What is Kali Linux?
Kali Linux is an open-source Debian-derived Linux distribution maintained by Offensive Security. Devon Kearns and Mati Aharoni developed it. It was created explicitly for network analysts, penetration testers, or anyone in the cybersecurity field with a requirement for a very detailed scope of effort — including forensics analysis.
Unlike other Linux distros like Rocky Linux or Alma Linux, Kali Linux is intended for use by experts or individuals familiar with Linux. Many believe Kali is a tool for breaking into web servers or social media accounts. This assumption is one of the most common delusions regarding Kali Linux. It is just another Debian distribution with a plethora of networking and security capabilities. Summarizing the answer to the question, what is Kali Linux? one could say it is a cybersecurity tool for penetration testing and ethical hacking.
Advantages of Kali Linux
1. Kali Linux incorporates over 600 preinstalled network security and penetration testing tools.
2. It is open source and completely free to use.
3. Multilingual support is a key feature, allowing more users to operate in their native languages.
4. Excellent for individuals who are familiar with Linux commands.
5. It is highly customizable.
Disadvantages
1. It is mainly recommended for professionals and not for beginners.
2. There are some known glitches found in the related software components.
3. It is slower at times.
Installation of Kali Linux
System requirements
Installation of the desktop version of Kali Linux requires minimal system requirements:
- Disk space of at least 20 GB
- RAM of at least 2 GB
- OS installation via CD/DVD or USB drive
- Access to internet connection
Installation steps
The official Kali Linux website provides an installer and virtual machine images to set up and run the OS. For beginners, download the virtual machine image and run it in VMware or VirtualBox. This way, you can run the preconfigured Kali virtual machine inside a Windows environment.
1. Download the latest VMware virtual image and VMware Workstation Player for Windows from the Kali Linux official website.
2. Open the VMware Workstation Player. Next, select "Open a Virtual Machine."
3. Download and unzip the Kali image and choose the .vmx file:
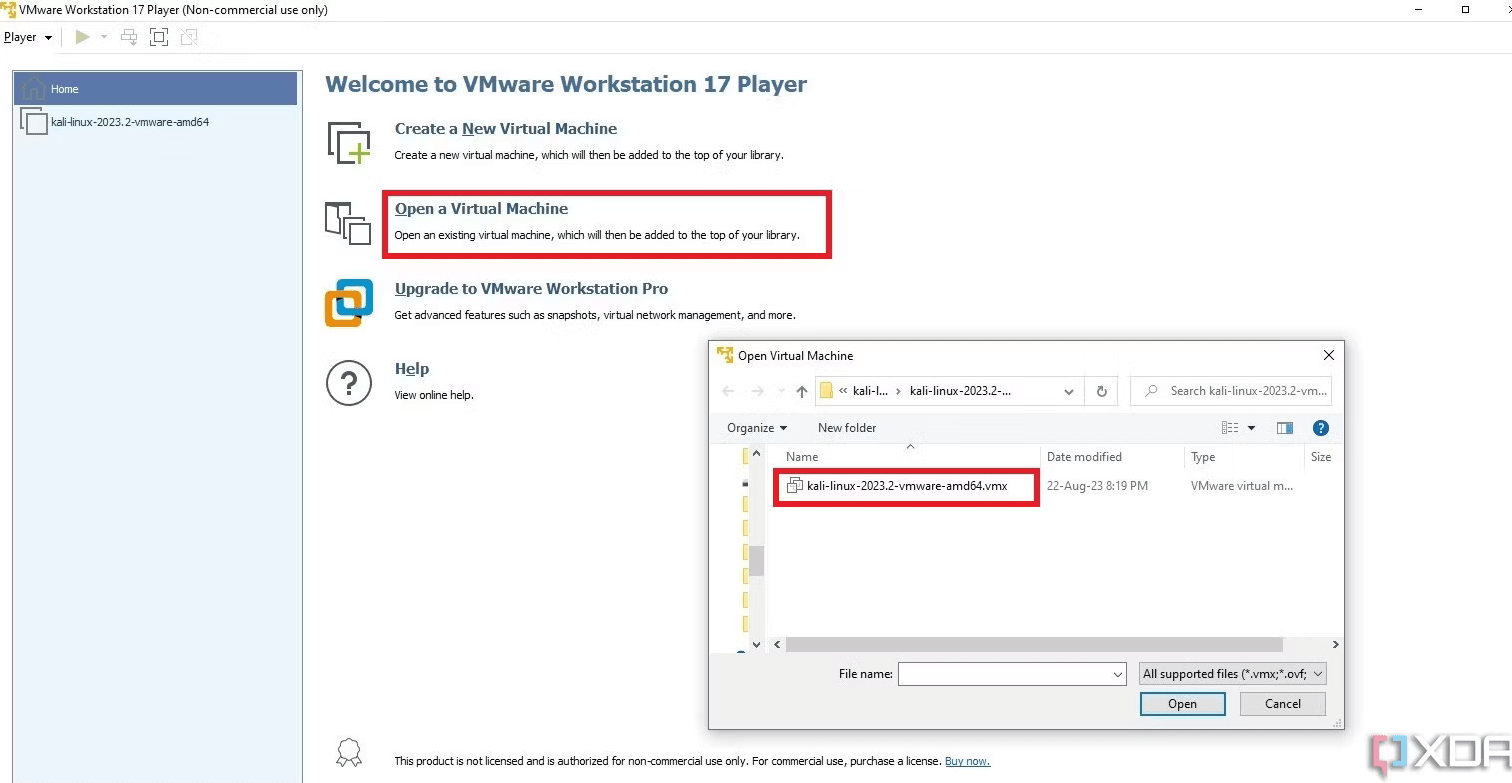
4. Click the Play Virtual Machine option on the subsequent screen.
5. Wait a few seconds for the virtual machine to boot, then enter "kali" as your username and password and log in.
An overview of Kali Linux graphical user interface
So, what is Kali Linux when unpacked? At first glance, Kali Linux's interface resembles the Windows environment. The taskbar at the top pinned icons for the file manager, terminal, and other features contains the main functionality. It also has an applications icon at the left side of the taskbar to display all installed applications, akin to the old Windows menu button.
It also incorporates almost 600 cybersecurity analysis and testing tools like the port scanner Nmap (network mapper), a password cracker, and the penetration testing Metasploit Framework. The wide range of security features makes Kali Linux immensely preferred by ethical and regular hackers:
Terminal and Linux desktop environments
Terminals available
Terminal emulator packages for CLI-based operations and desktop environment packages for GUI-based functions are typically included in Linux operating systems. A few popular terminals are mentioned below:
- GNOME Terminal
- QTerminal
- MATE Terminal
- Konsole Terminal
Linux desktop environments
Some of the Linux desktop environmentsfor Kali Linux include:
- Cinnamon Linux Desktop
- XFCE Linux Desktop
- GNOME Desktop
- MATE Linux Desktop
Kali, an operating system based on Linux, includes several terminals and desktop environments. Kali 2020.2 Linux comes with XFCE Server as the desktop environment and QTerminal as the by default terminal program.
Familiarization with the Kali Linux Terminal program
1. To customize the terminal or alter the Kali Linux Terminal's appearance, navigate to the File menu and choose Preferences. From here, you may personalize your terminal with as many choices as you prefer.
2. The command line interface can be tested by simply typing a command, and you will get the required output. The terminal will run the commands through the shell and deliver the result. For example, enter the following text into the terminal:
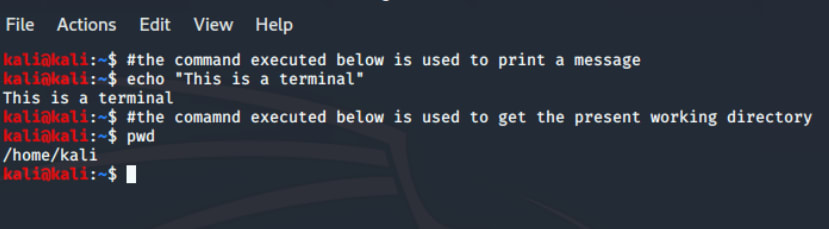
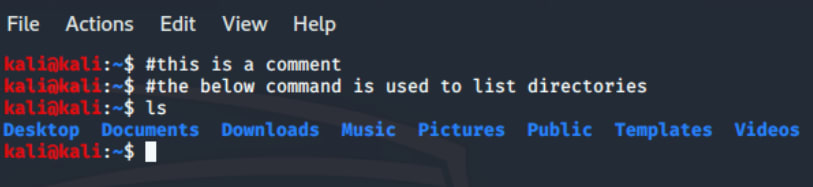
3. Comments: The "#" character is used to enter a comment in the terminal. Here is an illustration of a comment:
Command line essentials
You'll need more than just the definition and answer to the question, what is Kali Linux? Working with Kali Linux demands the use of the command line because many of its tools lack a graphical user interface, and most of the time, using the command line interface is necessary while conducting ethical hacking or penetration testing. In Kali Linux, we utilize specific commands far too often. Familiarizing ourselves with these commands will help boost our productivity. The basic Kali Linux commands are the same as Linux commands. Some of them are pwd, cd, ls, grep, mv, cp, etc.
Hashcat tool in Kali Linux
Hashcat is well-known as one of the fastest password recovery and cracking tools. Hashcat's design lets it quickly break or crack even the trickiest passwords.
Installing the Hashcat tool
Kali Linux typically comes with the Hashcat utility preinstalled. However, if installation is required, type the following command into the terminal:
sudo apt-get install hashcatNow, the Hashcat tool is available under Password Cracking Tools:
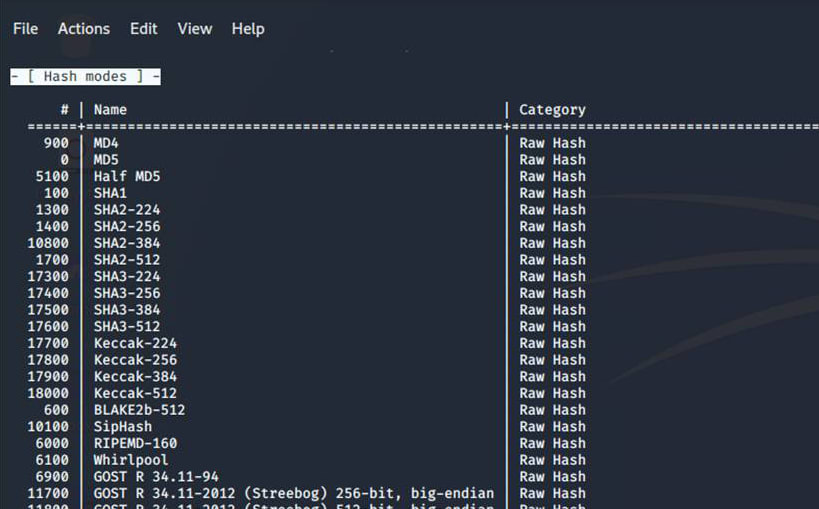
Below are a few password hashes that can be decrypted with Hashcat:
You can also check various options for Hashcat using the following command:
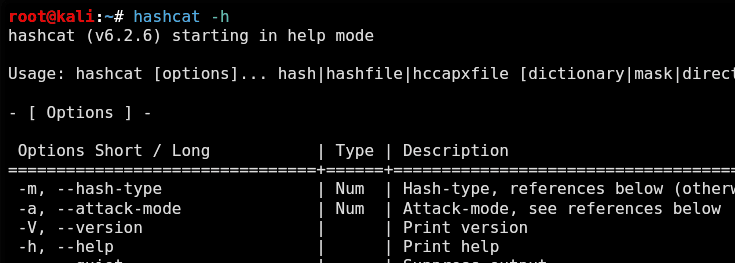
Understanding the type of hash is essential while attempting to crack it. To determine the type of hash, we can utilize the hash-id tool. Next, we must decide on our wordlist and attack type. This is the basic steps for cracking a password using the Hashcat tool.
Other tools in Kali Linux
1. Password cracking tools
Although it is easy to crack passwords using simple guessing tactics, it takes time and is less efficient. Fortunately, there are several tools available to automate this process. Kali Linux comes with many efficient tools for cracking passwords. We need a strong wordlist that can crack passwords leveraging crack hashes for password attempts. Kali Linux has a tool called Crunch, a preinstalled wordlist-generating utility to accomplish this. It is used to produce unique keywords by using wordlists and generates a list with permutations and combinations. Crunch can be executed using the following command:
crunch
crunch version 3.6
Crunch can create a wordlist based on criteria you specify. The output from crunch can be sent to the screen, file, or to another program.
Usage: crunch <min> <max> [options]
where min and max are numbers
Please refer to the man page for instructions and examples on how to use crunch.Some useful Crunch commands are shown below to generate a wordlist with 576 words having 2 and 3 digit numbers with combinations of 0, 1, 2, 3, 4, 5, 6, 7:
crunch 2 3 01234567
Crunch will now generate the following amount of data: 2240 bytes
0 MB
0 GB
0 TB
0 PB
Crunch will now generate the following number of lines: 576
00
01
02
03
04
05
06
07
10
.
.
777This command will save the list into a file list.txt:
crunch 2 3 01234567 >list.txtTo generate a specific list with a particular pattern you may use the following command:
crunch 15 15 -t liQuiswEB1^%%%%
Crunch will now generate the following amount of data: 5280000 bytes
5 MB
0 GB
0 TB
0 PB
Crunch will now generate the following number of lines: 330000
liQuiswEB1!0000
liQuiswEB1!0001
liQuiswEB1!0002
liQuiswEB1!0003
liQuiswEB1!0004
liQuiswEB1!0005
liQuiswEB1!0006
..
..
..
liQuiswEB1 9999The command to generate a list with permutations and combinations is given below:
crunch 1 12 -p Liquidweb Hosting
Crunch will now generate approximately the following amount of data: 34 bytes
0 MB
0 GB
0 TB
0 PB
Crunch will now generate the following number of lines: 2
HostingLiquidweb
LiquidwebHostingThis command generates two permutations of Liquidweb Hosting as shown above.
2. Sniffing and spoofing tools
Kali Linux is also prepacked with tools for sniffing and spoofing. Kali Linux comes preinstalled with Wireshark, one of the most commonly used network protocol analyzers. You can use Wireshark to examine what's going on in your network and use filters to find the best results for your search. Some of the other tools include MITMPROXY, Burp Suite, etc.
3. Vulnerability analysis tools
Kali Linux is also used for vulnerability analysis, one of the critical stages of hacking. Vulnerability analysis is a process in application design completed after data gathering. There are several vulnerabilities in the cyberworld, which are gaps in programs that hackers might use to launch an assault. More than 300 tools are included with Kali Linux for vulnerability checks. Some of them are Nikto, ZenMap, and others.
4. Forensics tools
Kali Linux is also equipped with tools that can be used for forensics analysis. We must understand how to protect ourselves from the ransomware, spyware, and digital viruses that are all too common these days and can spy on us and compromise our privacy. Forensics tools assist us in analyzing them, aiding in identifying the attacker and occasionally providing us with information regarding the content or creator of the file. Some of the tools include Binwalk, Bulk-Extractor, and Autopsy.
Use the flavor Linux touted by security professionals
Now you know the answer to the question, what is Kali Linux? Being one of the safest Linux distros, Kali Linux is equally beneficial for aspiring or experienced security professionals. Alternatively, Kali Linux is an excellent choice when used to investigate any program's security flaws or check for website vulnerabilities.
Kali Linux is intended for people who wish to get involved in ethical hacking, penetration testing, or cybersecurity. It's a handy and powerful tool that, if not used for good purposes, can even cause loss. Stay safe and stay ethical, please!
Related Articles:

About the Author: Sapta Upendran
Sapta is a passionate Linux system engineer, a voracious reader, a dexterous cook, and a wanderlust. She is also interested in technical and non-technical writing.
Our Sales and Support teams are available 24 hours by phone or e-mail to assist.
Latest Articles
In-place CentOS 7 upgrades
Read ArticleHow to use kill commands in Linux
Read ArticleChange cPanel password from WebHost Manager (WHM)
Read ArticleChange cPanel password from WebHost Manager (WHM)
Read ArticleChange the root password in WebHost Manager (WHM)
Read Article


