II. How to Disable SSLv3 for Exim and Protect Your WHM/cPanel Server from POODLE
There’s a new POODLE in town, but unfortunately it’s not the kind of pooch you want around. POODLE stands for Padding Oracle On Downgraded Legacy Encryption. It’s an exploit that, although not considered to be as serious as Heartbleed, is one that should still be protected against. For more information read the Google Blog.
Fortunately, protecting your WHM/cPanel server is easy. Just follow the steps below:
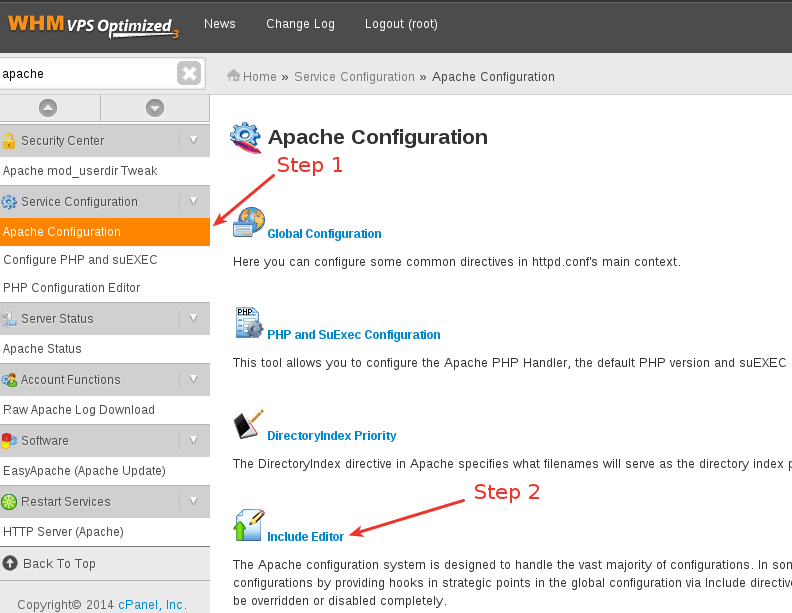
Login to WHM, open up the Apache Configuration screen, and click on Include Editor
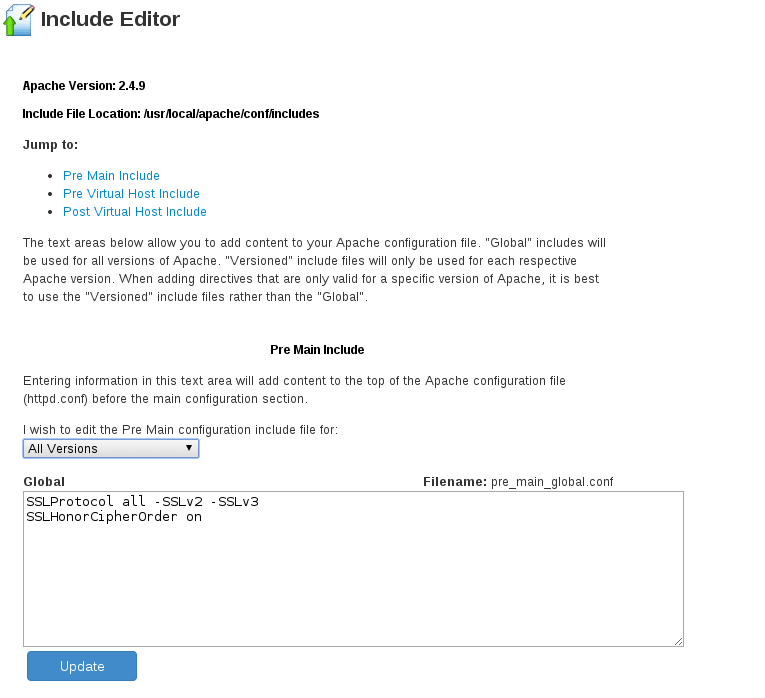
Under Pre Main Include, select All Versions. This way your server will be protected if you change your version of Apache. When selected, enter the following into the text box for CentOS/RHEL 6.x:
SSLHonorCipherOrder On
SSLProtocol -All +TLSv1 +TLSv1.1 +TLSv1.2
When selected, enter the following into the text box for CentOS/RHEL 5.x:
SSLHonorCipherOrder On
SSLProtocol -All +TLSv1
…and then click Update. Once you click update, you’ll be prompted to restart Apache; do so at this time.
To verify you’re covered, run the following command in a terminal as root:
openssl s_client -connect www.yourssldomain.com:443 -ssl3
You’ll know you’ve successfully disabled SSLv3 and protected yourself from the attack POODLE if you see a response similar to this:
CONNECTED(00000003)
140421693269648:error:14094410:SSL routines:SSL3_READ_BYTES:sslv3 alert handshake failure:s3_pkt.c:1275:SSL alert number 40
140421693269648:error:1409E0E5:SSL routines:SSL3_WRITE_BYTES:ssl handshake failure:s3_pkt.c:598:
Thank you to Jason Gillman for providing the information essential to this tutorial. If you still need assistance with this problematic pooch, please contact our Heroic Support team!
Related Articles:

About the Author: J. Mays
As a previous contributor, JMays shares his insight with our Knowledge Base center. In our Knowledge Base, you'll be able to find how-to articles on Ubuntu, CentOS, Fedora and much more!
Our Sales and Support teams are available 24 hours by phone or e-mail to assist.
Latest Articles
Change cPanel password from WebHost Manager (WHM)
Read ArticleChange cPanel password from WebHost Manager (WHM)
Read ArticleChange cPanel password from WebHost Manager (WHM)
Read ArticleChange cPanel password from WebHost Manager (WHM)
Read ArticleChange the root password in WebHost Manager (WHM)
Read Article


