How Do I Secure My Linux Server?
Our last article on Ubuntu security suggestions touched on the importance of passwords, user roles, console security, and firewalls. We continue with our last article and while the recommendations below are not unique to Ubuntu specifically (nearly all discussed are considered best practice for any Linux VPS server or dedicated server) but they should be an important consideration in securing your server.
1) Ensure your Server is Up-To-Date
As soon as you can access the server as root, make sure it is up to date.
apt-get update && apt-get upgrade
2) Create a Secondary User and Disable Root Logins
To decrease the possibility of unauthorized access, create a primary user with limited permissions to accomplish specific tasks.
adduser bobAdd this new user to the sudo’ers file, so he can temporarily increase his rights and permissions as needed to accomplish root level tasks.
echo 'Bob ALL=(ALL) ALL' >> /etc/sudoerNext, log out and then SSH back into the server as the new user to ensure that their login works as expected. Once in, confirm they can ‘su’ up to root. Next, login into the server in a second terminal. This is important!
Now, let’s disable the root users SSH login. To accomplish this, we’re going to edit the /etc/ssh/sshd_config file:
vim /etc/ssh/sshd_configChange this line:
#PermitRootLogin yesTo this:
PermitRootLogin noand then restart the SSH service.
/etc/init.d/sshd restart
Stopping sshd: [ OK ]
Starting sshd: [ OK ]
3) Setup SSH Keys
SSH keys allow for you to connect to the server securely with a stored key pair.
This would be an extra step in securing the server to disallow additional access.
SSH into your server as the root user. Next, run:
ssh-keygen -t rsa -C "you@example.com"Press <Enter> to accept the default locations and file names, then enter, and then re-enter a passphrase for your user.
Next, we’ll add your public key to the local authorized_keys file.
cd ~/.sshNext, copy the new public key to the root user’s SSH directory on the server.
cp id_rsa.pub authorized_keys
cd ~/.sshNow you can simply connect with:
scp authorized_keys root@host.servername.com:/root/.ssh/
ssh host.servername.com
4) Check and Configure the Firewall
root@server:~# ufw app list
Available applications:
OpenSSHroot@server:~# ufw status
Status: active
To Action From
-- ------ ----
22/tcp ALLOW Anywhere
22 ALLOW Anywhere
8080/tcp ALLOW Anywhere
80/tcp ALLOW Anywhere
Anywhere DENY 58.218.92.34
80 DENY 202.54.1.5
22 (v6) ALLOW Anywhere (v6)
22/tcp (v6) ALLOW Anywhere (v6)
8080/tcp (v6) ALLOW Anywhere (v6)
80/tcp (v6) ALLOW Anywhere (v6)
5) Limit Open Ports
Most installations of Ubuntu usually have no network services that are listening after the initial install (some hosts may vary). After the server is started, the root user or administrator can define specific services and/or ports to open beyond the defaults.
Testing for open ports can be accomplished using the command netstat -tulpn:
root@server:~# /home# netstat -tulpn
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 69941/sshd
tcp6 0 0 :::22 :::* LISTEN 69941/ss
6) Canonical Kernel Livepatches
The Canonical Livepatch service provides security fixes for most major kernel security issues without requiring a reboot. Ubuntu users can take advantage of the service on up to three nodes for free. All machines covered by an Ubuntu Advantage support subscription can receive Livepatches. More info can be found the at Canonical or Ubuntu websites.
7) Kernel Hardening
The Ubuntu kernel itself has multiple built-in protections enabled to make it more difficult to compromise.
SELinux is a kernel enhancement scheme which implements a Mandatory Access Control (MAC) system to confine applications to a defined set of resources. To install the SELinux package:
apt-get install selinux-basics selinux-policy-default auditdNext, download the load_SELinux_policy script (which is a slightly modified version of the script included in the Ubuntu 'SELinux' package), and place it in the folder.
/usr/share/initramfs-tools/scripts/init-bottom/then, run
update-initramfs -u
Afterward run the command below to configure GRUB, PAM and for /.autorelabel creation.
selinux-activate
Next, reboot the server for the changes to take effect. (it will take some time to label the file systems on boot, then the system will automatically reboot a second time when that task has completed)
Finally, run the command to verify everything has been set up correctly. This will also catch many common SELinux problems.
check-selinux-installation
For further info, see the Debian SELinux wiki.
9) Userspace Hardening
There are multiple hardening features available via Ubuntu's default compiler flags which when building applications utilized via the kernel will provide additional security features.
10) UEFI Secure Boot (amd64)
Beginning with Ubuntu 12.04, UEFI Secure Boot's "enforcing mode" was added to the bootloader and "non-enforcing mode" to the kernel. With this setup, later Ubuntu's versions in which the kernel fail to authenticate will not boot and, kernel modules which fail to validate will not be loaded.
11) Setup 2FA (Two-Factor Authentication)
For an additional layer of protection, you can also set up Two-Factor Authentication in Ubuntu
Step 1: SSH into the server and run this command to install the Google Authenticator app from the Ubuntu repo.
apt-get install libpam-google-authenticator
Step 2: Next, run the google-authenticator command to create a new secret key in your home directory.
google-authenticator
Do you want authentication tokens to be time-based (y/n) y

Your new secret key is: 73GRSXVJNUXZWN2T
Your verification code is 389485
Your emergency scratch codes are:
99536578
44768915
90480600
82281337
56945099
Do you want me to update your "/root/.google_authenticator" file (y/n) y
Do you want to disallow multiple uses of the same authentication
token? This restricts you to one login about every 30s, but it increases your chances to notice or even prevent man-in-the-middle attacks (y/n) y
By default, tokens are good for 30 seconds and in order to compensate for possible time-skew between the client and the server, we allow an extra token before and after the current time. If you experience problems with poor time synchronization, you can increase the window from its default size of 1:30min to about 4min. Do you want to do so (y/n) y
If the computer that you are logging into isn’t hardened against brute-force login attempts, you can enable rate-limiting for the authentication module. By default, this limits attackers to no more than 3 login attempts every 30s. Do you want to enable rate-limiting (y/n) y
Step 3: Next, we edit our sshd_config file:
vim /etc/ssh/sshd_configTo use PAM enable it yes (PAM stands for pluggable authentication module).
UsePAM yesWe then save and close the file (using :wq in VIM) and then restart SSH.
ChallengeResponseAuthentication yes
systemctl restart ssh
Step 4: Next, we need to edit the file where the PAM rules reside for the SSH daemon.
vim /etc/pam.d/sshdAdd the following entry at the end of the file:
auth required pam_google_authenticator.so
Step 5: We then can save and close that file. From now on SSH daemon will use Google Authenticator.
12) Turn Off IPv6
If you are not using IPv6, you can go to the network configuration file and add the following lines to disable it.
vim /etc/sysconfig/network
NETWORKING_IPV6=no
IPV6INIT=no
13) Be Aware/Cautious of All Applications You Install
Each time you install an application, it can add new software alongside that app which may put the server at risk if it allows openings in the server ports.
14) Check and Disable Unneeded Startup Processes
Ubuntu by default will use these run level equivalents in systemd (called targets)
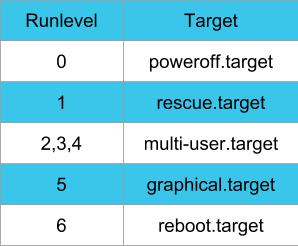
Again, be very sure of the exact settings you need to modify before attempting a change here. Liquid Web servers are already set to have the minimum number of services enabled at startup.
15) Review Logs Regularly
All of Ubuntu’s log files are located in /var/log directory. In that location are specific files for each type of log. Review the logs there to ensure nothing untoward the server is occurring.
To look at a file use the command below. less file.log
Use the arrow keys to scroll up or down. You can also use the head (get the first 10 lines), tail (get the last 10 lines) or, use the grep commands to search through a file.
Backups are your last line of defense in the vent of a catastrophic disaster. We subscribe to the 3-2-1 backup method:
Liquidweb has multiple options for backups available. A full accounting of these backup options can be found on Liquidweb.com. Check out our full line of products today!
Overall, Ubuntu is a mature Linux system in which to securely host your websites. Its unparalleled ability to set up and adapt to many varied configurations remains the best option for those who choose to use a secure, self-managed Dedicated server option that is fast and stable.
If you are a Liquid Web customer and have further security questions, please do not hesitate to reach out and contact our support via a ticket, call or chat! With Liquid Web servers, you are secure! If you're not quite sure about your options, we’re here to help! Talk with a hosting advisor today at 800.580.4985.
Related Articles:
- Using MySQL Command Line to Create a User
- How to Use Disk Quotas in Dedicated Linux Servers With cPanel
- How to Use Disk Quotas in Dedicated Linux Servers with Plesk
- Remove a MySQL User on Linux via Command Line
- Remove Permissions for a MySQL User on Linux via Command Line
- Grant Permissions to a MySQL User on Linux via Command Line

About the Author: David Singer
I am a g33k, Linux blogger, developer, student, and former Tech Writer for Liquidweb.com. My passion for all things tech drives my hunt for all the coolz. I often need a vacation after I get back from vacation....
Our Sales and Support teams are available 24 hours by phone or e-mail to assist.
Latest Articles
How to use kill commands in Linux
Read ArticleChange cPanel password from WebHost Manager (WHM)
Read ArticleChange cPanel password from WebHost Manager (WHM)
Read ArticleChange cPanel password from WebHost Manager (WHM)
Read ArticleChange the root password in WebHost Manager (WHM)
Read Article


