How To Set up an SSH Key for SFTP in SiteWorx
In this tutorial, we’ll describe how to create and set up SSH keys for SFTP connections to remote servers using the Interworx control panel. Siteworx is a part of the Interworx control panel that grants you the ability to monitor bandwidth, disk space, email, database information, and other critical information relating to your hosted websites within the same Unix account.
What is an SSH Key?
SSH keys are used to identify a user logging into an SSH server using public-key cryptography and challenge-response authentication. This adds a greater level of security to protect your sensitive data. Unlike passwords, SSH keys are automatically generated by the system and not by the user. SSH keys also ensure connections are made only from approved devices.
Using a traditional username and password would provide access to device files after simply inputting two pieces of data. Traditional password authentication is a basic security measure that might have been enough to protect sensitive data in the past, but considering the advanced attacks hackers are using today, it’s not strong enough anymore and requires additional security.
Human-generated passwords are sometimes easy to guess, used across various accounts and programs, and can allow access to the SFTP server from any device, making them susceptible to brute force attacks. Instead of creating complicated, random passwords, using SSH keys might be preferable.
What is SFTP?
SFTP stands for SSH File Transfer Protocol or Secure FTP. It was designed as an extension of the Secure Shell (SSH) protocol to enhance file transfer capabilities between two devices. To establish an SFTP connection, you’d need an SFTP client and an SFTP server. Most FTP clients like Filezilla and Cyberduck support SFTP connections.
When using SFTP for file transfer or synchronization, you will need:
- A hostname (or the IP address of the target server).
- The target port.
- Appropriate login credentials.
Depending on the server, you will need to provide either SSH credentials or FTP credentials to establish SFTP connections.
How SSH Keys Work
SSH protocol uses public-key cryptography, also known as asymmetric cryptography. Asymmetric cryptography requires two separate keys, one of which is private, while the other one is public. Together they make a key-pair.
Public-key cryptography is used in both directions when connecting to an SSH or SFTP server. The two key pairs are:
- Host (Server) Key Pair.
- Public Key: Identifies which server a user is connecting to.
- Private Key: Stored safely on the server and is only accessible by the server’s administrator.
- User (Client) Key Pair.
- Public Key: Must be stored on the server.
- Private Key: Must be stored on the device using the SFTP client and should be encrypted by a passphrase secure enough to persevere in the face of a brute force attack.
During the connection attempt, the end user would need to enter the passphrase defined when creating the key pair to decrypt the private key with the SFTP client. Then, the private key would be shared by the SFTP client in an encrypted form with the server. That key would then be compared to the public key that is stored on the server for that particular username. Once the verification is successful, the SFTP server will grant access to the connecting client.
Passphrases can be saved on a device using an SSH agent. For additional security, if a single device is connecting to various servers using an SSH key, it should have a private public key for each of them. In this case, having a private public key would mean that the device should have a different public key for each of the servers it’ll be connecting to. Using a single public key for multiple server connections wouldn’t be a good practice, same as a single password for multiple services isn’t a good practice, either.
How To Create an SSH Key Pair
To create an SSH key pair, you’ll need an SSH client, such as PuTTY (which includes a PuTTYgen). Alternatively, you can use the terminal and the ssh-keygen command.
You’ll need to define the type of key and the number of bits to use. In the below example, we’ll select RSA (Rivest-Shamir-Adleman) and set the number of bits to 4096.
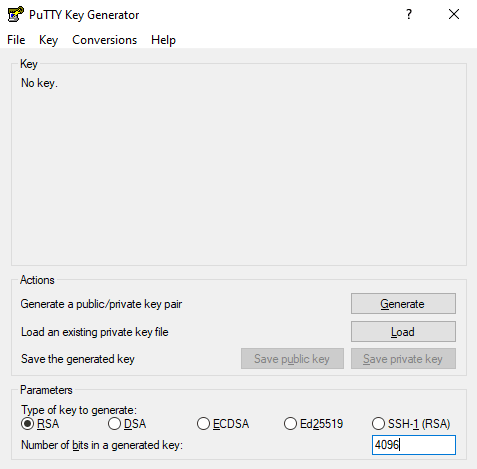
Click the Generate button to create a public key in the Key box. You’ll then be able to add a comment (if needed) and the passphrase you wish to use to encrypt the private key.
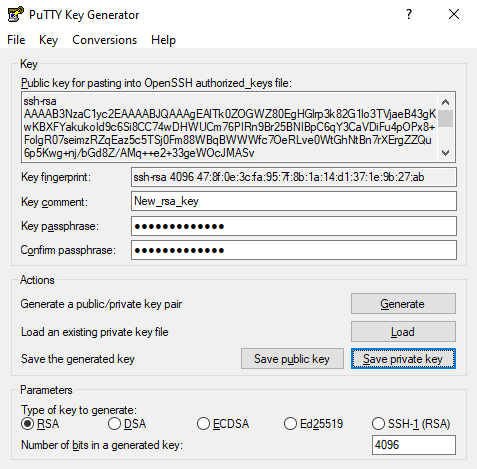
Both your private and public keys need to be saved separately. Private key files should be saved in the .ppk format, which is recognized by SFTP clients. Public keys can be named using the default id_rsa.pub or any other name you’d wish to use.
Required Server-Side Modifications
Now that you have created private and public keys, you’ll need to save the public key on the server you’re connecting to. To do that, you’d need to establish an SSH connection to the server and navigate to the directory your new FTP user will be accessing.
Create a directory called .sftp.
$ mkdir .sftpChange permissions of the .sftp directory to 700.
$ chmod 700 .sftpCopy the public key into the authorized keys file in the .sftp directory. Authorized keys file will contain all the public keys of devices allowed to connect to the SFTP server. The public key file can be opened in any text editor on the local device and pasted into a new file on the server.
$ vi .sftp/authorized_keysCreate an FTP User in Siteworx
To create a new FTP user, you’ll need to log in to your Siteworx account using the domain user credentials.
Once logged in, you’ll need to click on Hosting features (left navigation bar), then FTP, and then Accounts.
This screen shows all current FTP users for the domain and provides the ability to delete an account (by clicking Delete), modify an existing account (by clicking Edit), or add a new account.
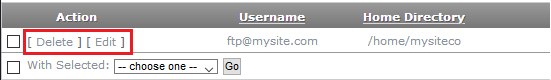
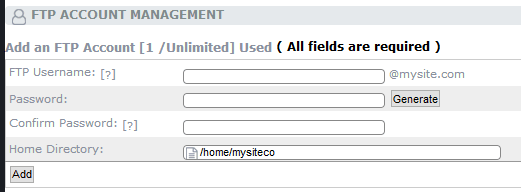
When creating a new account:
- Enter a name for the FTP account in the FTP Username box.
- Click the Generate button to create a password. This random-character password will be considered strong. Input your password a second time in Confirm Password.
- Select a Home Directory for the new user. Keep in mind the FTP user will only have access to the home directory and its subdirectories. Additionally, the Home directory should be where you created the .sftpdirectory.
- Click Add.
Conclusion
We hope you have enjoyed this article on how to set up SSH keys in SiteWorx. Do you still have questions about setting up or connecting to SFTP servers using an SSH key? Our Support Team can assist with this or other issues you may be experiencing with SSH Keys. If you are uncomfortable walking through the steps outlined here, feel free to reach out to one of our helpful Support team members via support ticket, phone, or live chat.
Related Articles:

About the Author: Amy Myers
Amy is a Linux support technician with Liquid Web and Nexcess, with expertise in customer service. She considers expanding upon and sharing knowledge as one of life's top priorities. She is an avid technology and art fan.
Our Sales and Support teams are available 24 hours by phone or e-mail to assist.
Latest Articles
How to use kill commands in Linux
Read ArticleChange cPanel password from WebHost Manager (WHM)
Read ArticleChange cPanel password from WebHost Manager (WHM)
Read ArticleChange cPanel password from WebHost Manager (WHM)
Read ArticleChange the root password in WebHost Manager (WHM)
Read Article


