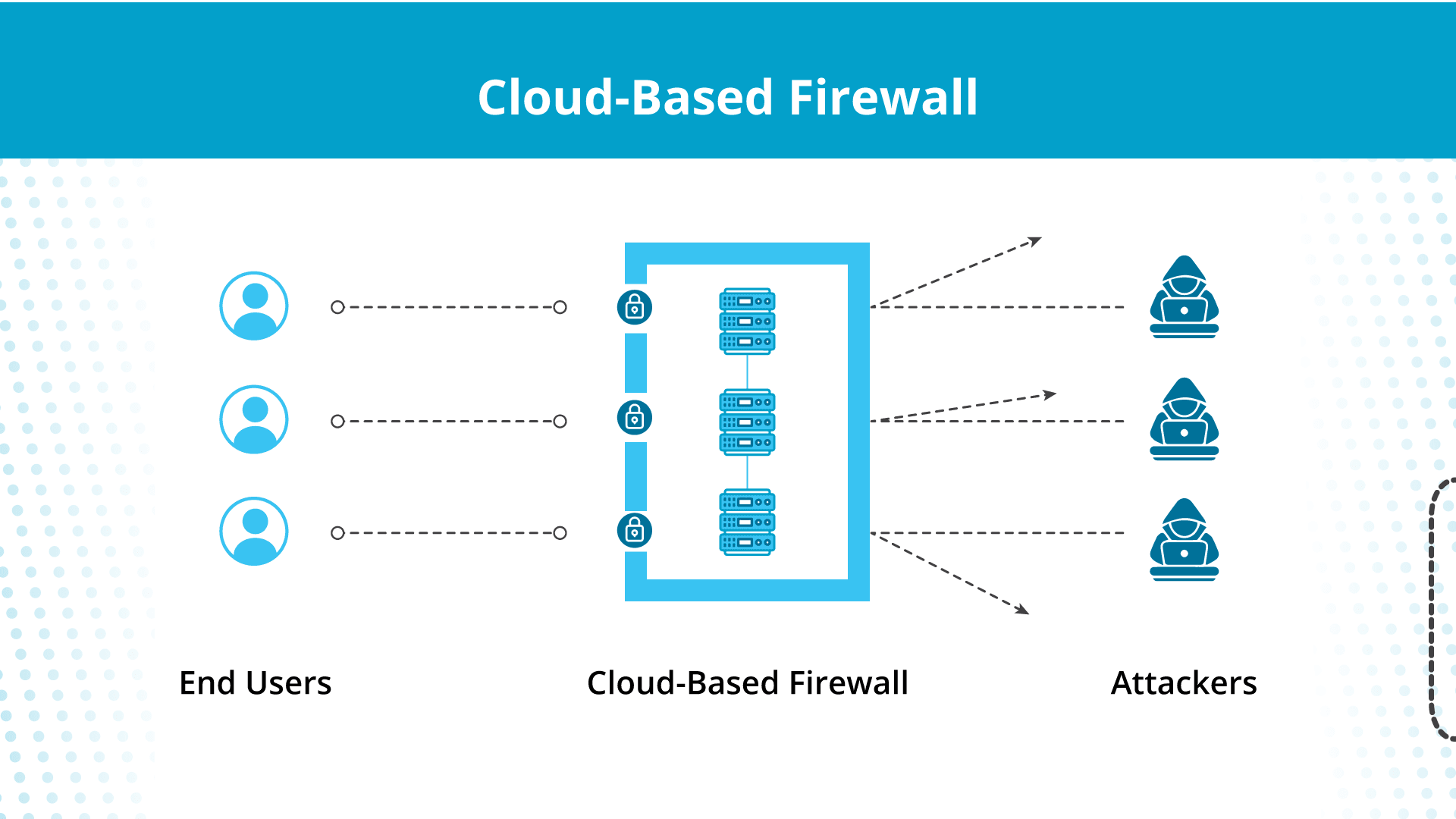
Think of cloud-based firewalls as security guards who can differentiate between legitimate customers and thieves based on preset configurations. Instead of metal detectors to detect weapons, they use blocklists to restrict traffic with negative signatures from entering the cloud.
And, unlike traditional firewalls, cloud-based firewalls are based in the cloud, so they protect your cloud content regardless of location.
How Do Cloud-Based Firewalls Work?
While a cloud-based firewall is located on the cloud, it performs its functions like that of a hardware firewall.
- Traffic monitoring — A cloud-based firewall separates the system from the Internet, and all incoming traffic has to pass through its gates to enter your cloud.
- Filter-based access — The firewall separates the good and bad content based on how the cloud provider configures the filters. Authorized content passes through, and unauthorized data stays outside.
- Restricted outbound traffic — Besides filtration of incoming traffic, cloud-based firewalls restrict outgoing traffic so only the permitted content leaves your network. For instance, you want to send necessary API requests out but wouldn’t want to send sensitive customer data outside the network.
In short, the basic working of the cloud-based firewall is identical to traditional firewalls. The differences appear only when you look at the two types at a macro level.
Cloud-Based Firewalls vs Traditional Firewalls

So how do cloud-based firewalls compare with old-school physical firewall security guards? The answer typically depends on your application.
Unlike cloud-based firewalls that reside in the cloud, traditional firewalls are located on the organization’s on-premises server. In addition, while cloud-based firewalls are always a software solution, traditional firewalls may consist of a software solution or a physical device.
Hardware specifications limit traditional hardware firewalls, and software firewalls rely on on-premises computing resources. So if a traffic spike occurs due to a distributed denial-of-service (DDoS) attack, they can’t scale up to meet the resource demand.
In contrast, cloud-based firewalls have the flexibility of the cloud and can scale up and down as required.
You’re also fully responsible for regular maintenance and updates of the traditional firewall. Maintenance of cloud-based firewalls, on the other hand, typically falls under the cloud provider's responsibility.
Benefits of Cloud-Based Firewalls
While cloud-based firewalls are implemented for cloud security, they offer several other additional benefits:
Scalability
Scalability and the cloud go together like coffee and mornings. Unlike traditional firewalls, cloud-based firewalls can scale up and down according to need without bandwidth limits.
Since cloud-based firewalls don’t depend on on-premises physical infrastructure, you can quickly increase the capacity during peak traffic demands.
Global Protection
Cloud-based firewalls are hosted on the cloud, so your network is protected globally regardless of where the incoming traffic comes from.
With worldwide servers and edge content delivery networks (CDNs), you can benefit from this robust security solution without affecting the end-user experience. In fact, your users will experience lower load times and latency, depending on where they are located.
Streamlined Management
While cloud-based firewalls let you create smaller application containers for your users worldwide, you don’t need to rely on their technical know-how to protect your network. Instead, you can manage everything from a central interface.
For instance, you can use the cloud-based firewall dashboard to:
- Update security policies across all networks and locations.
- View and monitor all security events and potential threats.
- Apply security patches to the whole cloud network.
Remote-Friendly
Owl Labs’s 2022 State of Remote Work report found that almost two-thirds of workers feel more productive working from home instead of in the office.

However, letting employees access your secure system remotely means expanding your attack surface to malicious attackers. This isn't good news if you’re a HIPAA-compliant business since you must keep sensitive data safe from prying eyes.
Cloud-based firewalls solve this remote work issue by letting you implement solutions like content filtering and virtual private connections to help remote employees access the system without exposing it to the outside.
Automatic Updates
Since 74% of data breaches involve human error, automatic updates are a great benefit of cloud-based firewalls.
Unlike on-premises firewalls, where your IT team has to apply security fixes and vulnerability updates manually, cloud-based firewalls receive regular, automatic updates directly from the cloud provider.
Real-Time Threat Intelligence
Cloud-based firewalls are powered by large security databases that help them make data-driven decisions against advanced threats in real time.
For example, if a cloud-based firewall senses an attack pattern on one side of the globe, it shares the information with the rest of the cloud infrastructure to improve collective security against emerging threats.
Fast Deployment
Since a cloud-based firewall is software-based, you can deploy it in almost no time. That allows you to apply security measures to your IT infrastructure in minutes instead of waiting for the hardware firewalls to be shipped and configured.
Types of Cloud-Based Firewalls
While every firewall on the cloud is a cloud-based firewall, there are different classes you must consider to better protect your infrastructure:
Public Cloud Firewalls
A public cloud firewall is a cloud-based firewall set up by the public cloud providers like Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP).
A public cloud firewall typically creates security protection around the virtual machines and cloud storage and prevents unauthorized parties from accessing your hosted content.
While you have some degree of flexibility, most public cloud firewalls work with predefined configurations to keep the overall cloud environment stable and secure and aren’t tailored to your specific needs.
SaaS Firewalls
A SaaS firewall, or firewall-as-a-service (FWaaS), is a cloud-based firewall. Organizations deploy these firewalls on their cloud infrastructure to filter moving traffic and identify threats within it.
SaaS firewalls protect your IT infrastructure on a subscription basis. Instead of manually configuring software-based firewalls on the VMs, you can rely on the firewall provider to handle everything.
Web Application Firewalls
Web application firewalls (WAFs) are cloud-based firewalls designed for filtering and blocking web-based attacks at the application level. They are typically located in front of web servers and apps since they help filter HTTP and HTTP traffic.
Website hosting providers commonly use WAFs as security measures against SQL injections, cross-site scripting (XSS), and other common vulnerabilities of web applications like WordPress.
Next-Generation Firewalls
Next-generation firewalls (NGFW) are robust firewalls that combine traditional firewall functionalities with several advanced security measures.

For instance, NGFWs offer:
- Intrusion prevention systems (IPS) — NGFWs monitor the network traffic for known attack signatures and patterns to prevent malicious agents from reaching your sensitive data.
- Deep packet inspection (DPI) — Next-generation firewalls perform deep packet inspections at the application layer to understand the content and context of the network traffic. This lets NGFW implement a security policy based on the content of the data packets.
- Support for virtual private networks (VPN) — Many NGFWs offer support for VPNs and help you allow secure access to remote employees without the risk of data breaches.
How To Select a Cloud-Based Firewall
While an NGFW may seem like your best bet for robust security, it’s not always the optimal solution for every application. For instance, a WAF beats NGFW for common web applications by providing cost-effective security with a simplified deployment.
Here are the top considerations when choosing a cloud-based firewall for your application:
- Security features — Ensure the firewall provides robust protection against relevant cybersecurity threats. For instance, if you own a SaaS application, look for DPI, application-aware filtering, threat intelligence, and DDoS protection.
- Performance — Evaluate how the firewall handles the traffic. Ensure it doesn’t affect user experience by increasing latency or response time.
- User interface — Assess if the firewall interface makes it easy to manage the access control policies and get real-time reports. If the dashboard is complicated, ensure the provider offers documentation and customer support to help your IT team during onboarding.
- Compliance — If you must comply with PCI-DSS or HIPAA, ensure the tools and features needed to secure sensitive data per those security standards are available.
- Redundancy and Failover — If you’re inclining toward a SaaS firewall, review the firewall provider’s failsafe mechanisms to ensure your infrastructure security in case of accidents.
Best Practices for Managing a Cloud-Based Firewall
Once you decide on a cloud-based firewall, you can make it your own by applying custom security rules and regulations that suit your application. However, you must follow certain best practices to ensure you benefit from the firewall instead of leaving the floodgates open for malware.
Develop a Security Policy
To start off on the right foot, establish a security policy for the cloud-based firewall that your IT team understands and agrees with. This way, everyone dealing with the firewall will know what’s allowed and disallowed and can work together to monitor potential threats.
For example, consider listing source channels for traffic and how much risk each carries. Consider plugging that port if a particular channel brings meager traffic but increases security risks.
Enforce Default Deny
Approach configuration as if everything is lava and there are a few safe spots. In other words, instead of blocking specific malicious traffic, start by blocking everything and then only allowing safe traffic.
Keep Security Rules up to Date
Since firewalls rely on preset configurations to separate safe and unsafe traffic, keep the security rules up to date.
Monitor Security Logs
Enable logging to collect security records of warnings and potential security breaches. Review them regularly to protect your system against ongoing threats.
Segment the Traffic
Segment the traffic into different security levels and limit access to hosted content based on those levels. This way, even if malicious agents sneak through the lowest security level, they can’t touch the sensitive information stream.
In fact, this security practice is required to comply with many of the data security standards. For instance, PCI-DSS requires you to create a buffer zone between the Internet and cardholder data to only allow the necessary traffic to pass through, which isn’t possible without a firewall segmenting the incoming traffic.
Final Thoughts: Cloud-Based Firewalls — Boosting Cybersecurity With Ease
If you opt for the right firewall and manage it well, you can better protect yourself against most of the common cyber threats that affect modern businesses.
Still, there’s more to the security equation than just firewalls.
Our cloud dedicated hosting solutions can help protect your network security. Our ServerSecure Advanced Security comes with features like a traditional firewall, malware scanning, vulnerability assessments, and DDoS mitigation.
Related Resources
Keep up to date with the latest Hosting news.



