Disabling Recursive DNS in BIND
Recursive DNS acts as a middle-man between the viewer of a site, and the authoritative DNS servers hosting the domains and the IP addresses associated with a domain name. Recursive DNS performs two major tasks:
- When a user types a URL into their web browser, the URL is sent to the recursive DNS server first. The first thing the recursive DNS server will do is check the cache memory to see if the IP address for the URL is already stored. If the IP address information is already stored, the recursive DNS server will immediately provide the IP address back to the browser, and the viewer will be taken to the website.
- If the recursive DNS server doesn’t have the IP address in cache, it will go through the process of fetching the IP address, called walking the DNS tree, and return it to the user. The recursive DNS server then stores the IP address in memory for a certain amount of time. The amount of time that the IP address is stored is defined by the owner of the domain using a setting called TTL, Time to Live.
What is BIND?
BIND is the most widely used domain name system software on the internet. It was originally designed at the University of California, Berkeley, and the name originates from the acronym of Berkeley Internet Name Domain. The software consists of the DNS server component called named, the contracted form of name and daemon. The software suite contains various administration tools, and a DNS resolver interface library.
Why are recursive DNS requests not recommended?
Servers that support this type of request are vulnerable to fake requests from a spoofed IP address (the victim of the attack), the spoofed IP address can get overwhelmed by the number of DNS results it receives and be unable to serve regular Internet traffic. This is called an Amplifier attack because this method takes advantage of DNS servers to reflect the attack onto a target while also amplifying the volume of packets sent to the victim.
How do I disable recursive DNS requests on my server that is using BIND?
The process to disable recursive DNS requests is straightforward and only involves editing your named.conf file followed by restarting named. The following directions assume you are logged into your Linux server via SSH. For more information on SSH, see Logging into Your Server via Secure Shell (SSH).
acl "trusted" { 127.0.0.1; x.x.x.1; x.x.x.2; };- The first step is to back up your named.conf file in your /etc folder like this:
cp named.conf named.conf.backup
The above command uses the linux cp command and makes a backup copy of named.conf to a new file with the name named.conf.backup.
- The next step is to edit named.conf and add a section to ‘trust’ your server’s own IP addresses, and then to block recursion from all external sources. Now that named.conf is backed up, use an editor, such as vim, and open the file.
- With named.conf open in a text editor, we’ll add the ACL section to ‘trust’ our server’s IP address with the following sections at the top of the file:
acl "trusted"{
127.0.0.1;
x.x.x.1;
x.x.x.2;
];Replace the x.x.x lines with your server’s IP addresses. If your server only has one, you only need to update one x.x.x line and can remove the second.
- Right below you should see a section called ‘options’. Add the following line in this section to notify named what the ‘trusted’ IP addresses are that we just added:
allow-recursion { trusted; };- Lastly, skim through the remaining sections and you will probably see some sections named ‘localhost_resolver’ and/or ‘internal’. The one we are interested in is ‘external’. In this section, you should see a line like this:
recursion no;
- If you do not see it, go ahead and add it. When done, it should look like this:
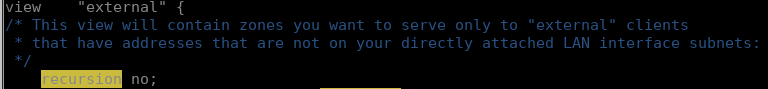
- You should be all set. Go ahead and save named.conf and then you can restart the named service with:
service named restart