How to Repair the DNS DCV Error in cPanel
How Using Cloudflare Affects AutoSSL in cPanel
We have provided information about Cloudflare, AutoSSL, and the advantages of utilizing those services in previous articles. In this article, we will focus on solving one of the specific issues seen when using Cloudflare and AutoSSL together on a cPanel/WHM server. These services function admirably in almost every setting and can be relied upon to deliver the service they advertise. However, in certain situations, services can clash through no fault of their own.
What is Cloudflare?
Cloudflare is an internet service company that provides a CDN (content delivery network), DDoS mitigation, Internet security, distributed DNS (domain name server), and other services. The Cloudflare service sits between the user and the website hosting provider while acting as a reverse proxy for websites connecting the two.
What is AutoSSL?
AutoSSL is a free alternative SSL certificate that precludes the purchasing of a yearly SSL certificate. It is usually an account-wide setting that is enabled or disabled within the user’s management panel. When AutoSSL is enabled, a daily cron replaces self-signed SSL certificates expired (or soon to be expired) with new Sectigo or Let’s Encrypt certificates. With AutoSSL, local websites are automatically secured with a free, Domain Validated SSL certificate. cPanel’s AutoSSL uses both the Sectigo provider module and a Let's Encrypt™ plugin, which can be downloaded.
What Does the Error Look Like?
When using AutoSSL within WHM and AutoSSL tries to renew an SSL automatically, if the domain is configured to use Cloudflare, an error like the one below is seen can occur. (This is a portion of a log file in which the error is seen.)
12:44:11 PM ERROR Local DNS DCV error (example.com): The DNS query to “_cpanel-dcv-test-record.example.com” for the DCV challenge returned no “TXT” record that matches the value “_cpanel-dcv-test-record=g5EgawFWDq0V8PTUN5gspeRpOP_ckd2vcyofocOtXIRr9WcAiqj5qQfWYvaBE8fo”. ERROR Local DNS DCV error (www.example.com): The DNS query to “_cpanel-dcv-test-record.example.com” for the DCV challenge returned no “TXT” record that matches the value “_cpanel-dcv-test-record=g5EgawFWDq0V8PTUN5gspeRpOP_ckd2vcyofocOtXIRr9WcAiqj5qQfWYvaBE8fo”. Local DNS DCV OK: *.example.com (via example.com) Analyzing “example.com”’s DCV results …12:44:11 PM ERROR Impediment: NO_UNSECURED_DOMAIN_PASSED_DCV: Every unsecured domain failed DCV.Why Does This Error Occur?
The primary method for DNS validation uses HTTP. Still, cPanel takes the extra step and uses an additional local DNS Domain Control Validation (or DCV) process to verify and prove a domain is valid to the certificate authorities.
As part of the DCV process, a DNS record is automatically added to the zone file of a domain on a cPanel & WHM server. This record is added/removed/modified automatically as needed by cPanel/WHM. This issue arises when cPanel cannot retrieve the needed validation due to the domain nameservers being used at Cloudflare, which prevents the validation process during the “AutoSSL” renewal process.
How Do I Know if I am Using Cloudflare?
There are 2 methods we can easily use to verify if our domain is indeed using Cloudflare to handle its DNS, using the command line.
Command Line
Dig
root@host:~# dig liquidweb.com
; <<>> DiG 9.16.1-Ubuntu <<>> liquidweb.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 53640
;; flags: qr rd ad; QUERY: 1, ANSWER: 5, AUTHORITY: 0, ADDITIONAL: 0
;; WARNING: recursion requested but not available
;; QUESTION SECTION:
;liquidweb.com. IN A
;; ANSWER SECTION:
liquidweb.com. 0 IN A 67.225.187.61
ns.liquidweb.com. 0 IN A 69.16.222.254
ns1.liquidweb.com. 0 IN A 69.16.223.254
ns.liquidweb.com. 0 IN AAAA 2607:fad0:0:8917::a
ns1.liquidweb.com. 0 IN AAAA 2607:fad0:0:8927::a
;; Query time: 40 msec
;; SERVER: 192.168.238.49#53(192.168.238.49)
;; WHEN: Fri Nov 20 08:45:21 EST 2020
;; MSG SIZE rcvd: 214
root@host:~#Nslookup
root@host:~# nslookup liquidweb.com
Non-authoritative answer:
Name: liquidweb.com
Address: 67.225.187.61
Name: ns.liquidweb.com
Address: 69.16.222.254
Name: ns1.liquidweb.com
Address: 69.16.223.254
Name: ns.liquidweb.com
Address: 2607:fad0:0:8917::a
Name: ns1.liquidweb.com
Address: 2607:fad0:0:8927::a
root@host:~#Internal Tools
In manage.liquidweb.com, we have the ability to set up Cloudflare on our account. Our knowledgebase article about Cloudflare outlines that process.
External Tools
We can also use third-party tools like these:
When using the ICANN tool, type your domain name and click the lookup button. The results will be similar to the image below. The area outlined in red is what we are most interested in.
In this case, the specific record types:
- Name: example.com
- Type: Nameservers
- Data: gabe.ns.cloudflare.com & ivy.ns.cloudflare.com
The Name indicates the actual name of the domain we entered in the search bar.
The Type is the type of record we are looking to find.
Data will be the name of the nameservers. Cloudflare typically uses the following format:
Any domain that uses Cloudflare will have their NS records as follows:
- xxxx.ns.cloudflare.com
- xxxx.ns.cloudflare.com
Verify Nameserver Info
To verify if our domain is using Cloudflare, we need to check if the Name Servers are pointing to Cloudflare.
Going back to WHM-Cpanel and AutoSSL, if you tried to renew the SSL in your domain and noticed an error like this:
12:44:11 PM ERROR Local DNS DCV error (example.com): The DNS query to “_cpanel-dcv-test-record.example.com” for the DCV challenge returned no “TXT” record that matches the value “_cpanel-dcv-test-record=g5EgawFWDq0V8PTUN5gspeRpOP_ckd2vcyofocOtXIRr9WcAiqj5qQfWYvaBE8fo”. ERROR Local DNS DCV error (www.example.com): The DNS query to “_cpanel-dcv-test-record.example.com” for the DCV challenge returned no “TXT” record that matches the value “_cpanel-dcv-test-record=g5EgawFWDq0V8PTUN5gspeRpOP_ckd2vcyofocOtXIRr9WcAiqj5qQfWYvaBE8fo”.
Local DNS DCV OK: *.example.com (via example.com)
Analyzing “example.com”’s DCV results …
12:44:11 PM ERROR Impediment: NO_UNSECURED_DOMAIN_PASSED_DCV: Every unsecured domain failed DCV.It means AutoSSL tried to renew it, but since CloudFlare proxies (hides), the connection between the server and any request being made. AutoSSL could not get some text files it temporarily places on the server to test if it is actually hosted on the server.
How to Address the Error
We have several options in addressing this problem.
- We can purchase a stand-alone SSL certificate
- We can use Cloudflare’s SSL Option without AutoSSL
- We can use the cPanel SSL option without Cloudflare
- We can temporarily pause Cloudflare and then update the AutoSSL certificate
We choose option 4 in this case. Addressing this problem is pretty straightforward.
Step 1. Pause Cloudflare
We begin by logging into the cloudflare.com dashboard that controls the DNS for the domain and pauses Cloudflare for a moment.
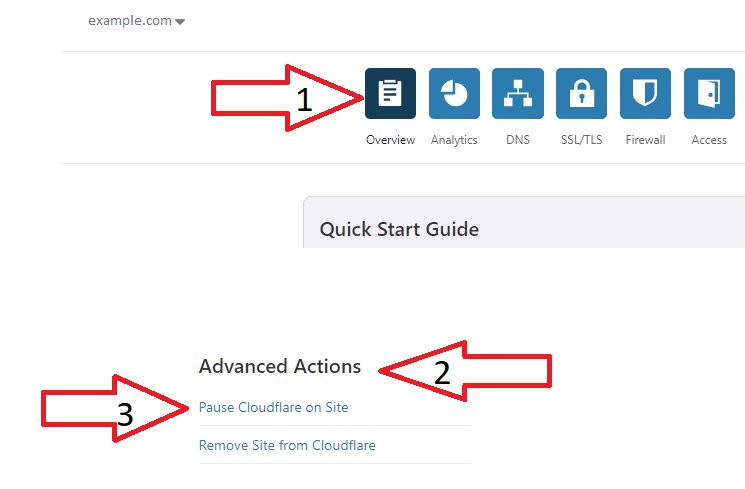
In the top left, go to “Overview.” Then find the “Advanced Options” section, and in the bottom right, click on “Pause Cloudflare on Site.”
Step 2. Run AutoSSL
Once we have accomplished this, we can rerun AutoSSL to issues the certificate. This will ensure our domain passes Domain Control Validation.
Using AutoSSL in WHM-Cpanel
While we are on this topic, we will demonstrate how to use the AutoSSL feature in WHM.
- First login to your server WHM.
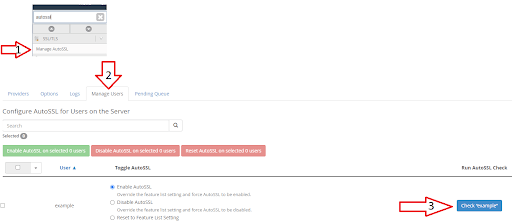
2. In the search bar type “autossl” and click on “Manage AutoSSL”
3. This will take us to a new screen. In that screen locate the “Manage Users” tab.
4. Find the cPanel user for your domain on the right and click on check “example” in blue.
5. It will now issue an SSL for the domain.
Great! We just renewed the SSL.
Verify SSL
So, where do we go to verify it actually worked? We will check the logs, of course!
- Go back to the “Manage AutoSSL” option in WHM.
2. Click on the “Logs” tab in the middle.
3. Click on “Refresh” so you can see the latest logs.
4. Click on the latest log available.
5. Click on “View Log”, to view the log you selected.
The output of the log is usually long, but it will show an entry something akin to the following entry at the very bottom of the log.
The certificate is available. The system will now attempt to install it.
12:49:02 PM SUCCESS The certificate is now installed!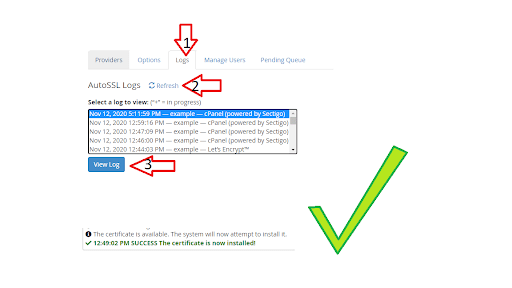
Conclusion
The free SSL from WHM should be renewed every 3 months. The other workaround would be ordering a paid SSL for one year. If we choose to order an SSL to avoid having to do this every 3 months we have 2 options.
- Standard SSL that covers your domain.com and the subdomain www.domain.com for $50/Year.
- A Wildcard SSL. This SSL will cover your main domain and any subdomain for $150/Year.
If you are unsure what’s the best option for you is, just contact us and we will make sure you get the best solution for your business, you can read more about ordering an SSL in this article.
How Can We Help?
Related Articles:

About the Author: Nelson Alba
Nelson Alba is a former Support Technician at Liquid Web.
Our Sales and Support teams are available 24 hours by phone or e-mail to assist.
Latest Articles
How to use kill commands in Linux
Read ArticleChange cPanel password from WebHost Manager (WHM)
Read ArticleChange cPanel password from WebHost Manager (WHM)
Read ArticleChange cPanel password from WebHost Manager (WHM)
Read ArticleChange the root password in WebHost Manager (WHM)
Read Article


