
How to Respond to a Cyberattack
Key Facts Companies Should Consider
Since the onset of the pandemic, the race towards digital transformation hasn’t slowed down. But as organizations begin to migrate to the cloud, adopt work-from-home policies, and enact bring-your-own-device (BYOD) programs to accommodate a distributed workforce, their attack surface continues to expand.
As remote workers move further away from the edge of secured networks and use unsanctioned personal devices to access corporate data, resources, and enterprise applications, organizations must implement the proper security measures to stay protected against financially-motivated cyber criminals.
Unfortunately, many companies have let cybersecurity fall by the wayside in their rush to deploy new digital business models, as successful cyberattacks are on the rise. For example, brute force attacks, credential stuffing, and social engineering attacks (primarily through phishing emails) continue to be key avenues for cyber criminals to attack an organization.
To help build awareness around the growing and ongoing threat of cyberattacks, we surveyed 500 participants who have experienced some form of cyberattack between June 1, 2020, and May 31, 2021.
The “Liquid Web Cybersecurity Actions and Attitudes Study” was launched to understand specific consequences of these attacks, how they responded after an attack, and gauge preparedness against future attacks.
Some of the most eye-opening findings of the survey include:
- 21.2% experienced affected servers or systems for a 1 month or longer.
- 21.4% lost between $100,000 to over $1 million in revenue.
- 62.4% hired more staff to support against future cybersecurity attacks.
- 76.6% invested more money in protective software and programs after the attack.
- Over 2/3 of respondents stated cybersecurity increased in priority.
- 36.4% reported that cybersecurity is now their top priority after the attack.
- 50.8% identified as workers of medium-sized businesses (100-999 employees).
Before breaking down these key findings, it’s best to gain a firm understanding of just what a cyberattack is.
What Is a Cyberattack?
A cyberattack is any attempt by a cybercriminal to obtain unauthorized access to a computer, computer system, or network. These attacks can be used for various purposes, including to disable or control computer systems, or to manipulate or steal confidential data.
Common types of cyberattacks include phishing, malware, ransomware, and distributed denial of service (DDoS). According to the FBI’s Internet Crime Complaint Center (IC3), cyberattacks accounted for $4.2 billion in lost revenue in 2020, and the top cyberattacks were phishing-based scams.
Details of the Liquid Web Cybersecurity Actions and Attitudes Study
In the Liquid Web Cybersecurity Actions and Attitudes Study, we only surveyed participants in the U.S. who claimed they experienced a cyberattack sometime throughout 2020 to early 2021. Some of the key demographics of our study group include:
- Age groups:
- 18 to 24 (11.0%)
- 25 to 34 (20.2%)
- 35 to 44 (50.2%)
- 45 to 54 (10.8%)
- > 54 (7.8%)
- Gender:
- Male: 290 (58%)
- Female: 210 (42%)
- Organization roles:
- Technical Staff: 186 (37.2%)
- President/CEO/Chairperson: 77 (15.4%)
- C-Level Executive: 132 (26.4%)
- Chief Technical Officer: 24 (4.8%)
- Director: 81 (16.2%)
Table of Contents
1. Phishing remains a go-to, but brute force attacks are a common runner-up
2. 21.2% reported an impact of 1 month or longer
3. Financial services, healthcare, and government sectors were most likely to not know what kind of attack impacted their organization
4. Over 76.6% increased spending on protective software and programs since their cyberattack
5. Nearly all participants experienced revenue loss regardless of whether an attack was successful
6. Cybersecurity priorities remained about the same for nearly 20% of participants after an attack
7. 3 out of 4 respondents invested much more in cybersecurity education protocols and rollouts because of the attack
8. Middle management employees are more likely to be targeted in a cyberattack
9. Software/tech companies have an abundance of confidence in their cybersecurity approaches
10. The job market remains bright for cybersecurity professionals
11. Ransomware wasn’t as prevalent as other studies suggest
1. Phishing remains a go-to, but brute force attacks are a common runner-up
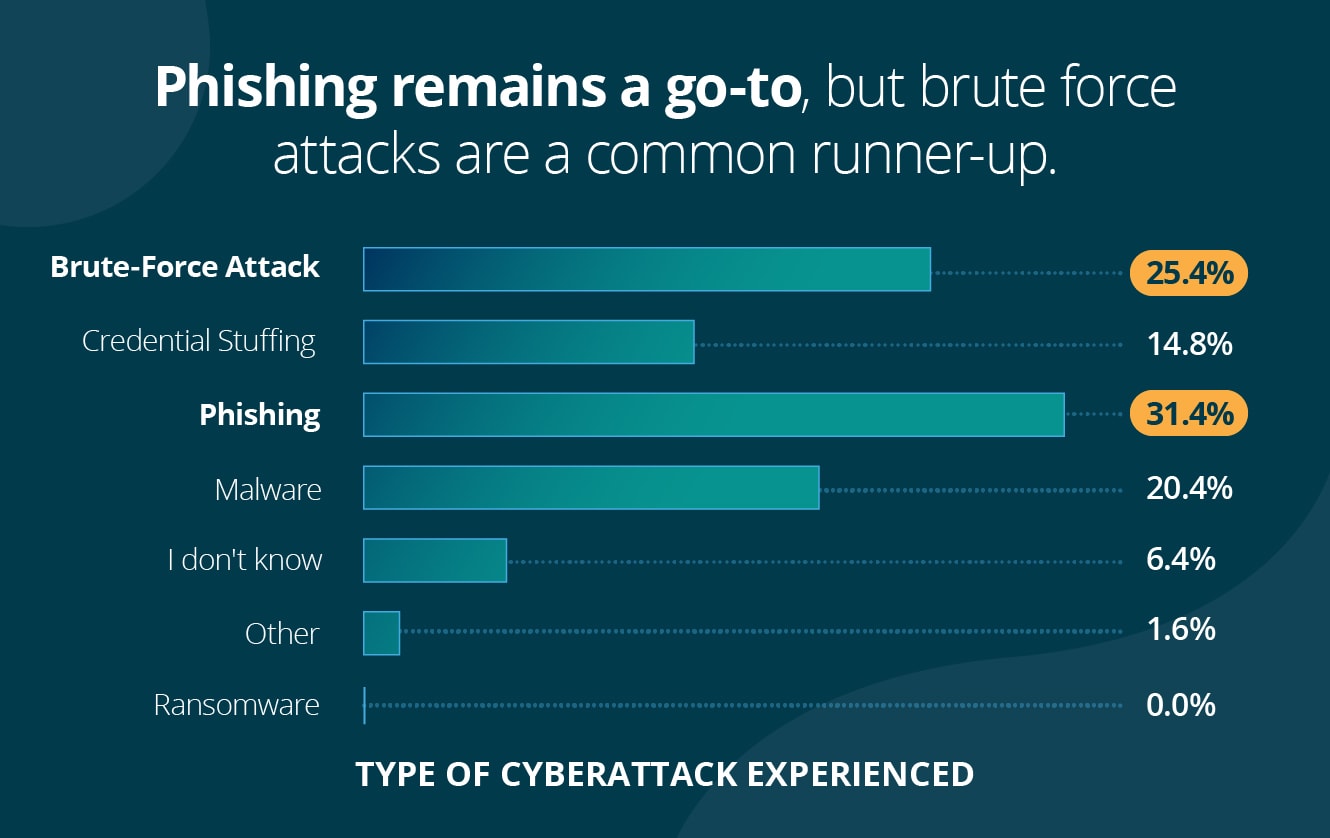
Phishing remains one of the top action varieties in breaches, which follows suit with findings from Verizon’s 2021 Data Breach Investigations Report and the impact of COVID-19-related phishing scams. Brute-force attacks—which often consist of cybercriminals using different combinations of usernames and passwords until they find one that works—comes in a close second, with malware and credential stuffing following.
- Phishing: 31.4% (157)
- Brute-force attack: 25.4% (127)
- Malware: 20.4% (102)
- Credential stuffing: 14.8% (74)
- I don’t know: 6.4% (32)
- Other: 1.6% (8)
- Ransomware: 0.0% (0)
2. 21.2% reported an impact of 1 month or longer
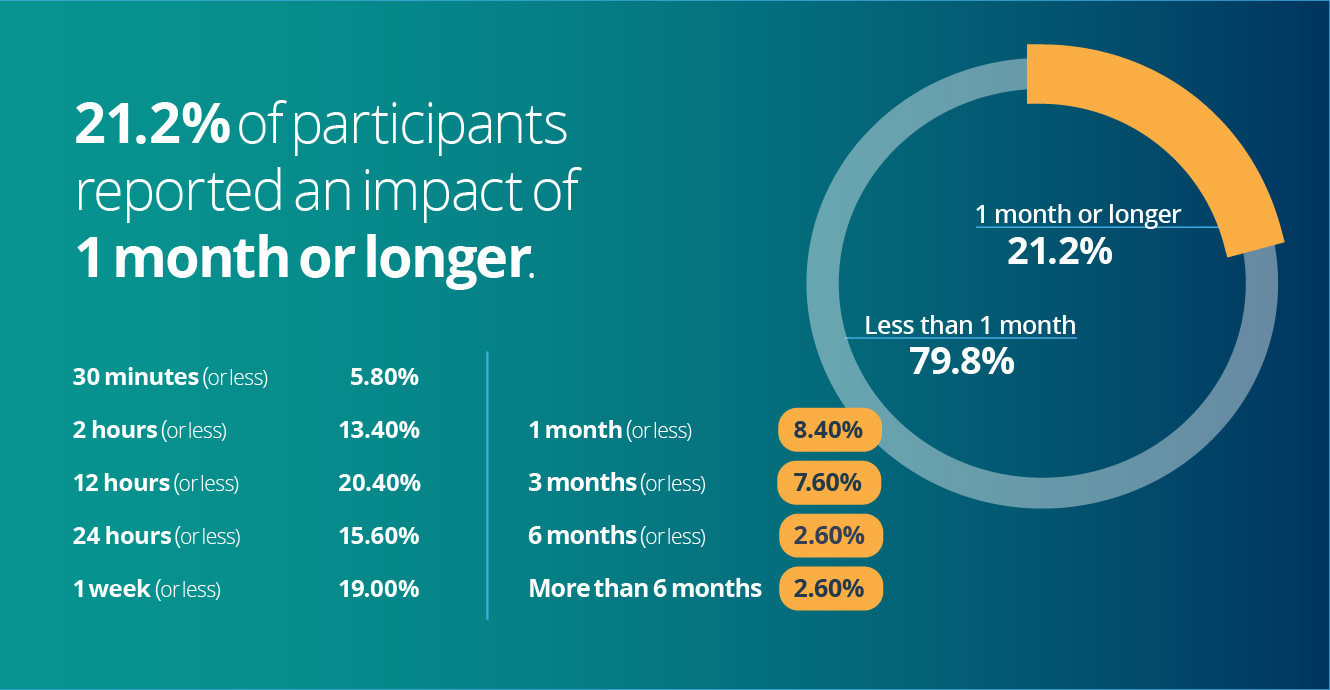
Although most participants reported that a cyberattack’s impact on their servers or systems lasted for 12 hours or less, 21.2% claimed the impact exceeded 1 month—which is a significant amount of time. Even more shocking, some of those experienced an impact of 6 months or more.
- 30 minutes or less: 5.8% (29)
- 2 hours or less: 13.4% (67)
- 12 hours or less: 20.4% (102)
- 24 hours or less:15.6% (78)
- 1 week or less: 19% (95)
- 1 month or less:8.4% (42)
- 3 months or less:7.6% (38)
- 6 months or less:2.6% (13)
- More than 6 months: 2.6% (13)
3. Financial services, healthcare, and government sectors were most likely to not know what kind of attack impacted their organization
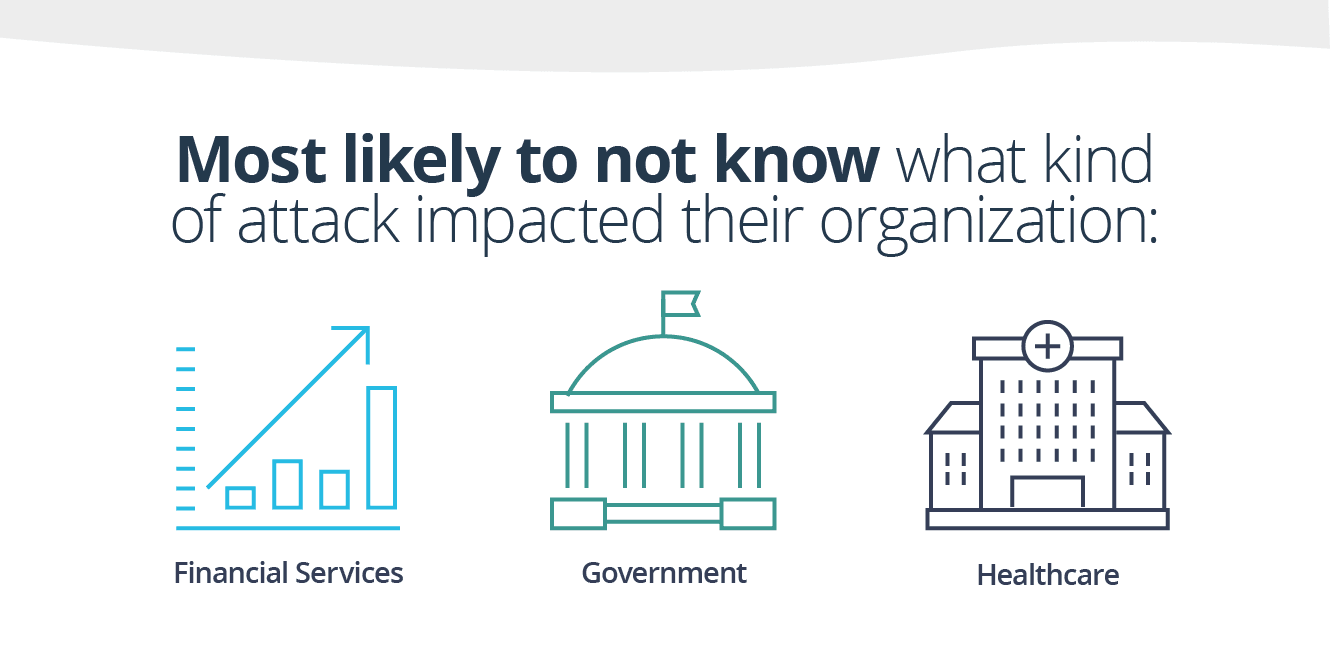
Out of the 500 participants we surveyed, 32 claimed they did not know what type of cyberattack their organization was subjected to. Within this group, the financial services, healthcare, and government sectors were the most common to report this lack of visibility.
Interestingly, participants from all three of these sectors made opposing claims surrounding their cybersecurity efforts:
- 45.64% claimed they were “very prepared” to protect against the increased cybersecurity risks of a remote workforce.
- 50.26% claimed they were “very confident” in their organization’s ability to mitigate future cybersecurity attacks.
- 37.44% claimed cybersecurity increased in priority over the last 12 months but it was not a focus.
While these three sectors were the most likely to not know what kind of attack they experienced, it’s worth noting how their perceived confidence and preparedness for future attacks remains high. Since understanding all possible vulnerabilities is a key aspect of cybersecurity, this demonstrates how reality and perception don’t always line up.
4. Over 76.6% increased spending on protective software and programs since their cyberattack
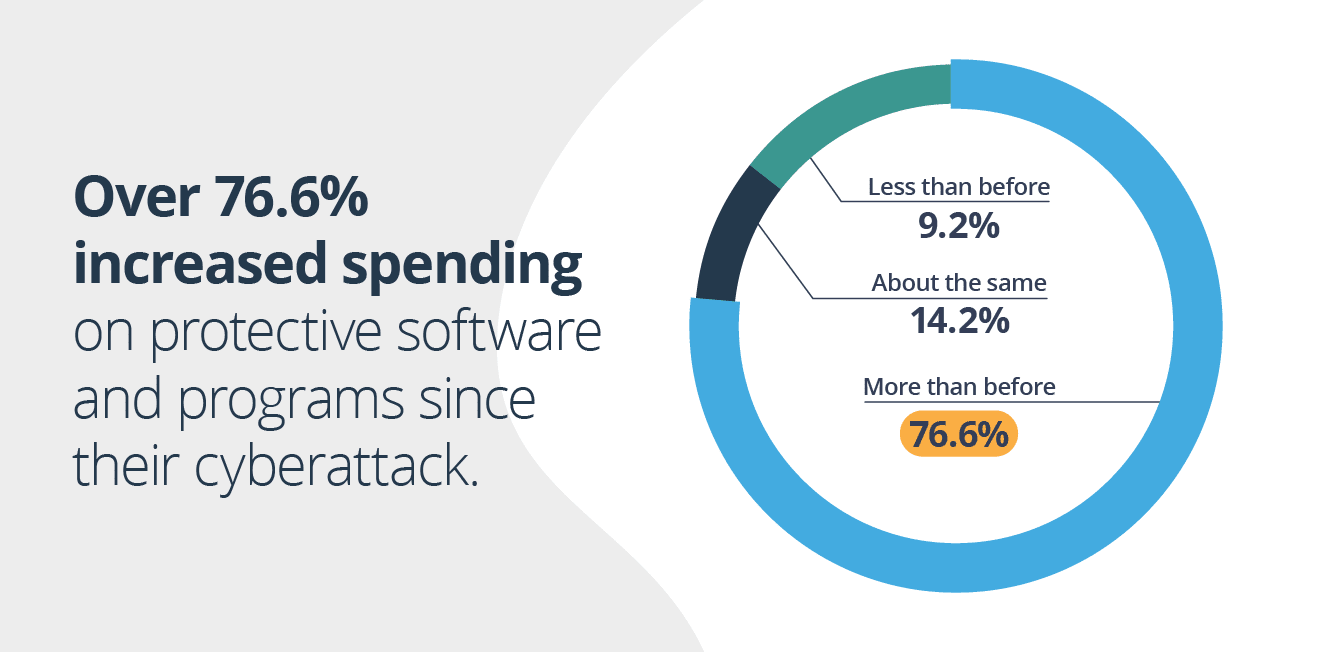
Spending on protective software and programs continues to increase as cyberattacks increase. According to Gartner, worldwide spending on information security and risk management technology and services is forecast to grow 12.4% in 2021, reaching $150.4 billion. In another study by Oracle, 78% of organizations are using a combination of more than 50 different cybersecurity tools to secure their website or protect their network.
When asked how much money our survey participants invested in protective software and programs since they experienced a cyberattack:
- 76.6% claimed they were spending more than before.
- 9.2% claimed they were spending less than before.
- 14.2% claimed they were spending about the same as before.
5. Nearly all participants experienced revenue loss regardless of whether an attack was successful
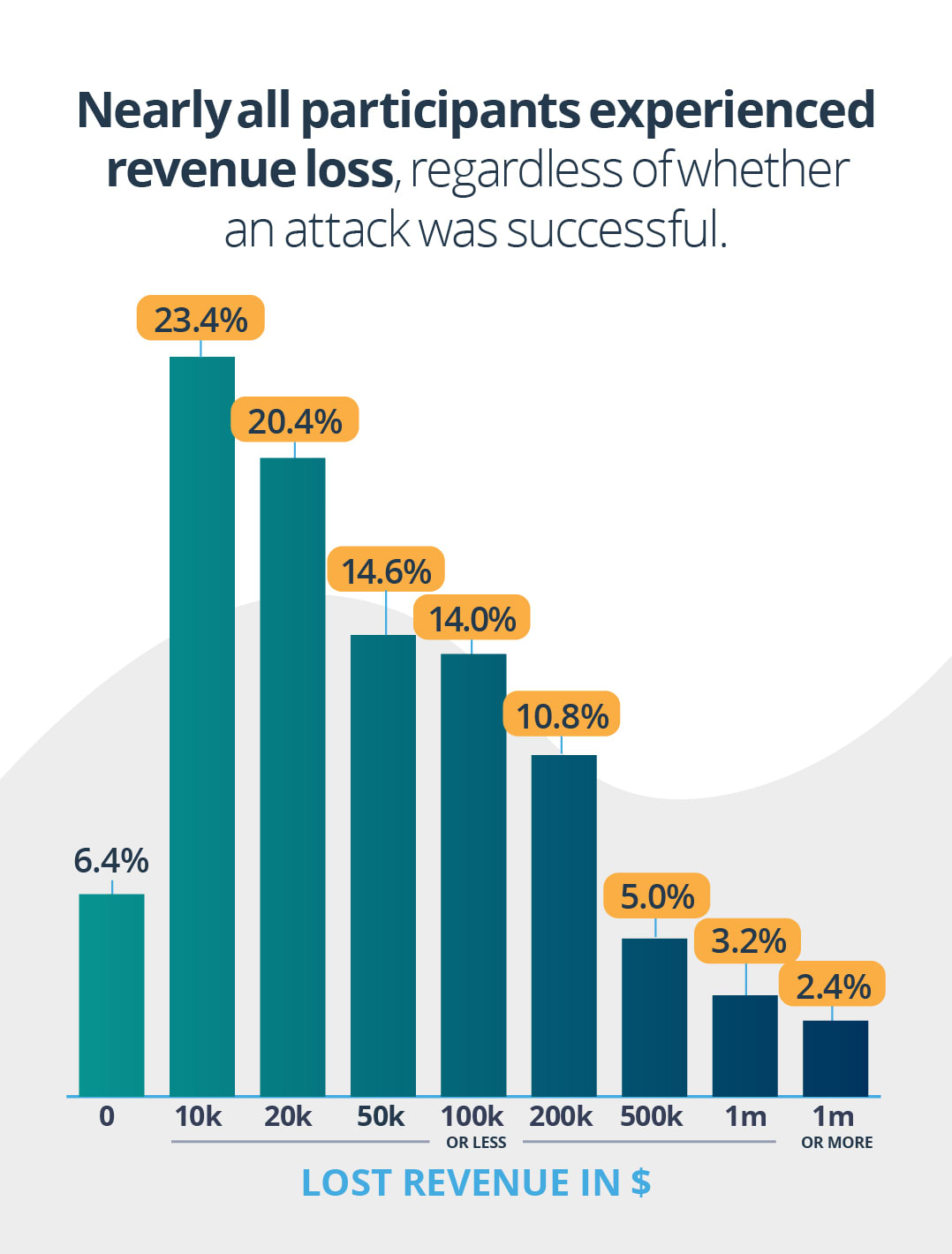
Even though a majority of participants say the cyberattack was unsuccessful (55%), nearly all of them experienced some sort of revenue loss during the process. This is because the costs associated with cyberattacks include a number of factors, such as data damage or destruction, intellectual property theft, and stolen money. Although this study did not survey for reputational damages from a cyberattack, most companies risk negative public reception, loss of trust, and a tarnished reputation post-attack.
On the low end of the spectrum, 28.6% of organizations claimed to have lost $10 thousand or less. On the high end, 2.4% of organizations claimed to have lost more than $1 million.
- $0:6.4% (32)
- $10k or less: 23.4% (117)
- $20k or less:20.2% (101)
- $50k or less:14.6% (73)
- $100k or less:14% (70)
- $200k or less $500k or less:10.8% (54)
- $500k or less $500k or less:5% (25)
- $1m or less:3.2% (16)
- More than $1m: 2.4% (12)
Another interesting statistic we discovered in our survey was that 50.08% of those in the financial services sector claimed to have lost revenue of $50,000 or more as a result of a cyberattack.
6. Cybersecurity priorities remained about the same for nearly 20% of participants after an attack
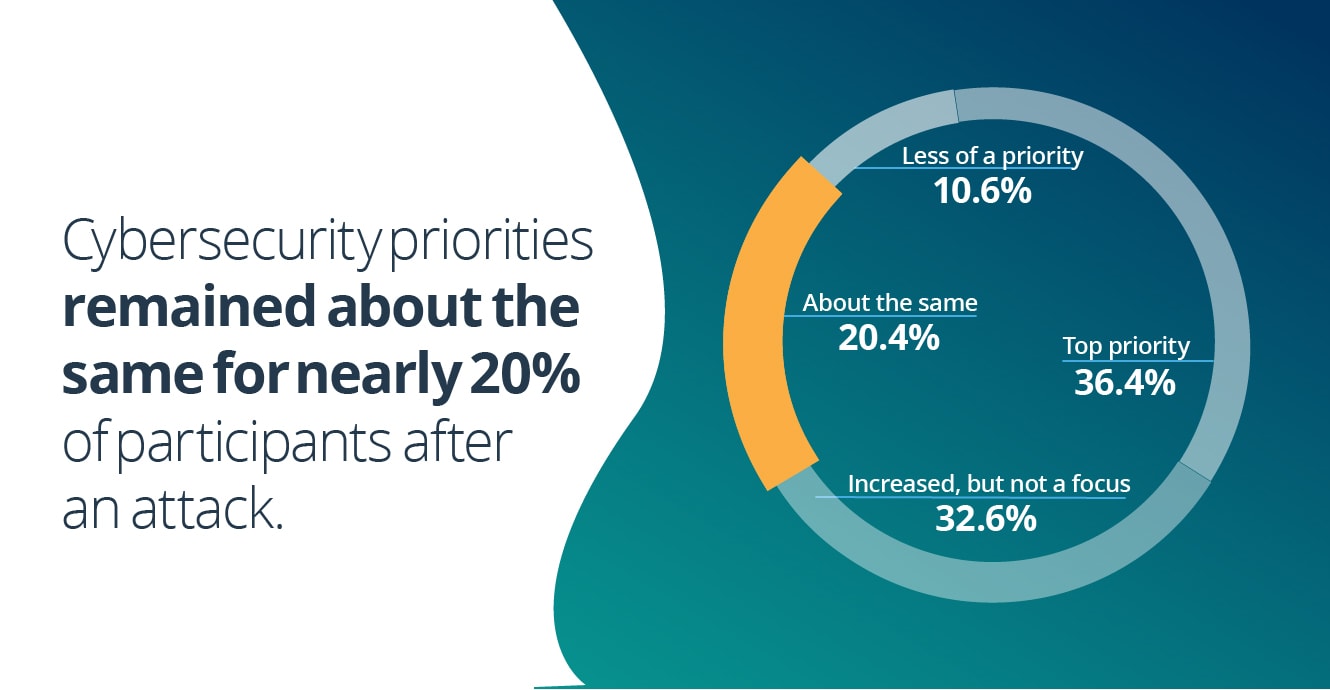
When asked to describe how cybersecurity priorities have changed for their organization after a cyberattack, 36.4% of survey participants claimed that cybersecurity is now a top priority. However, many participants claimed that cybersecurity efforts, even after a cyberattack, were not their main focus or that their cybersecurity priorities stayed about the same.
- Cybersecurity is now our top priority: 36.4% (182)
- It's increased in priority, but not our focus: 32.6% (163)
- It's about the same: 20.4% (102)
- It's become less of a priority: 10.6% (53)
7. 3 out of 4 respondents invested much more in cybersecurity education protocols and rollouts because of the attack

Just as organizations are investing more money into cybersecurity tools to protect against future cyberattacks, they are also investing more in cybersecurity education and protocol rollouts to instill cybersecurity best practices in their employees. 74% of the participants we surveyed claimed that their company invested more resources into training and governance frameworks than before they experienced a cyberattack.
- More than before: 74% (370)
- Less than before: 10% (50)
- About the same: 16% (80)
8. Middle management employees are more likely to be targeted in a cyberattack

While any employee within an organization can fall victim to a cyberattack, middle-management employees are more likely to be targeted—and it’s no surprise why. Mid-level managers often have access to confidential information and employee data, and cybercriminals typically take advantage of this through email phishing scams. When survey participants were asked which of their employees were most targeted in a cyberattack (they were given the chance to choose up to three answers), 21.96% claimed middle management, while 19.8% claimed directors and vice presidents.
- C-Suites: 16.76% (171)
- Directors and VPs: 19.8% (202)
- Middle management: 21.96% (224)
- Entry-level employees: 16.37% (167)
- Mid-to-Senior employees: 10.78% (110)
- Technical staff: 11.57% (118)
9. Software/tech companies have an abundance of confidence in their cybersecurity approaches

Software/tech companies represent the largest audience segment of our survey (29.8%), and participants in this sector claimed to have the most significant confidence levels with their cybersecurity preparedness, priority level, and ability to mitigate future cyberattacks. Additionally, these participants claimed that their organizations are doing a great job educating employees about their role in protecting the company from cyberattacks.
While having confidence in their cybersecurity infrastructure is a good thing, overconfidence can lead to complacency.
Cybercriminals and their sophisticated methods of attack are constantly evolving, which means organizations must stay vigilant to adequately protect their corporate resources. For example, Gartner suggests organizations must implement a continuous adaptive risk and trust assessment (CARTA) architecture as a base line. With the CARTA mindset, organizations must continuously assess their security risks and adapt as necessary.
10. The job market remains bright for cybersecurity professionals

According to the U.S. Bureau of Labor Statistics, employment of information security analysts—professionals who plan and carry out security measures to protect an organization’s computer networks and systems—is projected to grow 31% from 2019 to 2029, which is much faster than the average for all occupations.
According to our survey, 62.4% of participants claimed that they have increased their cybersecurity staffing in response to a cyberattack, which coincides with the technical expertise required to properly secure computer networks and systems.
- We’ve hired more staff to support against cybersecurity attacks: 62.4% (312)
- We have less staff focused on cybersecurity attacks now: 12.4% (62)
- Our team has remained around the same size: 25.2% (126)
In addition, the best industries for information security analyst opportunities likely lie in the software/tech and financial services sectors, with the healthcare sector representing no change to staffing after a cyberattack.
11. Ransomware wasn’t as prevalent as other studies suggest

Participants in the Liquid Web Cybersecurity Actions and Attitudes Study were asked to point out the specific type of attack their organization experienced. Considering how ransomware attacks are on the rise and becoming more prevalent, it was surprising to find that ransomware and other malware attacks ranked third (20.4%) compared to phishing (31.40%)
and brute-force attacks (25.4%).
While we have confidence in the results of the survey, it should be noted that the findings from this study reflect how our participants answered. It’s important to consider that studies and research from other sources indicate that ransomware and malware attacks steadily increased over the last several years.
People may conflate phishing attacks with malware since phishing scams are often just a means to gain access to systems. The end goal with this access is to perform a plethora of other malicious activities.
Our cybersecurity study shouldn’t necessarily suggest a specific prescription on what to do, but more serve as additional datapoints to help you evaluate what others have experienced. Taking into account your unique needs, vulnerabilities, and priorities, more data can be instrumental in making the right decision for a path forward.
Responding to a Cyberattack Study: Takeaways
As the landscape of cybersecurity is constantly evolving, organizations must continuously analyze their security vulnerabilities and implement measures to mitigate future cyberattacks. Based on the results of our survey, here are two primary takeaways organizations should consider:
- Make cybersecurity a priority: Nearly all participants in our survey experienced a loss in revenue from a cyberattack, regardless of dealing with a threat incident or a breach. Additionally, organizations claimed to spend large sums of money on cybersecurity software, education, and protocol rollouts after a cyberattack. Rather than waiting to make cybersecurity a priority after an attack and risking corporate data or revenue, organizations must establish a robust cybersecurity program with a CARTA mindset as quickly as possible—especially prior to migrating to the cloud or growing a remote workforce.
- Don’t become complacent: As cybercriminals become more sophisticated and new threats emerge (especially within our cloud-focused, work-from-home economy), organizations must not become complacent with their cybersecurity infrastructures. This means that companies must constantly evaluate ecosystem risks and adapt their security strategies as necessary. In order to do this, it’s important to build out internal cybersecurity teams that feature professional, cloud-savvy information security analysts, or partner with a consolidated security vendor that has your organization’s interests in mind.
Partner with a hosting provider who makes security a top priority
When you need a hosting partner with a security infrastructure you can trust, Liquid Web is here to help. Along with our fully managed cloud and dedicated server solutions, we provide around-the-clock security that works to:
- Identify and block cyber threat activity using threat intelligence and vulnerability management.
- Aggregate third-party threat intelligence and security analytics to provide actionable reports.
- Provide custom host vulnerability management with ServerSecure.
- Utilize industry leading network protection technology.
- Monitor for known and previously unknown threats.
- Protect against vulnerabilities by providing prompt system patch deployment.
Find out more about our comprehensive hosting and security solutions today.

