How to Tell if an Email is Spam
Email is huge! It’s become an indispensable part of our lives and our businesses. In fact, a report from Statista estimates some 319.6 billion emails are sent every day, worldwide. That’s 41 emails for every person on the planet. And out of all that email, around half is spam, which is why it's so important to know how to identify spam emails. Not to mention, spam is annoying, it impacts productivity, and it opens us up to phishing and malware attacks.
Follow along with this article to learn how to identify a spam email before you open, click, download, or share data, along with practical ways to protect yourself from email spam.
Easily Tell if an Email is Spam with These Tips
Here are five foolproof ways for how to identify a spam email:
1. Watch for Unknown, Spoofed, or Weird Email Addresses

A great, general rule to follow: do not open an email from email addresses you don't know or are not familiar with.
Now, in business, this isn’t always possible, so pay attention to the sender’s email address, especially if the message seems suspicious. If you’re ever unsure, don’t reply or click any links. Attackers often use weird email addresses that are known as spoofed email addresses (email addresses that appear to come from a trustworthy source) to trick the recipient. These emails often include phishing attack attempts.
Spoofing is done in a number of ways, but a few of the more common ways include:
Changing the Name of the Sender to Not Match the Sender’s Email Address
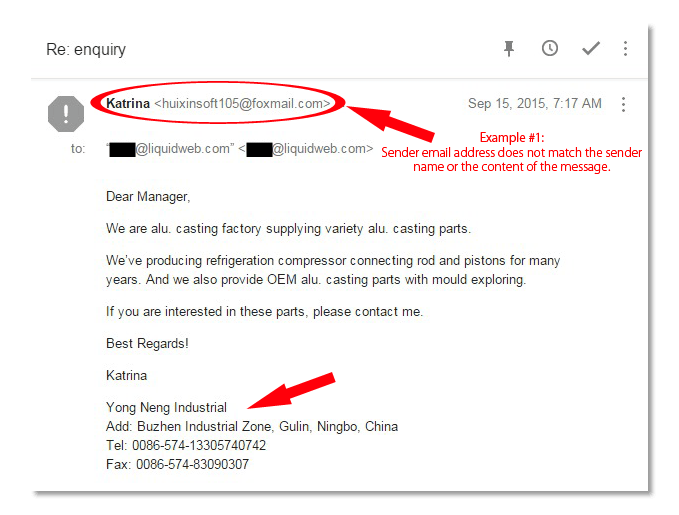
It’s easy to change the header information of an email so that the sender’s name doesn’t match the sender’s email address.
In the image example above, the spammer changed the name to read “Katrina”, in an attempt to make the email appear as if it was from a familiar source. The email address, however, is clearly unfamiliar and untrustworthy: “huixinsoft105@foxmail.com.”
Using Similar Characters in Order to Make the Sender Email Address Appear to be Recognizable
Many Greek characters look similar to Latin letters, such as the Greek character “ε” and the letter “e”. Emails may use the Greek character instead of the letter “e” in the sender’s address, like this: “example@liquidwεb.com.” Unless the recipient is paying attention, they might not notice the email address is incorrect.
Creating a Fake Sender Address That References a Trustworthy Institution
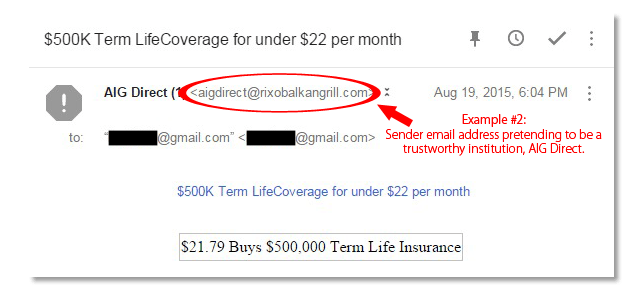
Emails like “aigdirect@rixobalkangrill.com,” as in this example, are a clear attempt to convince the reader the email is actually from AIG Direct. However, a quick google search reveals that legitimate emails from AIG Direct will probably end in “@aigdirect.com.”
2. Avoid Strange Attachments or Unfamiliar Links
The best policy is to refrain from downloading files or clicking through links in weird spam emails unless you trust the source. Malware, viruses, and other types of malicious material can be easily downloaded to your server or computer through attachments or malicious links, such as the Dropbox link in Example #3.
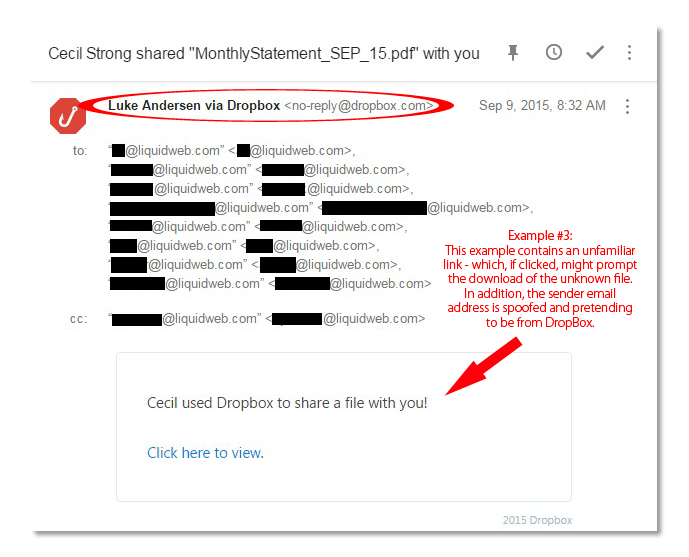
Dangerous files can come in any form, even with familiar extensions like .docx, and are often zipped to conceal their true file type.
3. Seem Too Good To Be True? It Probably Is.
Another tip on how to identify a spam email is noticing when the content seems too good to be true – often in the form of a promise for large sums of money or unprompted offers for advertisement opportunities. Such emails are almost always phishing schemes trying to collect bank account information from the recipient.
The goal of an email that seems too good to be true is to encourage the recipient to click a link and provide their bank account information – a classic phishing scam. These scams come in many forms, including the story about the government owing you money in Example #4.
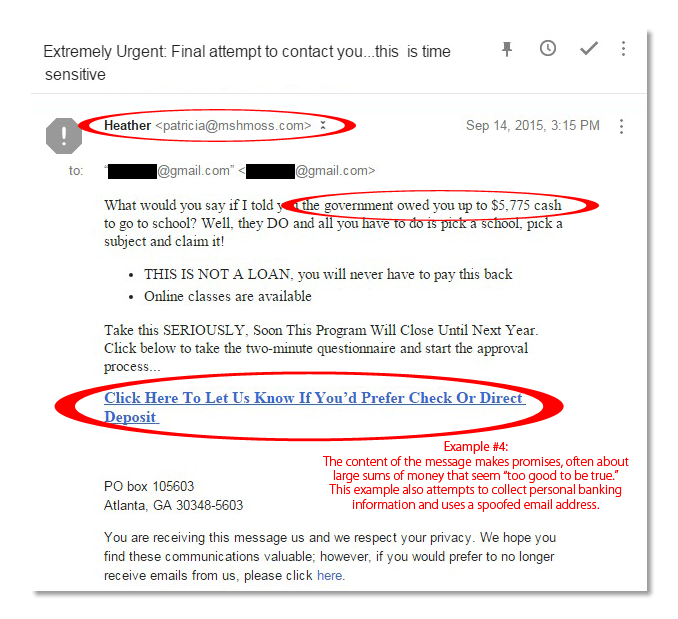
You might also see promises of money from foreign royalty, the announcement of a fake lottery win, and even get-rich-quick schemes.
4. Spam Emails May Ask for Personal Information
Phishing scams usually appear to come from legitimate businesses, like your bank or a government agency like the IRS or the Social Security Administration. These emails will often contain URLs that link to malicious web pages asking for your private information, and the spoofed pages look very convincing!
Again, we understand that, in business, it’s not often possible to avoid giving away your personal information. Just remember: legitimate businesses, like the government or Apple, will never ask for personal information such as passwords, social security numbers, or credit card numbers via email.
Giving out your information can lead to drained bank accounts or even identity theft.
5. Install Anti-Spam and Antivirus Software to Avoid Spam Emails
Our last tip to identify spam emails saves you time and stress. You can’t watch everything at once. So, one of the best ways to protect yourself from dangerous spam is to install anti-spam software that can do it for you. Liquid Web’s Protection and Remediation product handles this for you. It bundles several general server security functions, including SpamAssassin and ESET setup and configuration.
- SpamAssassin inspects incoming transmissions and tags emails as spam, giving you the freedom to delete or recover as you see fit.
- ESET monitors potentially dangerous applications.
Spam can be dangerous and can leave your computer or server vulnerable to future attacks. Following the above tips can help you identify the most common types of spam.
Also, don’t forget that even replying to spam or attempting to “unsubscribe” can come with its own set of dangers! It is always best not to reply at all if you are unsure.

Jerry Vasquez
A self-professed pirate captain with two decades of leadership experience, Jerry has led teams from 60+ cooks and chefs to 16 networking engineers. He brings those years of experience to his current role as Product Manager at Liquid Web, focusing on networking and security products. When not working or sleeping, Jerry can usually be found eating and having a good conversation with good people.
Keep up to date with the latest Hosting news.



