The importance of managed hosting security for your clients’ web security needs
In today's digital landscape, cyberattacks, data breaches, and other malicious activities are an ever-present threat. If you’re in the business of running websites for others, one of your primary responsibilities is to keep their sites safe from these security risks or threats at all times.
Unfortunately, this is sometimes easier said than done. Maintaining top-level security around the clock is challenging — particularly if you’re a small business owner juggling multiple clients and sites. Moreover, unless you’re a web security expert, you might not know precisely what specific tools or features your clients need for the best protection.
Enter managed hosting—a unique service that not only gives your clients’ websites a home on the web but also fortifies them with a comprehensive, multi-layered security strategy.
Read on to discover how managed hosting security can be your strongest ally in safeguarding your clients' online assets and businesses.
Unmanaged vs. managed hosting: The basics
Web hosting can be broadly categorized into two types: unmanaged and managed.
Unmanaged hosting is where the provider supplies the essential infrastructure needed to run and host your clients’ websites, such as server hardware and network connectivity, but leaves almost all other aspects of server management and maintenance to you.
That means you’re responsible for tasks such as server setup, software installations, security monitoring, backups, and disaster recovery.
Conversely, managed hosting sees the provider assume a more active role in maintaining and managing the server.
So, beyond just providing physical or virtual server and network connectivity, the hosting company also handles the following tasks:
- Server setup.
- Configuration.
- Monitoring.
- Security protocol implementation.
- Software updates.
- Backups.
- Performance optimization.
- Technical support.
Managed hosting relieves you of many of the day-to-day technical responsibilities of server and website management, allowing you to focus on more important matters like customer growth.
Benefits of managed hosting security

Entrusting the technical and security aspects of your clients’ websites to a managed web hosting provider means tapping into a pool of expertise and cutting-edge tools designed to combat even the most advanced cyber threats.
Here are some features and benefits you can expect when you opt for managed hosting security.
Proactive monitoring
In the online world, threats can emerge anytime and without warning. Managed hosting service providers understand this fact and are, therefore, always on alert. They constantly monitor servers and websites for any unusual or suspicious activity.
For example, when you host with Liquid Web, you’ll benefit from the level 3 technicians at our data centers and a fully staffed team monitoring your clients’ servers and networks 24/7/365. This ensures that potential security threats are identified early and neutralized before they escalate and cause serious damage.
Unmanaged hosting environments typically lack this level of vigilance. Without proactive monitoring, many threats can go undetected until it’s too late.
Platform-specific security measures
This means the hosting provider tailors security protocols and defenses—such as firewalls, intrusion detection systems, and DDoS protection—to each platform or website's unique requirements and vulnerabilities.
For example, WordPress-hosted sites will receive specialized security configurations that address common vulnerabilities of this content management system (CMS).
So, instead of a one-size-fits-all approach, which might leave gaps in security, you get a bespoke cybersecurity solution optimized for your specific platform.
Automatic backups
Losing data, whether due to a technical failure, human error, or an attack from hackers, can mean starting from square one — a situation no business owner wants to find themselves in.
However, the risks associated with data loss are greatly minimized with managed hosting security because most of these services come with automated daily and on-demand backups. These two features act as failsafes to ensure that your and your client’s projects, data, or crucial files are never lost.
Dedicated expert support
Another standout benefit of managed hosting is dedicated expert support. Most providers of this service offer round-the-clock customer assistance through various channels, like phone, email, and live chat. In short, help is always a touch of the button away.
What’s more, most managed web hosts boast support staff trained and experienced in a wide range of technical domains, including different content management systems like WordPress and Joomla and operating systems like Microsoft and Linux.
So, regardless of the platform or system powering your clients’ sites, a knowledgeable professional familiar with your specific ecosystem is ready and eager to assist.
Compliance tracking
If your clients operate in a region or industry that requires compliance with specific privacy and security regulations, you’ll need to make sure your hosting environment complies with those standards. With this in mind, managed hosting providers usually have experience with implementing these kinds of standards and can help ensure your sites are compliant.
Examples of compliance requirements include:
- The Payment Card Industry Data Security Standard (PCI DSS): for businesses that process credit card transactions
- The General Data Protection Regulation (GDPR): for businesses that operate in the EU
- The Health Insurance Portability and Accountability Act (HIPAA): for businesses that handle healthcare data
The ramifications of non-compliance can be quite severe for your clients. To illustrate, failure to comply with PCI DSS may result in fines of between $5,000 and $100,000 per month.
With managed hosting, you can help your clients sidestep these potential pitfalls, relying on the provider's expertise to maintain a compliant and secure hosting environment.
Cost Savings

The financial implications of cyberattacks are daunting. For example, according to IBM, the global average cost of a data breach in 2023 was a staggering $4.45 million. Beyond direct financial losses, there are also ripple effects like lost business, reputation damage, and potential lawsuits.
Investing in managed hosting security shields you and your clients from a myriad of unforeseen expenses, including post-breach clean-ups, downtime-associated revenue losses, and legal fees.
Additionally, having a dedicated security team from the managed hosting provider overseeing and handling your clients' security eliminates the need to hire a large in-house team or outsource the task to a third party. You can channel the money saved to other areas of your business.
Peace of mind
Constantly worrying about the security of your clients’ websites can distract you from core business priorities. With managed hosting security, you can rest assured that your clients’ sites are safe and in capable hands. With this peace of mind, you can redirect your energy and focus on other important matters.
Types of threats that managed hosting security can protect against
Managed hosting security can protect your clients' websites from a relatively wide range of threats. These include:
- Distributed Denial of Service (DDoS) attacks: A DDoS attack involves attackers flooding a web server with traffic, rendering it unavailable to legitimate users.
- Brute force attacks: Here, attackers repeatedly guess passwords or other authentication information or credentials until they find the right combination.
- Malware attacks: These are malicious software designed to infiltrate, damage, or take control of a network or website. Common attack vectors are outdated CMS and applications with known security issues that have been fixed but not updated. Examples are viruses, worms, trojans, spyware, and ransomware. Managed hosting providers deploy regular malware scans, ensuring early detection and removal of these programs.
- SQL injection: This type of attack involves inserting malicious SQL code into the web application’s input fields. This could allow the attacker to view, manipulate, or extract data in the site’s database.
- Cross-site scripting (XSS): This is a vulnerability that allows attackers to inject malicious code into a website, which unsuspecting users who visit the site can then execute. Once executed, the code could allow attackers to steal sensitive data, like personal information and login credentials, directly from visitors’ browsers.
- Phishing attacks:Phishing involves tricking victims into divulging important personal information, like by creating fake, look-alike websites. While managed hosting can’t prevent scammers or fraudsters from trying to trick consumers, they do offer SSL certificates that can help users ascertain the legitimacy of a website.
- Man-in-the-middle (MiTM) attacks: These are threats where the attacker intercepts communication between two parties with the goal of stealing sensitive information or spreading malware. Managed hosting employs encryption protocols that ensure secure data transmission and prevent outside interference.
How to choose a managed hosting service with strong security
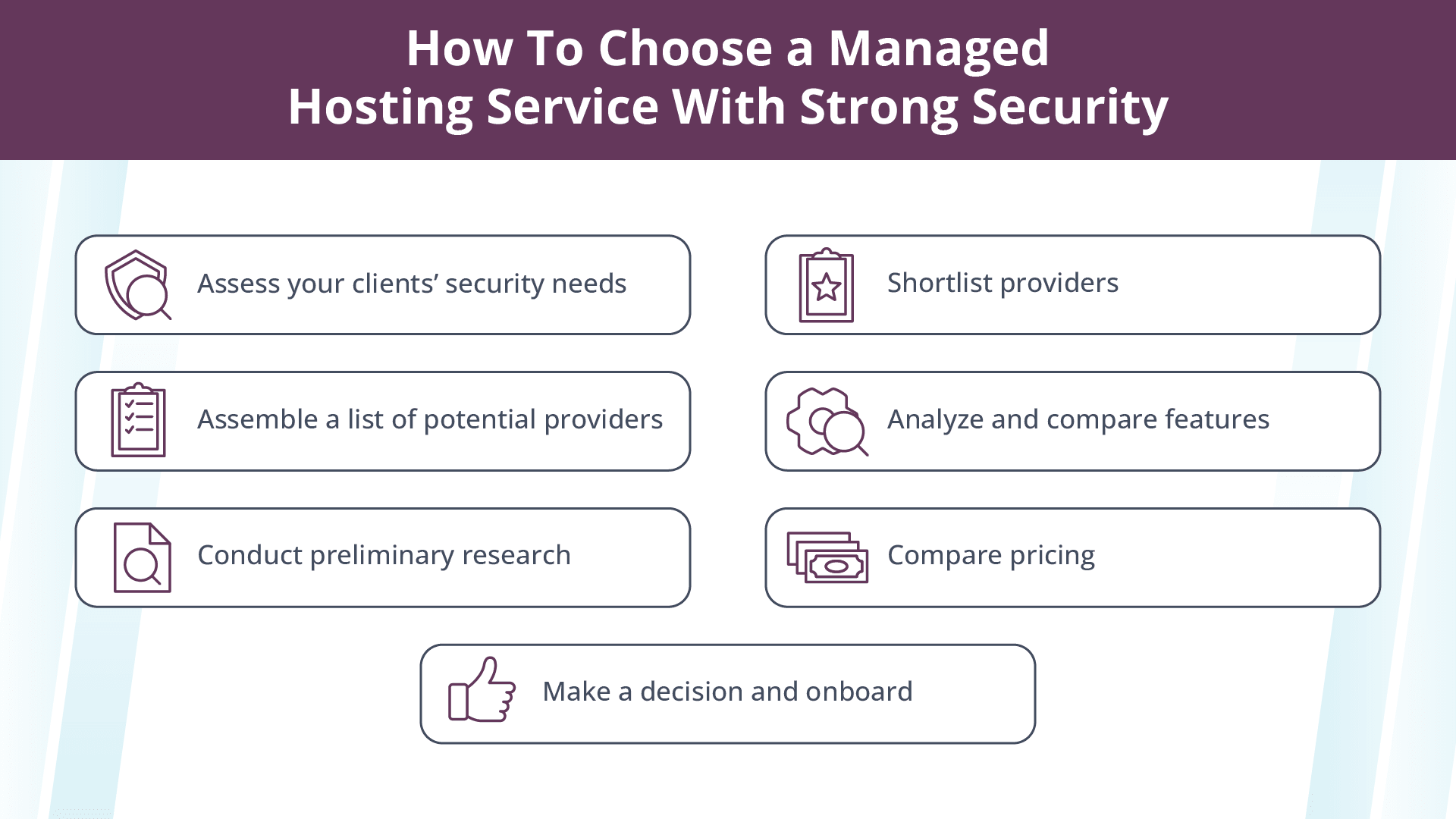
With so many managed hosting providers out there, it can be difficult to choose the right one for your needs. Here’s a useful step-by-step guide you can use.
1. Assess yourclients’security needs
Every client is unique, and so are their security needs. So, start the process of choosing a managed hosting provider by clearly articulating their security needs. Ask yourself the following questions:
- What types and amounts of data do your clients handle?
- What types of threats are most relevant to their business?
- How much traffic do they typically get?
- Are there compliance standards they need to adhere to? If so, what kind?
This exercise will help ensure that the provider you opt for is perfectly attuned to your client’s specific needs.
2. Assemble a list of potential providers
Having established the security needs of your clients, you now need to compile a list of potential providers.
Start with your professional network. Colleagues and acquaintances in the industry can offer invaluable recommendations that are grounded in first-hand experience.
Next, venture into online sources such as industry forums, expert blogs, and tech communities. These can also help you identify reputable providers worth considering.
3. Conduct preliminary research
With a list of potential providers, the next step is to do some preliminary research.
Commence by reading customer reviews and ratings on independent forums. Assess the general perception or sentiment about each provider among the public.
Next, do some research on each provider’s history. For example, when were they founded? Have there been any reports of security breaches? If so, how did the provider respond? Did they promptly acknowledge the breach and take corrective action, or did they deflect responsibility?
The handling of past vulnerabilities can provide a glimpse into a provider’s resilience and integrity.
Transparency is also key, so look into it too. Assess how forthcoming each provider is about their operational standards, security measures, infrastructure, and even pricing.
Last but not least, check for and compare the security and compliance certifications of the providers on your list. For example, certifications like ISO 27001 or SOC 2 can be strong indicators of a provider's commitment to security. Make sure to verify the authenticity of these certifications.
4. Shortlist providers
Based on your research findings, narrow down your list to a handful of providers that seem to meet your primary criteria.
As a general guideline, your list should include providers with stellar reputations, a proven track record in handling security incidents, a comprehensive set of service offerings, and an evident commitment to user security.
5. Analyze and compare features
With a shortened list, it’s time for a more in-depth comparison. Take a closer look at what each shortlisted provider brings to the table security-wise.
What DDoS protection tools and mechanisms do they offer? How comprehensive are their malware defense strategies? Additionally, do they provide SSL certificates, crucial for ensuring data transit security for your clients? What about firewall protection and backups? Analyze these features keenly for each provider and make relevant comparisons.
Keep in mind that even with top-notch security, things can still go awry. If that happens, having a dedicated support team on standby can make a world of difference.
So, in addition to comparing specific security features, look into the technical support each provider offers, including availability (i.e., whether support is available 24/7) and the promised response time.
6. Compare pricing
With a clear grasp of the features of each provider, shift your focus to reviewing their pricing models.
Here are some questions to consider:
- Can you afford the costs indicated?
- Do the costs resonate with the breadth and depth of security features on offer?
- Are there any hidden costs or fees?
- Is there cost-effective scalability in place? In other words, as your clients' businesses grow and evolve, will the hosting plan accommodate their expanding needs without breaking the bank?
An important note: When analyzing prices, don’t look at the numbers alone. An inexpensive plan can mean gaps in security measures or a lack of essential features. Conversely, a hefty price tag does not always equate to a bulletproof security suite.
The emphasis should be on the value proposition: What tangible and intangible benefits are you deriving from the amount you're investing? Make sure you're not just paying for a brand name or superficial features but for a comprehensive solution that truly serves you and your clients' best interests.
7. Make a decision and onboard
With all the necessary research, analysis, and comparison done, the stage is now set to make an enlightened choice. Choose the managed hosting provider that provides the best balance between your security needs, your budget, and your business goals.
With that done, all that’s left is to contact the provider and commence the onboarding process.
Final Thoughts: The importance of managed hosting security for your clients' security needs
Switching from unmanaged to managed hosting can be a game changer for your business.
It's an investment that not only safeguards your clients' digital assets to the highest possible level but also frees up valuable time and resources that you can channel toward your core business activities.
If you’re in search of a top-managed hosting solution for your clients, then look no further than Liquid Web. Our comprehensive managed hosting portfolio includes:
In addition to unparalleled security, our plans come with a 100% uptime SLA. This means we’ll do everything in our power to ensure your sites are always up and running, and we’ll issue a credit to compensate you for any downtime. Also, if you encounter any challenges or have a query, our expert support team is on hand 24/7/365 to provide the necessary assistance.
But there’s more. Liquid Web also has an attractive partner program that you can sign up for to unlock exclusive perks like a dedicated account manager, priority support, and referral commissions that scale as you grow.
Explore the Liquid Web partner program to learn more.
Related Resources

Luke Cavanagh
Product Operations Manager at Liquid Web. Devoted husband and Tween wrangler. Synthwave enthusiast. Jerry Goldsmith fan. Doctor Who fan and related gubbins.
Keep up to date with the latest Hosting news.



