What is a Hardware Firewall? How It Keeps You Secure
What is a Hardware Firewall?
A hardware firewall is a physical device similar to a server that filters traffic to a computer. Instead of plugging the network cable into the server, it is connected to the firewall, positioning the firewall between the uplink and the computer. Like a standard computer with a processor, memory, and sophisticated software, this device also employs powerful networking components (hardware and software) and forces all traffic traversing that connection to be inspected by configurable rulesets which grant or deny access accordingly.
Everyone who has ever used a computer can probably tell you a story about being blocked by a firewall. As good Internet citizens, we encounter firewalls all the time, usually in the form of a software firewall running on a personal laptop or workstation. Their function is surprisingly modest. They inspect traffic as it enters and leaves the computer and, based on some simple rules, either allow or deny that traffic.
Some common examples of software firewalls you may be familiar with are:
- Windows Firewall.
- UFW.
- IPTables.
- FirewallD.
A hardware firewall operates similarly except it lives outside of the server.
How Does a Hardware Firewall Work?
The hardware firewall is set up differently depending on your current configuration. The firewall is situated outside your server and is connected directly to your uplink. If this is a new setup, the firewall is then connected to your server. If this is a new setup to a production server, a maintenance window would be scheduled to handle the physical connection. Once the connection to the server is established, all traffic to and from the server goes through the firewall, forcing it to pass inspection. This allows you to have granular control over the type of traffic you’re receiving, which is incredibly important in order to keep your device protected from malware of any kind.
Why Do You Need a Hardware Firewall?
A hardware firewall works as a filter between a computer network and the Internet. It monitors data packets and determines whether they should be blocked or transferred during transmission.
Network Protection
A hardware firewall is used to protect the entire network along with incoming and outcoming traffic. It gives network administrators the ability to control the way the network is being used. Furthermore, a hardware-based firewall can protect other network devices like scanners that don’t have integrated firewalls.
Integration
A hardware firewall easily integrates with other forms of security. Besides, in most cases, physical firewalls come with supplementary security features like a virtual private network (VPN). Using a firewall with a VPN connection, you can have the security and control to grant access to the people who need secure access anywhere there’s a stable Internet connection.
Autonomy
Even though hardware firewalls are not easy to manage, you don’t have to worry about updates and unexpected crashes since they do have built-in 24/7 protection. However, hardware firewalls do require monitoring and maintenance.
Resources
A hardware firewall protects the whole network. There is no need to install it on every device separately, which saves a great amount of time and resources.
Advantages and Disadvantages of a Hardware Firewall
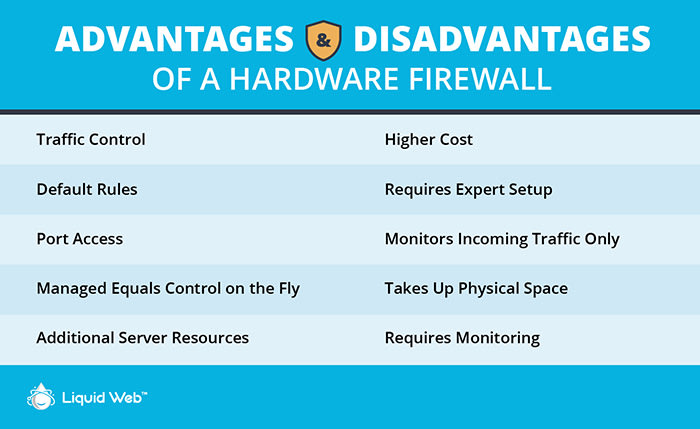
Five Advantages of a Hardware Firewall
Here are the five advantages of a hardware firewall:
1. Traffic Control
A hardware firewall will decide which traffic should and shouldn’t reach your server.
2. Default Rules
A fully configurable list of default rules which can be applied to all traffic when using a hardware firewall.
3. Port Access
A hardware firewall grants granular control to tailor rules with options like allowing all traffic to your website or ensuring only you and your developer can access SSH ports or Remote Desktop Protocol (RDP).
4. Managed Equals Control on the Fly
A fully managed hardware firewall gives you access to a fully staffed networking team to configure, troubleshoot, or adjust controls on the fly.
5. Additional Server Resources
A hardware firewall gives you access to additional server resources that would otherwise be utilized since it is a completely separate device from your server. You can even disable the software firewalls from your server and rely completely on the hardware firewall, freeing up valuable memory and processing power for the functions and services that your business needs to continue being successful.
5 Disadvantages of a Hardware Firewall
Here are a few considerations to be made if you are thinking about using a hardware firewall:
1. Higher Cost
Compared to software firewalls, a hardware-based firewall usually costs more.
2. Requires Expert Setup
This type of firewall requires a certain level of experience to set up and configure.
3. Monitors Incoming Traffic Only
Hardware firewalls are used for incoming traffic only. They won’t check the traffic coming from your device, which can lead to infection of the entire network.
4. Takes Up Physical Space
A hardware-based firewall is a separate physical device that requires space for itself and connected wires.
5. Requires Monitoring
Hardware firewalls have built-in 24/7 protection; however, they require a high level of monitoring and maintenance.
Hardware Firewall Examples
The firewall market allows you to choose the firewall based on your needs and budget. We have collected some of the most popular firewall solutions in the list below:
Cisco ASA 5500-X
Cisco presented the first threat-focused, next-generation firewall and is a leading brand when it comes to firewalls. The ASA 5500-X comes with Cisco ASA firewall protection combined with industry-leading Sourcefire threat and advanced malware protection in a single device.
Key Features:
- Multilayered protection.
- Granular visibility and control.
- Cisco AnyConnect remote access.
Bitdefender BOX
Bitdefender's technology has pioneered breakthrough innovations in antimalware, behavioral analytics, and artificial intelligence. The Bitdefender BOX comes bundled with a Bitdefender Total Security subscription which allows you to monitor inbound traffic – defending your network against potential hacks or intrusions – as well as outgoing traffic, blocking things like requests to known malicious sites or sending sensitive data (such as a password) over an insecure connection.
Key Features:
- Unlimited protection and support.
- Parental control.
- Cross-platform security.
Checkpoint
The Checkpoint solutions secure customers from Gen V cyber attacks by catching malware, ransomware, and other sorts of attacks at an industry-leading rate. Because these attacks are quick, multi-vectored, and extremely harmful, it's critical to provide an extra layer of security in addition to real-time threat prevention. Check Point firewall protects virtual instances, cloud deployments, endpoints, remote offices, and mobile devices with a single architecture and powerful threat prevention technologies in real time.
Key Features:
- Unified management platform.
- Ultra-scalable protection against Gen V cyber attacks.
- Remote access VPN.
Fortinet
Fortinet is the only security company that develops and manufactures custom security processing unit technology in order to provide the best performance and cost value in the industry. Fortinet’s firewall provides industry-leading enterprise security for any edge at any scale with full visibility and threat protection.
Key Features:
- Ultra-fast security, end to end.
- Operational efficiency and automated workflows.
- Real-time defense with FortiGuard Services.
Netgear ProSAFE
The Netgear company is known as an enterprise cybersecurity service provider that offers storage, network, and security solutions at affordable prices. This firewall router comes with a stateful packet inspection firewall, Denial of Service protection, and intrusion detection.
Key Features:
- Real-time alerts.
- 8 simultaneous VPN tunnels.
- Easy-to-use browser-based setup.
Which is Better: Hardware Firewalls vs Software Firewalls?
Both types of security firewalls are used to provide a secure connection between the local network and the Internet. The choice is mainly based on the user’s needs and financial capabilities.
We have outlined some major differences between software and hardware firewalls below:
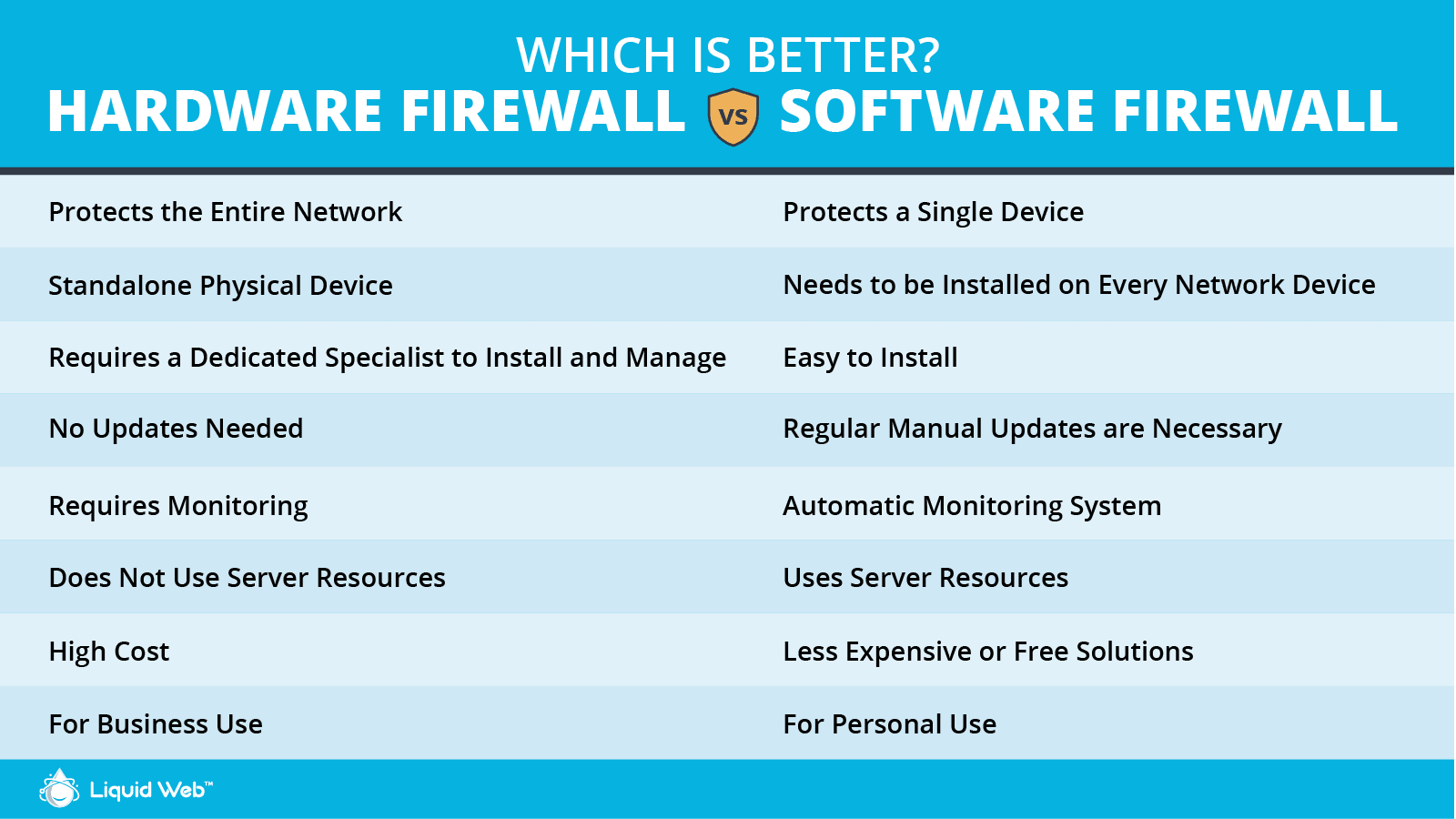
Why Choose a Hardware Firewall
Businesses are more likely to require a hardware firewall. It provides protection for your entire network through a single, standalone physical device, which means it also does not use server resources. However, while it does not require updates, it does require a dedicated specialist to install and manage. Also, a hardware firewall requires monitoring and has a higher cost than using a software firewall solution.
Why Choose a Software Firewall
A software firewall is far more likely to be used for personal use, although there are certainly business applications. Software firewalls protect a single device, so if you plan to use software firewalls to protect your entire network, it will need to be installed on each device. It is easier to install and less expensive than a hardware firewall and includes automatic monitoring. However, regular manual updates are necessary to keep protected from the latest threats, and it does use server resources since it is not on a standalone device.
Which Kind of Firewall is Right For You?
As you consider whether a hardware or software firewall is the right choice for your business, do not think about this as a simple installation. Instead, think of a firewall as a door lock. The better you want to protect yourself, the more it will cost.
We have composed a list of questions that you must consider as you choose between a software and hardware firewall:
- Is this firewall for personal or business use?
- How many devices do you want to protect?
- What is your budget for the firewall?
- How much granular control over traffic do you need?
- What are your top security threats?
- Do you have remote employees?
- Do you have a dedicated IT department that can take care of installation and maintenance?
Based on your answers, Liquid Web’s Support can help you set up your first firewall and utilize the best firewall rule practices to secure your system on each level.
Get Secure with a Hardware Firewall at Liquid Web Today
Liquid Web is a proud Cisco shop and stocks several versions of their hardware firewall devices. These devices are also powerful enough to handle traffic from multiple servers, including dedicated servers. We also employ a full staff of dedicated networking professionals 24/7/365 who can manage and maintain your fully managed networking infrastructure.
Cisco ASA 5508-X
Cisco ASA is a combination of firewall, antivirus, intrusion prevention, and virtual private network (VPN) capabilities. It provides proactive threat defense that stops attacks before they spread through the network. In addition, the Cisco ASA model performs functions of antivirus, antispam, content inspection, VPN, and SSL device
Cisco FPR 2110
Cisco FPR is a next-generation firewall line that expands the features of the ASA model. FPR’s automated updates mechanism will enhance consistent network visibility. If you are looking for a top-notch security solution, you should try our advanced malware protection to simultaneously protect your network and endpoints from online threats such as malicious firmware.
Contact us now to get started with a new firewall.

Vanessa Stephens
Vanessa Stephens has a Bachelor's degree in Information Resources Management. She has been working with Liquid Web for almost two years with much of her time spent as a Managed Applications Support Supervisor.
Keep up to date with the latest Hosting news.



