What Is GPG Encryption and Do You Need It?
Introduction

In this article, we will be exploring GnuPG or GPG as it is more commonly known. We will discuss if this software platform is still needed, if it will still be useful in the future, and how to install and utilize it.
GnuPG is a free, open-source command-line tool and application to apply the OpenPGP standards to secure information. GPG itself is distinct from the OpenPGP standard because it uses that protocol to define the canonical format used to encrypt messages, certificates, and signatures via a public keys exchange.
What Goal Does GPG Help Achieve?
GnuPG lets users encrypt, decrypt, and sign communication data using a unique personal key that designates the ownership of the data and security against modification and tampering. It also features a versatile key management system and multiple access modules for many public key directories.
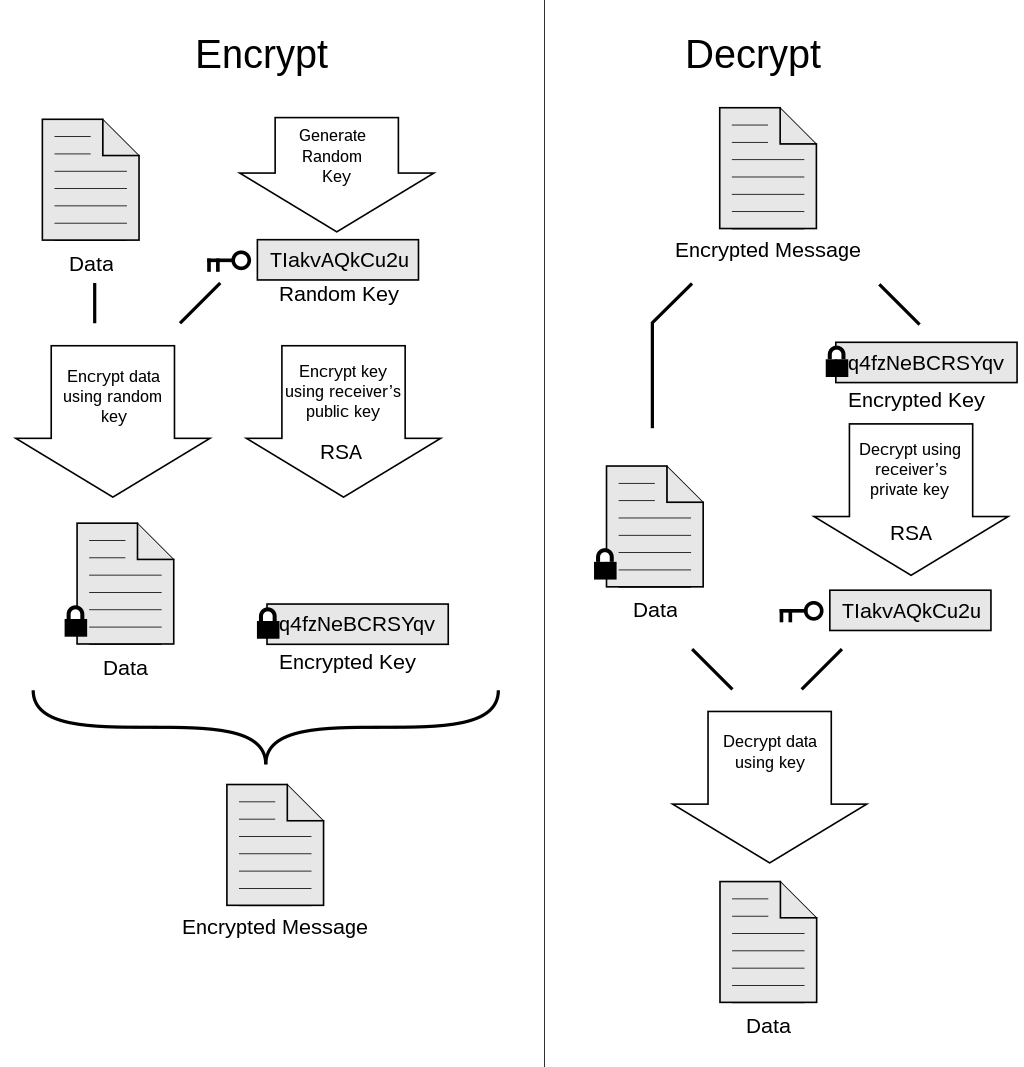
Gnu Privacy Guard (or GnuPG) is the evolution of the earlier encryption standard known as Pretty Good Privacy (or PGP). GPG can use both symmetric and asymmetric encryption to encrypt, decrypt, and sign messages or data using public and private keys. Encryption is an excellent method to ensure that secure communications occur between two parties, easily sharing sensitive data across an insecure network.

“Asynchronous key cryptography” uses both public and private keys to encrypt and decrypt messages. Once published, our public key can enable external users to use that key to encrypt data. The encrypted message is then sent to us, and then we use our private key to decrypt and read it. We then create a message using the original sender’s public key, securely encrypt the message, and send it back. They can then use their private key to decrypt and read the message.
GPG Primary Functions
Integrity & Verification
GPG verifies the owner and sender of the data. If a GPG encrypted reply is sent, it confirms the sender, and lastly, it authenticates that the message has not been modified in any way. It is impossible to decode an encrypted message in a subtle or secretive manner.
Assurance & Security
Assurance does not imply certainty. Nothing in life is certain, and data security is no different. The confidence promised and provided for by GPG means that there exists genuine proof your data is secure. If GnuPG is used correctly, you can be sure of the integrity of your encrypted data. GPG delivers security by encrypting the communication, protecting the message from tampering, and safeguards both the sender and recipient via verification.
Confidentiality and Privacy
GPG ensures privacy as it guarantees both parties that the message is intact as initially created. It also assures us that the sent message is correct and unmanipulated and verifies the receiver gets the accurate message. No unauthorized parties should be able to access or read your data.
What is the Difference Between PGP and GPG?
PGP purchased the rights to the software itself and is now a proprietary solution owned by Symantec. GPG is the open-source equivalent standard to PGP. Functionally, Both formats are virtually identical. OpenPGP is a protocol defined in RFC 4880, which is the open-source standard that both applications utilize for encryption.
Is GPG Still Needed?
Absolutely. GPG is in use today by journalists, business leaders, universities, and others who wish to keep the transmission of messages and data secure. The primary issues with GPG continue to be user acceptance, key handling, and the lack of understanding surrounding the complexity of key creation and exchange.
The main reason that encryption still exists and is widely used today is to protect a user’s communications, data, and privacy. Unfortunately, with today’s ongoing security breaches, 0day vulnerabilities, malicious exploit attempts, and password lists being sold on the dark web, your security is more important than ever. This does not include the ever-widening use of the tracking data pulled from our phone and browser surfing habits and is then sent back to large entities who then sell that information for a profit.
Credit to: commons.wikimedia.org CC BY-SA 3.0
Will GPG be Useful in the Future?
Yes. To calculate the security of existing cryptography systems, “bits of security” denotes the level of protection offered. This measure can be thought of as the number of steps needed to crack a password using the most efficient attacks available. A system using 112 “bits of security” would take approximately 112 steps to breach. This would take the most current computers of today billions of years to break. The National Institute of Standards and Technology currently endorse a minimum of 112 bits of security using one of the NIST-approved algorithms.
With the rise of quantum computing, many question the security and protection level of the currently used systems like AES-256 and RSA-2048. In review, AES-256 now provides the best level of protection until newer systems arise. In the future, advances in quantum computing will make the current cryptography schemes ineffective. Work at NIST is progressing on new methods and approaches as we move into a post-quantum state. The projected timeline for completing a draft for the NIST project is expected to be available somewhere between 2022-2024.
How to Install GPG
The installation process for GPG software is very straight forward on almost all types of systems in use today. Installing GPG from a source compile can be challenging as the following dependencies need to be met before installation: libpcsclite libpcsclite-dev. Once those programs are installed, the source files should be downloaded and installed using the typical ./configure, make, make install commands. The following install processes for various platforms are denoted below.
Ubuntu/Debian
root@host:~$ apt-get install gnupgCentOS/Redhat
root@host:~$ yum install gnupgWindows
The defactos standard for using GPG on Windows is via the GPGP4Win application. Simply download and install the program.
macOS
GPG can be installed on macOS using either GnuPG for OS X or GPG Suite. To install, download the .dmg and then double-click on the file to run the installer.
How Do I Use GPG?
Create Keys
Typically after installing the software, the first step is to set up a keypair. A keypair consists of both public and private keys. During the creation process, a passphrase is required to complete the setup.
Once this and other personalized data is added, random information from your system is collected to create the keypair. When the process completes, the created keys should reside in the .gnupg folder in your home directory.
Backup and Share
Next, we should make a backup of our keys along with our passphrase in a secure location. We can then share our public key to keyservers, add it to an email signature, or even add it to a blog post. Several well-known keyservers are listed below:
Send & Receive Messages
The basic process for using GPG is as follows. This assumes that both users have GPG installed and set up correctly.
- User 1 wants to send a private message to User 2
- User 1 locates User 2’s public key
- User 1 writes a message to User 2 and uses their public key to encrypt the message
- User 1 sends the encrypted message to User 2
- User 2 receives the message and uses his private key to decrypt the message
- User 2 locates User 1’s public key and uses it to encrypt and send a reply to User 1
- User 1 received the message and used their private key to decrypt the message from User 2
This transaction is called Asymmetric Encryption. It is widely used in multiple applications today.
Conclusion
GPG/PGP has a long and distinguished history going back more than 20 years. Some may say that GPG is an outdated method of privacy protection. We only have to review its recent usage in protecting dissidents, human rights activists, business leaders, journalistic sources, government information, and many other whistleblowers who rely on its battle-tested use. As we can see, GPG is still widely used today, and its usage is expected to continue long into the future.
Related Articles:

About the Author: David Singer
I am a g33k, Linux blogger, developer, student, and former Tech Writer for Liquidweb.com. My passion for all things tech drives my hunt for all the coolz. I often need a vacation after I get back from vacation....
Our Sales and Support teams are available 24 hours by phone or e-mail to assist.
Latest Articles
How to use kill commands in Linux
Read ArticleChange cPanel password from WebHost Manager (WHM)
Read ArticleChange cPanel password from WebHost Manager (WHM)
Read ArticleChange cPanel password from WebHost Manager (WHM)
Read ArticleChange the root password in WebHost Manager (WHM)
Read Article


