Alert Logic Security and Compliance Suite
Introduction
Intrusion detection systems (IDSs) are an ever-present requirement in a cybersecurity infrastructure to ensure a server or internal network is protected. An intrusion detection system is either a hardware device or software program that actively monitors a server or group of servers for network policy violations or malicious activity. Any suspicious activity, attempted attack, or policy violation is reported and logged to a centrally located security information and event management (SIEM) system database, or directly to a security administrator for further review. This article explores Liquid Web’s intrusion detection product called Alert Logic Security and Compliance Suite.
What is Alert Logic Security and Compliance Suite?
Liquid Web’s Alert Logic Security and Compliance Suite is a fully managed, white-glove intrusion detection system that functions on an appliance/agent mode on a client’s local network. It includes real-time activity reporting, around-the-clock incident response, verification, and guidance on remediation operations. The suite can also help a business satisfy security compliance standards, including:
- PCI DSS - The Payment Card Industry Data Security Standards is used by businesses that handle credit card transactions to ensure security measures are in place.
- HIPAA - The Health Insurance Portability and Accountability Act ensures health records are securely protected.
- HITECH - The Health Information Technology for Economic and Clinical Health Act encourages creating and applying health information technology.
- GDPR - The General Data Protection Regulation comprises the European Union law on data protection and privacy.
Once the solution is in place, the service is designed to be nearly free of human intervention.
Who is Alert Logic?
Alert Logic is an industry-leading cybersecurity firm partnered with Liquid Web that offers a mature and proactive Managed Detection and Response (MDR) solution. Alert Logic was founded in 2002 after providing an innovative public cloud SaaS (Software-as-a-Solution) security model. This platform includes an intrusion detection system that is integrated with a 24/7 Security Operations Center Service. In 2018, they introduced their groundbreaking Managed Detection and Response solution.
What is MDR?
The Managed Detection and Response system delivers around-the-clock threat detection, active monitoring, and 24/7 response services to clients. MDR leverages advanced AI-based technologies, including analytics, threat intelligence, human expertise incident investigation, and a framework deployed at both the host and network layers.
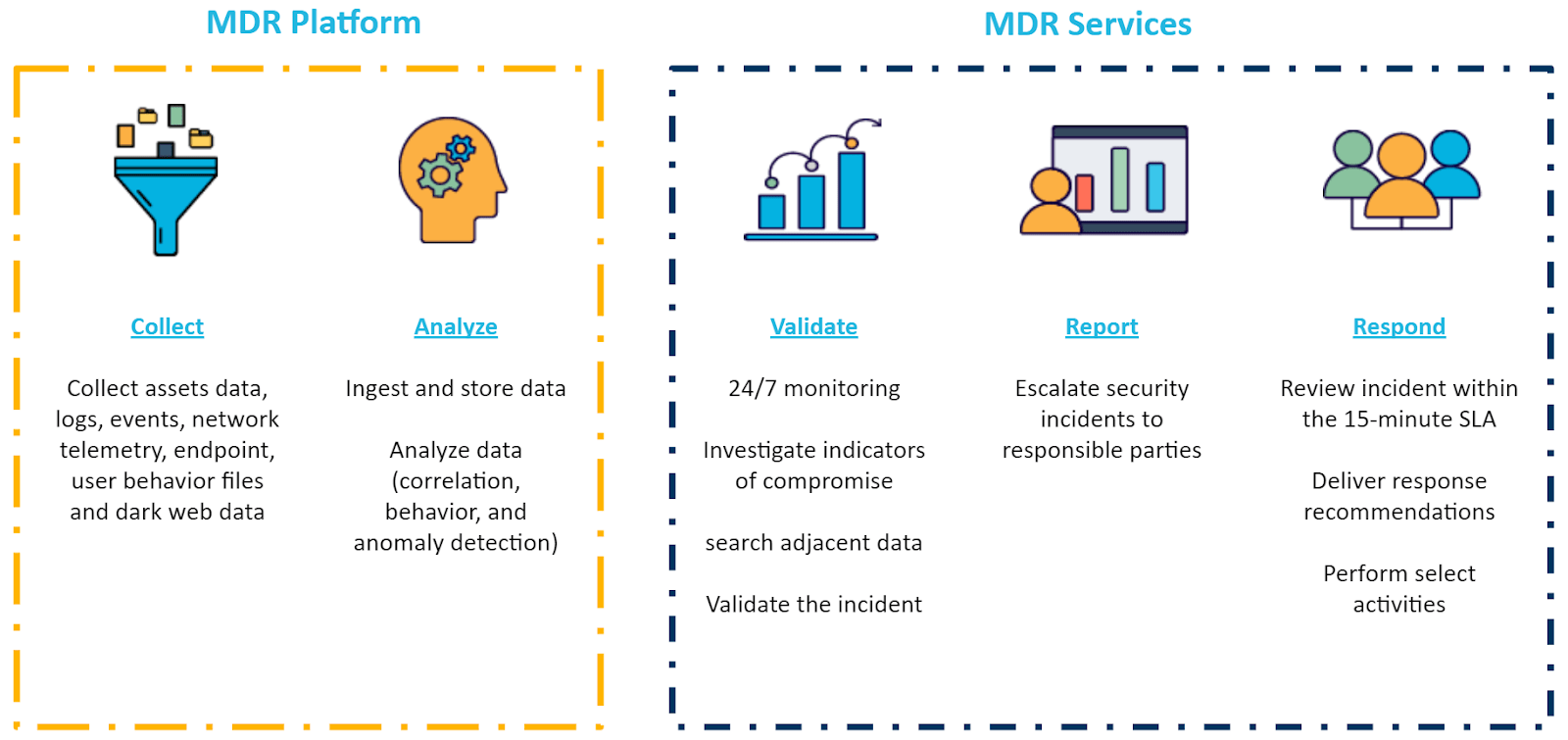
The MDS solution’s overall goal is to continuously audit, review, assess, and examine all the organization’s assets. This increased transparency allows for greater visibility into any potential threats that malicious individuals might exploit. In the event of an incident, a review immediately takes place, and a custom report is sent in an easy-to-understand format that provides credible information and possible impact to business processes. This report includes contextually related information surrounding the attack and how it is addressed.
Additionally, this advanced technology is augmented with experienced human intelligence to ensure any disparities that may exist between the AI and the framework of the system are proactively addressed. Coordinated security analysis and threat management indicators are continually added as new hazards emerge and updated vulnerability information becomes available.
Features of Alert Logic Security and Compliance Suite
Alert Logic provides these unique and well-defined features:
- A dynamic, always-on IDS.
- Exhaustive security monitoring and comprehensive incident management.
- Guaranteed endpoint protection against malicious code, malware, and bots.
- Aggressive vulnerability scanning measures.
- Thorough online reporting provided through a fully-featured dashboard. Note: Independent on-demand security scans are also available via the secure dashboard.
- Provides extensive monitoring, logging, and management capabilities.
- Robust 24/7/365 support provided by expertly trained Alert Logic professionals who are well versed in security protocol best practices.
Benefits of Alert Logic Security and Compliance Suite
- Threat Protection - Reduce the risks to your business with a comprehensive security suite that includes unlimited vulnerability scanning, spans the entire attack surface, and operates at scale.
- Threat Intelligence - Get insight into the threats your infrastructure faces through automated log management and detailed reporting based on industry data and expert analysis.
- Compliance Best Practices - Get the tools you need to maintain compliance across multiple mandates, including PCI-DSS, HIPAA/HITECH, GDPR, SOX, SOC 2, ISO, and NIST.
- Expert Support - Alert Logic's Security Operations Center provides 24/7/365 support by expert security professionals for incident verification, remediation guidance, and more.
Vulnerability and Assessment Scanning vs Alert Logic
The difference between Liquid Web's Vulnerability Assessment Scans Powered by Clone Systems and Alert Logic is that the vulnerability assessment is a monthly scan executed externally from the server. These scans provide customers with a detailed evaluation of any potential security risks and known vulnerabilities. Alert Logic is a continuous scan of the systems incorporated into the plan and provides clients with immediate detailed assessments.
The monthly vulnerability assessment scans can be implemented as a stand-alone product or as part of our ServerSecure+ package. The results of these scans are retrieved and sent to the client via a support ticket. The vulnerability assessment scans are conducted by the same vendor that provides our PCI Compliance scans. In comparison, Alert Logic is a stand-alone product used to provide instant or on-demand scans. Results are more detailed and aided by the Alert Logic professionals who assist and advise on any findings.
The vulnerability assessment scans should not be confused with a PCI DSS scan, which is intrinsically distinct in nature and focuses on different criteria. The pass/fail nature of the vulnerability assessment scan does not in any way impact or affect the PCI certification of the server's security configuration or compliance readiness. Alert Logic scans can be used to aid in securing PCI compliance.
Scan Types
| Scan Type | Description |
|---|---|
| Internal | Runs from an Alert Logic appliance within an environment. If a user provides credentials, Alert Logic logs into each host and performs a comprehensive vulnerability check. If no credentials are provided, Alert Logic performs as many checks as possible. |
| External | Runs from an Alert Logic data center. It simulates an external attack and identifies any potential issues these types of attacks impose. |
| Discovery | Applies to data center deployments only. It scans for new assets or asset changes on your networks. |
| PCI | A special type of external scan used specifically for Payment Card Industry compliance requirements. |
Best Practice
Alert Logic creates a default scan schedule when a deployment is completed. Users can edit or create additional scheduled scans. When configuring a scan, users should follow these guidelines to produce successful scan results and maximize the effectiveness of Alert Logic:
- Run scans during off-peak activity hours.
- Do not scan during server maintenance.
- For best results, run a scan after applying any patches or updates.
- Scan new servers prior to use. The time it takes for an unpatched or unprotected server to be infected can be less than an hour.
- Scan frequently. Create a reasonable scan schedule that can be adhered to.
- Run internal and external scans at least once a week and to completion. Incomplete and infrequent scans will miss undetected vulnerabilities.
- Scan common TCP and UDP ports once a week and all other ports every so often.
Prerequisites
Please review the following prerequisites before enabling Alert Logic:
- A Linux or Windows-based operating system. The Linux agent includes both RedHat and Debian-based software.
- Adequate bandwidth to collect multiple data streams for analysis, including log messages, network traffic, metadata, and other host-based identification information.
- Implement Alert Logic firewall rules.
Dashboard Access
Alert Logic provides five roles, each with a different permission level that is assigned to user accounts within its dashboard:
- Administrator - Provides full access to every aspect of the system.
- Owner - Allows full access but cannot create or remove users.
- Power User - Full access within a managing account, without user management.
- Support/Care - Provides read access for the managing account and all its managed accounts.
- Read Only - Allows read-only access for the managing account.
Multifactor authentication provides additional account security via the use of One-Time Passwords (OTP). Clients can download OTP apps like Google Authenticator, Authy, or 1Password from their preferred app store.
Conclusion
The Alert Logic Security and Compliance Suite is an elevated security option available to enhance an existing security profile. It is a powerful and accomplished system that has been battle-tested across multiple platforms and systems. Alert Logic’s continuous asset discovery and visibility features improve the protection of deployments. Its regularly scheduled vulnerability scans help detect and remediate exposure to multiple vulnerabilities, critical exploits, and malware strains that can cripple a business. Reach out to a Liquid Web solutions expert today to learn more about this necessary product to safeguard and better secure your infrastructure.
Related Articles:
Our Sales and Support teams are available 24 hours by phone or e-mail to assist.
Latest Articles
How to use kill commands in Linux
Read ArticleChange cPanel password from WebHost Manager (WHM)
Read ArticleChange cPanel password from WebHost Manager (WHM)
Read ArticleChange cPanel password from WebHost Manager (WHM)
Read ArticleChange the root password in WebHost Manager (WHM)
Read Article


