Locating your SSH (Secure Shell) credentials in Managed WordPress/WooCommerce
Overview
SSH (Secure Shell) is a secure network protocol used for encrypting communications over unsecured networks. Typically, you use it to log in to your server from a remote computer such as your home desktop or laptop.
SSH provides encryption on both ends — the server and the client — to keep the entire session secure. It’s an improvement over file protocols such as RSH, which uses plain text communication during data transfer.
Step by step instructions
Now that we’ve covered the basics of SSH let’s see where you can find your SSH credentials in the Nexcess Client Portal.
1. Log in to my.nexcess.net.
2. Go to the Plans area in the user interface. You can see all your active plans in this place. In this example, we’ll be working with the WordPress plan.
3. Now we need to reach our Plan Dashboard. To do so, click on the vertical ellipsis that can be found on our right-hand side to see your WordPress plan options.
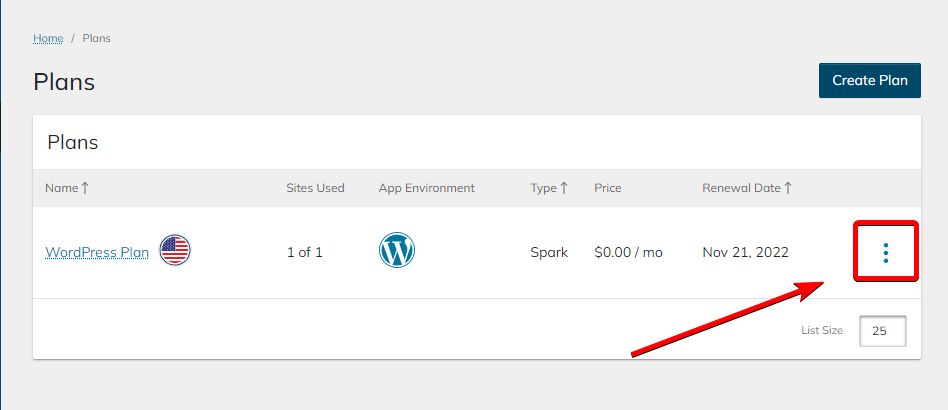
4. Navigate to the Plan Dashboard.
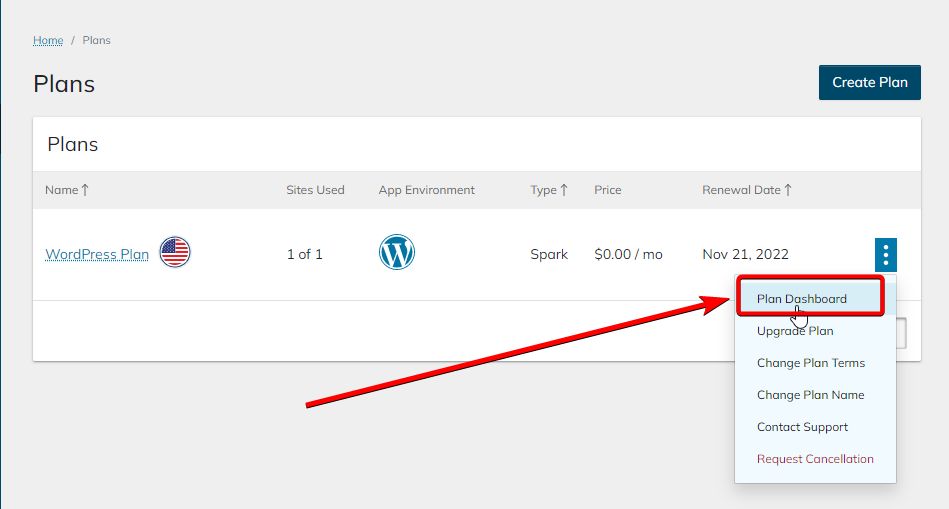
You’ll see a list of websites you have on the plan. First, find the website you want to create SSH (Secure Shell) credentials for.
5. Open site options by clicking the vertical ellipsis and navigating to Site Dashboard.
In the Site Dashboard, you’ll find Secure Shell (SSH/SFTP) credentials near the top of the page. You can also change the password by clicking the Generate New Password button location in the bottom right portion of the Secure Shell (SSH/SFTP) box:
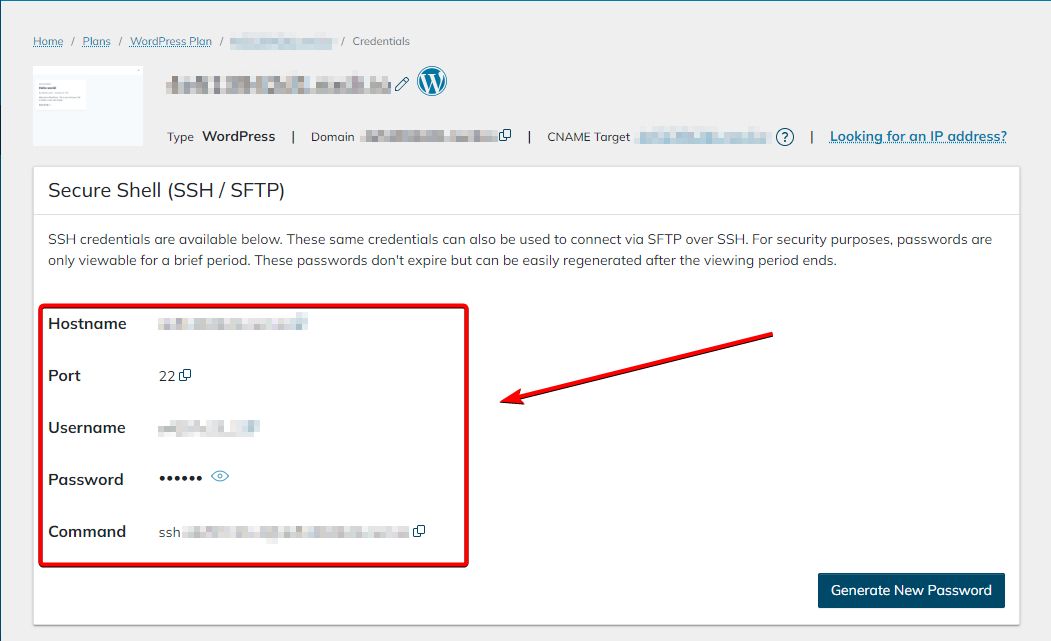
Conclusion
Now that you know how to find the SSH credentials, you can use them to control your web server and upload files remotely. In addition, SSH ensures that the link between you and the remote server remains secure, and you can do your work without worrying about data risks.