WordPress Exploit – AMP Plugin
AMP for WP -Accelerated Mobile Pages allows your site to be faster for mobile visitors. Along with last week’s report, the AMP plugin has also been added to the list exploited. The AMP for WP plugin was reported on October 20, 2018, by its developers. Luckily, the newest version, 0.9.97.20, of this plugin has patched for their known security flaws. This exploit has the means of putting 100,000+ users at potential risk, so its best to check if you are utilizing this plugin. In this tutorial, we will be checking if you use this plugin. Along with updating, we will also show you how to check if your site for compromises.
In the vein of the WP GDPR plugin exploit, the AMP hack allows code vulnerability to make site-wide changes. Bots scan for sites using the AMP plugin and use an XSS security bug to create a new user that has admin-like privileges. The vulnerable versions' (below 0.9.97.20) code didn’t cross check to see if registered users had the permissions to perform some actions. With administrative like privileges a hacker can hide their code within your WordPress files to use to take over your website. Additionally, they can upload files, update plugins, read files, and inject posts.
Identify If You Use AMP for WP
By logging into your WordPress backend you can easily see if you are subject to this exploit.
Step 1: Enter the WordPress backend by going to yourdomain.com/wp-login.php in your browser.
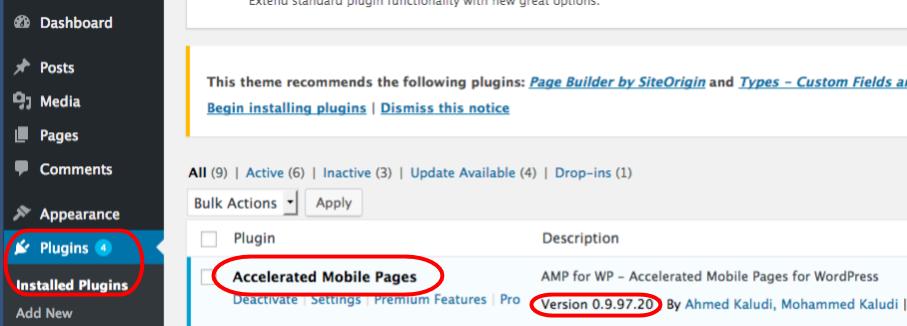
Step 2: Login with your WordPress username and password and navigate to Plugins and click on Installed Plugins on the left-hand side of your screen.
Step 3: Scroll down through any installed plugins to see if you have Accelerated Mobile Pages within your list, followed by its version. Any version below 0.9.97.20 is still vulnerable and you’ll have to perform a few actions to protect yourself.
Upgrade AMP - Accelerated Mobile Pages
Note: It’s recommended to backup your website before pushing any updates.
Step 1: Follow the steps above in the section “Identify If You Use AMP for WP” to login and locate your Plugins menu.
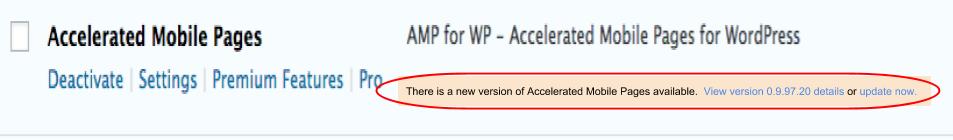
Step 2: Locate Accelerated Mobile Pages. If you are running an outdated version you’ll see a message providing you a link to update. Click “update now” to automatically update to the latest version.
Have You Been Hacked?
A site hack is possible even without noticing any visual differences to your site. For a closer inspection below are some of the characteristics of the AMP exploit.
- Characteristics of the AMP hack:
- External Calls to sslapis.com
- New creation of WordPress admin user “supportuuser”
- Post injections
- Registered user can manipulate code
- Code vulnerability in ajax hooks
- ampforwp_save_steps_data
- wp_ajax_ampforwp_get_licence_activate_update
- wp_ajax_ampforwp_deactivate_license
- wp_ajax_ampforwp_save_installer
- wp_ajax_amppb_export_layout_data
- wp_ajax_amppb_save_layout_data
- wp_ajax_ampforwp_get_image
If have identified your site is compromised from above characteristics, you’ll want to remedy it immediately since other sites on the same server can potentially be affected.
- Liquid Web customer can purchase a Malware Clean Up package
- Manually remove the code from the infected files
- Restore from a backup dated before October 20, 2018 (keep in mind this will still have the old version and your site will still be in danger).
As time goes by, more plugins will give way to more vulnerabilities but there are some proactive steps to ensure your site’s security. For insight into ways of protecting your WordPress site look into our article on the subject, The Best Ways to Protect Your WordPress Site.

Related Articles:

About the Author: Echo Diaz
Throughout Echo's four year stint as a technical support specialist, her passion for breaking down complex concepts had to lead to a career in professional writing. As a former top tier support specialist, she added a distinctive element to her written work that spoke to customer feedback and concerns. Echo occasionally pops her head out from behind her computer to watch her dog energetically run around the yard and unabashedly shovels money into buying tickets to see her favorite musical artists.
Our Sales and Support teams are available 24 hours by phone or e-mail to assist.
Latest Articles
Change cPanel password from WebHost Manager (WHM)
Read ArticleChange cPanel password from WebHost Manager (WHM)
Read ArticleChange cPanel password from WebHost Manager (WHM)
Read ArticleChange cPanel password from WebHost Manager (WHM)
Read ArticleChange the root password in WebHost Manager (WHM)
Read Article


