Guide to Using Umask Command in Linux
What is Umask in Linux?
Umask (short for user file-creation mode mask) is used by UNIX-based systems to set default permissions for newly created files and directories. It does this by masking or subtracting these permissions. For example, with the usual Umask being set to 022 on most systems all the new files we create will subtract the Umask value from full permissions (for files that would be 666 - 022 = 644). Umask can be expressed in octal or symbolic values.
- Octal values (for example 027) - The three digits will affect resulting permissions for user, group, and “nobody” users.
- Symbolic values (such as u=rwx,g=rx,o=rx) - Equivalent to octal values of 022. The symbolic permissions listed here are not really masked or subtracted by Umask, but instead, a value of u=rwx,g=rx,o=rx would result in a directory having u=rwx,g=rx,o=rx, and files having u=rw,g=r,o=r permissions since files can’t be created with executable attribute.
How is the Linux Umask Command Useful?
The Linux umask command is very useful when there are multiple users that are creating new files and directories, particularly in any kind of shared environment. System administrators can ensure that with properly set umask values, different users will make files with secure permissions by default instead of fixing and manually setting those later on, which can be risky, complicated, and time intensive.
What is the difference between chmod and umask?
While every situation is different, the advantage of umask over chmod is that it will affect all files and directories created by that user system-wide. Using chmod you would have to change permissions individually for each file specifically instead of them being made with proper permissions by default.
How does Linux Umask work?
Unix-based operating systems have a set of properties that are used to define who is allowed to read, write, or execute specific files or directories. There are three categories called “permissions classes” to which these permissions apply, and they are noted as follows.
- User: by default is the owner or creator of a file or folder. The ownership of the new file defaults to this user.
- Group: the set of users that share the same access level or permissions to a file or folder.
- Other: defined as any user not included in the previous two categories. These users have not created a file or folder, nor do they belong to a specific user group. This group includes everyone not identified as a user or as being part of a user group. When we set the permission level of a file or folder to Other, it gives permissions level access to anyone that accesses the file or folder.
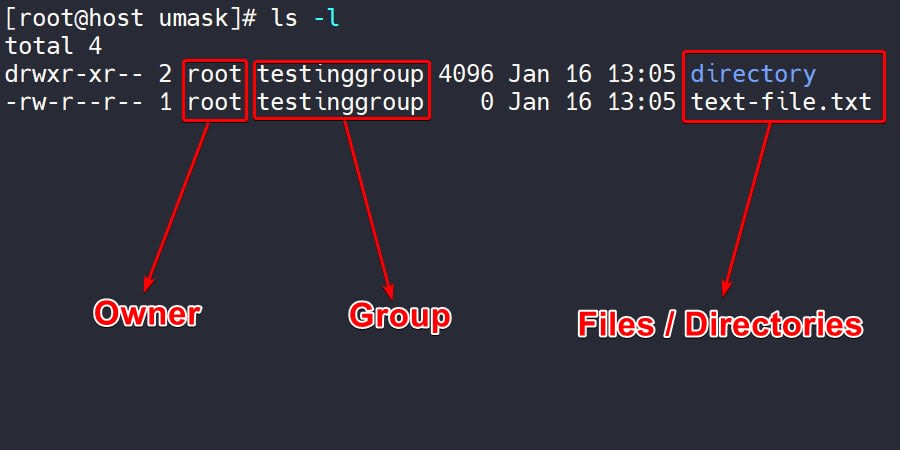
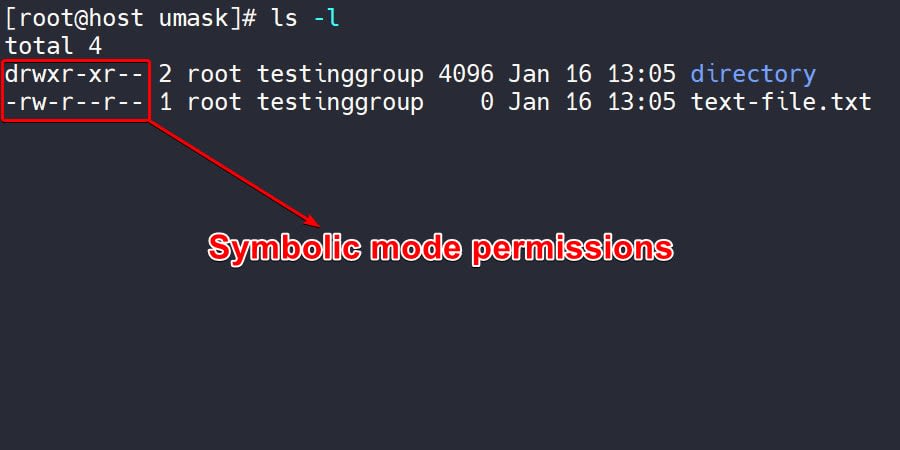
We can also see permissions in symbolic presentations on the left-hand side.
The umask command works by stripping away permissions as the file is created. On the system, the default umask is currently set to the octal value of 022. Here is what it looks like in the terminal.
[root@host umask]# umask
0022To understand with which permissions files and directories are made when umask is set to 022, simply subtract that value from the default permissions Linux sets for files and directories before umask which is 666 for files and 777 for directories.
- New files: 666 - 022 = 644
- New directories: 777 - 022 = 755
The following creates a file, then uses a modified stat command that will show the file’s permissions in octal mode.
[root@host umask]# touch newfile.txt
[root@host umask]# stat -c '%a' newfile.txt
644These commands do the same but with a directory this time.
[root@host umask]# mkdir newdirectory
[root@host umask]# stat -c '%a' newdirectory
755A umask value of 026 for a directory sets permissions for the owner to read, write and execute, for a group to only read and execute, and for other users to only have execute capability since 777 - 027 = 751.
[root@host umask]# umask 026
[root@host umask]# umask
0026
[root@host umask]# mkdir testdir
[root@host umask]# stat -c '%a' testdir
751
Below we can see how each octal value of unmask affects new files created.
- 0: read and write.
- 1: read and write.
- 2: read.
- 3: read.
- 4: write.
- 5: write.
- 6: execute only.
- 7: no permissions.
Here are the values for directories.
- 0: read, write and execute.
- 1: read and write.
- 2: read and execute.
- 3: read only.
- 4: write and execute.
- 5: write only.
- 6: execute only.
- 7: no permissions.
Where can I find Linux Umask command?
The Linux umask command can be found by simply typing umask in your terminal. You can also use the which command to find its binary path.
[root@host umask]# which umask
/usr/bin/umaskIf you want to edit the default umask value instead of setting it again each time you login, you can edit your .bash_profile and append the umask command at the bottom.
[root@host ~]# cat .bash_profile
# .bash_profile
# Get the aliases and functions
if [ -f ~/.bashrc ]; then
. ~/.bashrc
fi
# User specific environment and startup programs
PATH=$PATH:$HOME/bin
export PATH
umask 0023It can also be accomplished in your specific user’s .bashrc home directory as well.
[root@host testuser]# cat .bashrc
# .bashrc
# Source global definitions
if [ -f /etc/bashrc ]; then
. /etc/bashrc
fi
# Uncomment the following line if you don't like systemctl's auto-paging feature:
# export SYSTEMD_PAGER=
# User specific aliases and functions
umask 0023The Umask Command Syntax
The complete manpage entry for umask is as follows.
umask [-p] [-S] [mode]
The user file-creation mask is set to mode.
If mode begins with a digit, it is interpreted as an octal number; otherwise it is interpreted as a symbolic mode mask similar to that accepted by chmod(1). If mode is omitted, the current value of the mask is printed.
The -S option causes the mask to be printed in symbolic form; the default output is an octal number.
If the -p option is supplied, and mode is omitted, the output is in a form that may be reused as input. The return status is 0 if the mode was successfully changed or if no mode argument was supplied, and false otherwise.To view the current umask value, we use the umask command. Running the umask command by itself provide the default permissions that are assigned when a file or folder is created.
[root@host ~]# umask
0022
[root@host ~]#To change these values, we will use the following command.
[root@host ~]# umask ###
[root@host ~]# umask 022The ### symbols in the first command are used in lieu of an actual octal number.
Below, we can see the translated values of the octal and how they are related.
| Number | Permission |
|---|---|
| 4 | read |
| 2 | write |
| 1 | execute |
| Read | Write | Execute | Total Value | Symbolic Equivalent: |
|---|---|---|---|---|
| 0 | 0 | 0 | 0 | |
| 0 | 0 | 1 | 1 | x |
| 0 | 2 | 0 | 2 | w |
| 0 | 2 | 1 | 3 | wx |
| 4 | 0 | 0 | 4 | r |
| 4 | 0 | 1 | 5 | rx |
| 4 | 2 | 0 | 6 | rw |
| 4 | 2 | 1 | 7 | rwx |
So, when we run a ls command, the octal or symbolic permissions values are shown at the beginning of the output.
[root@host ~]# ls
drwxr-xr-x 2 root root 4096 Apr 21 12:54 test/
-rw-r--r-- 1 root root 0 Apr 21 12:53 test.txt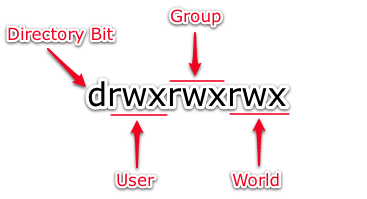
The permissions set for the test directory is 755 or 'rwx' 'r-x' 'r-x'.
The permissions set for the test.txt file is 644 or 'rw -' 'r - -' 'r - -'.
A dash signifies a 0 value.
Symbolic Headings
--- no permission
--x execute
-w- write
-wx write and execute
r-- read
r-x read and execute
rw- read and write
rwx read, write and executeNumeric Headings
0 --- no permission
1 --x execute
2 -w- write
3 -wx write and execute
4 r-- read
5 r-x read and execute
6 rw- read and write
7 rwx read, write and executeUmask Configuration Location
In most Linux distributions, the umask value can be found and configured in the following locations:
- /etc/profile - this is where system-wide default variables are stored
- /etc/bash.bashrc - this is where default shell configuration files are stored
Umask Symbols
As noted in the umask man page above, we can use specific symbols to specify permission values we want to set. To preview the currently set umask value in symbols, we use the following command:
umask -STo change it, we can use the command in which the letters “u,” “g,” and “o” represent the user, group, and other or world, as shown below.
umask u=$, g=$, o=$When settings permissions this way, we supplement each “$” placeholder with the desired permission symbol(s). The equal “=” sign is not the only operator at our disposal when setting umask with symbolic values. We can use plus “+” and minus “-” operators as well.
- The = symbol allows permissions to be enabled, prohibiting unspecified permissions
- The + symbol allows permissions to be enabled, ignoring unspecified permissions
- The - symbol prohibits permissions from being enabled, ignoring unspecified permissions
There’s an additional symbol that can be used when we want to set the same permission for all permissions classes at once (user, group, and other), and that is:
umask a=Conclusion
Now that we better understand the function of the user file mode creation mask, we can put it to good use. Not only does it save us precious time and improve security, but it also provides us with better permission management capabilities.
Your project deserves an environment able to perform and stand up to your needs. Consider Liquid Web's Dedicated Server environments for optimal performance, dedicated resources, and software flexibility. Contact our sales team to determine the best fit for you.
Related Articles:

About the Author: Freddy Reese
Freddy works in the Liquid Web Managed Hosting Support team with a strong passion for all things related to Linux administration, cybersecurity, and aviation. In his free time, he likes to keep up with the latest news on topics ranging from fusion to space technologies. His hobbies include automating all kinds of stuff using Arduino/Raspberry Pi, learning and flying around in flight simulators, playing with his dog Chupko, swimming at nearby beaches, and staying physically and mentally healthy by going to the gym.
Our Sales and Support teams are available 24 hours by phone or e-mail to assist.
Latest Articles
How to use kill commands in Linux
Read ArticleChange cPanel password from WebHost Manager (WHM)
Read ArticleChange cPanel password from WebHost Manager (WHM)
Read ArticleChange cPanel password from WebHost Manager (WHM)
Read ArticleChange the root password in WebHost Manager (WHM)
Read Article


