◦ Comprehensive security
◦ 24/7 support
Ecommerce → Security → PCI Compliance
PCI compliance levels: a beginner’s guide

Data breaches can cripple even the most reputable organizations. That’s why businesses of all sizes that handle card payments are expected to comply with a set of standards known as PCI-DSS (Payment Card Industry Data Security Standard).
But what happens if you’re not compliant with PCI DSS? The risks are steep, leading to costly fines, legal consequences, and the devastating loss of customer confidence. A single breach could expose sensitive data, resulting in reputational damage and a long road to recovery. Not to mention the disruption to daily operations and potential revenue loss.
Let’s break down the PCI compliance levels and show you exactly what your business needs to stay secure and compliant.
Get fast, secure ecommerce hosting for any store
Optimize your online store from the ground up with reliable ecommerce hosting that’s designed to keep up with modern shoppers.
What PCI compliance levels are and why they matter
PCI compliance levels are classifications that group merchants and service providers by their annual card transaction volume, determining how much security validation, auditing, and reporting they must complete each year.
Every organization that handles credit or debit card data falls into one of four PCI levels. These levels determine how deep your annual validation must go, who audits you, and which reporting requirements apply. The higher your transaction volume, the more scrutiny you face.
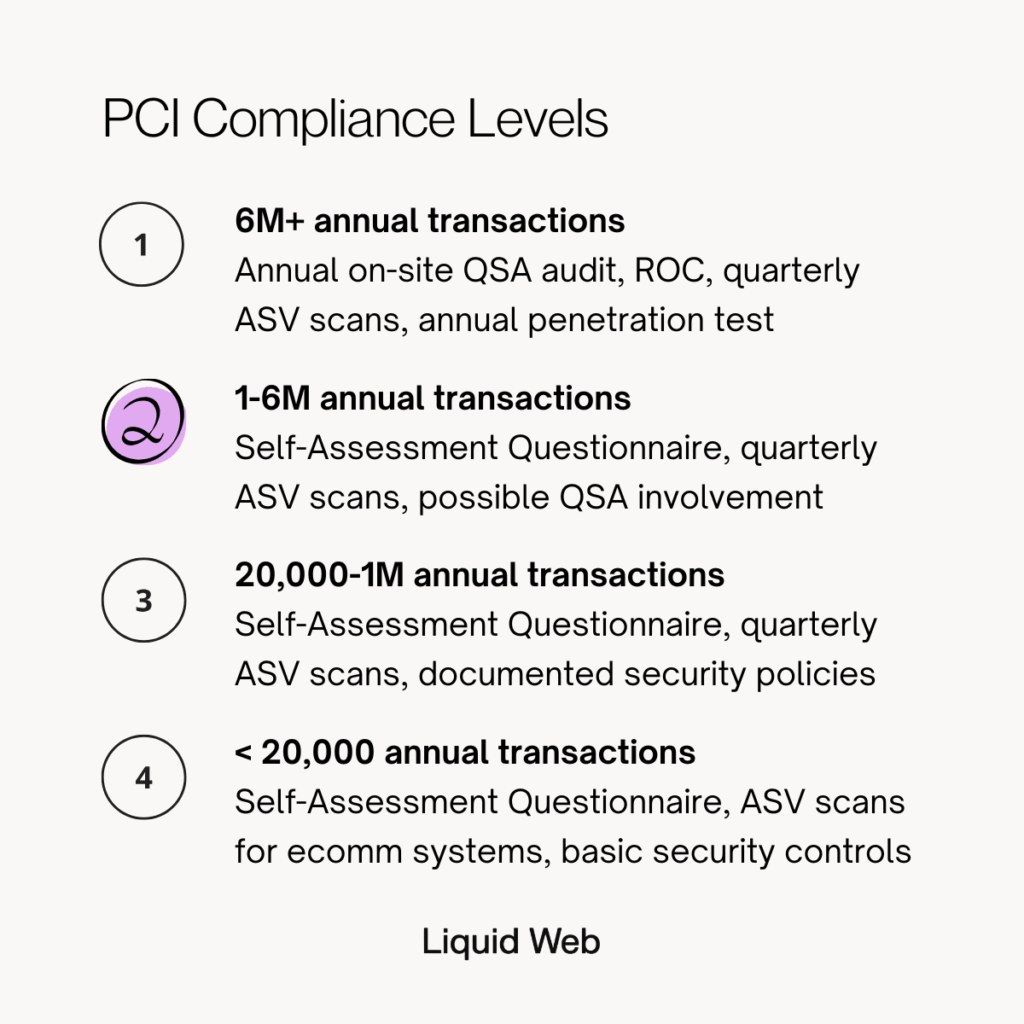
- Level 1: Handles more than 6 million annual transactions and requires the most rigorous validation, including an annual on-site QSA audit.
- Level 2: Processes between 1 million and 6 million transactions per year and typically completes a Self-Assessment Questionnaire with quarterly ASV scans.
- Level 3: Covers 20,000 to 1 million annual ecommerce transactions and relies on an SAQ plus recurring external vulnerability scans.
- Level 4: Applies to merchants with fewer than 20,000 ecommerce transactions per year and requires an SAQ and ASV scans for any online card processing systems.
For leaders in banking, fintech, and payments, knowing your PCI level sets expectations for resources, staffing, and technology investment.
PCI level 1
Level 1 applies to merchants processing over 6 million transactions per year or any organization that has experienced a major breach. At this scale, security becomes an operational discipline, not just a checklist.
Who qualifies as level 1:
- Merchants exceeding 6 million transactions annually
- Any merchant compromised in a previous data breach
- Organizations designated by a card brand as high-risk
Requirements:
- Annual on-site audit and Report on Compliance performed by a Qualified Security Assessor
- Quarterly ASV scans
- Annual penetration testing
- Comprehensive documentation of all PCI controls
- Forensic investigation requirements after any security incident
Common challenges for level 1 merchants:
- Large internal networks with inconsistent segmentation
- Legacy systems that aren’t easy to harden
- Complex vendor ecosystems
- Limited visibility across distributed infrastructure environments
PCI level 2
Level 2 fits mid-market merchants who handle high volumes but don’t hit enterprise scale. Compliance becomes less about deep audits and more about maintaining solid operational discipline.
Who qualifies as level 2:
- Merchants processing between 1 million and 6 million transactions per year
- Organizations required by their acquirer to meet Level 2 validation
Requirements:
- Self-Assessment Questionnaire
- Quarterly ASV scans
- Potential QSA involvement depending on card brand rule
- Incident response and documented security program
Typical gaps:
- Incomplete SAQs due to misunderstanding scope
- Insufficient log retention
- Poor vendor access controls
- Missed patch cycles
PCI level 3
Level 3 covers organizations with moderate ecommerce activity. These teams often run lean, so compliance lives at the intersection of security tools and operational consistency.
Who qualifies as level 3:
- Merchants processing 20,000 to 1 million ecommerce transactions per year
- Companies with growing online transaction volume
Requirements:
- Self-Assessment Questionnaire
- Quarterly ASV scans
- Network segmentation and encryption controls
- Documented access policies and monitoring
Where level 3 merchants struggle:
- Unclear boundaries between web servers and the cardholder data environment
- Limited security staffing
- Inconsistent TLS implementation
- Gaps in vendor oversight
PCI level 4
Level 4 covers the long tail of organizations that handle small volumes of card transactions. These merchants often assume PCI doesn’t apply to them, which leads to risk.
Who qualifies as level 4:
- Fewer than 20,000 ecommerce transactions per year
- Up to 1 million total annual transactions across all channels
Requirements:
- Self-Assessment Questionnaire
- ASV scans for ecommerce environments
- Basic segmentation and authentication controls
- Documented security policies
Why level 4 is still high-risk:
- Small teams often skip regular scanning
- Shared hosting creates noisy, unpredictable environments
- Weak password hygiene leads to common breaches
- Little to no monitoring or logging
How to determine your PCI level
Your acquiring bank has the final say, but you can get close by looking at a few data points.
- Check total annual card transactions for each card brand.
- Separate ecommerce from card-present transactions.
- Review any risk designations tied to industry or breach history.
- Confirm level and reporting expectations with your acquirer.
What changes from one PCI level to the next
| PCI Level | Annual Transaction Volume | Validation Requirements | Typical Merchant Profile |
|---|---|---|---|
| Level 1 | Over 6 million | Annual on-site QSA audit, ROC, quarterly ASV scans, annual penetration test | Large enterprises, major retailers, processors, or any merchant with a prior breach |
| Level 2 | 1 million to 6 million | Self-Assessment Questionnaire, quarterly ASV scans, possible QSA involvement | Mid-size retailers, established ecommerce brands, growing payment businesses |
| Level 3 | 20,000 to 1 million ecommerce transactions | Self-Assessment Questionnaire, quarterly ASV scans, documented security policies | Moderate-volume ecommerce merchants and online-first businesses |
| Level 4 | Fewer than 20,000 ecommerce transactions or up to 1 million total transactions | Self-Assessment Questionnaire, ASV scans for ecommerce systems, basic security controls | Small businesses and low-volume online or card-present merchants |
How SAQs differ by PCI level
Each Self-Assessment Questionnaire matches a specific environment and payment flow. Choosing the wrong one creates compliance gaps.
- SAQ A and A-EP apply to ecommerce models.
- SAQ B, B-IP, C, and C-VT cover in-person or device-based transactions.
- SAQ D is the “full” version used by higher levels or more complex environments.
Most Level 2–4 merchants complete some form of SAQ, but the type depends entirely on how they store, process, and transmit cardholder data.
Approved Scanning Vendor (ASV) scans and what they check
ASV scans validate your external attack surface. Scanners look for open ports, outdated software, unpatched vulnerabilities, weak TLS configurations, and known CVEs. Levels 2–4 require quarterly scans for ecommerce environments, while Level 1 requires them across all exposed systems.
PCI merchant vs PCI service provider levels
Merchants handle their own transactions. Service providers process, store, or transmit card data on behalf of others. Service providers follow similar levels, though thresholds differ and documentation expectations increase.
Many organizations fall into both categories, especially fintech firms with embedded payments.
How hosting choices influence PCI outcomes
Your infrastructure setup influences your PCI scope more than most merchants realize. Shared hosting exposes you to noisy neighbors and unpredictable configurations that expand your scope.
Dedicated servers or isolated VPS resources, however, shrink your cardholder data footprint. Managed firewalls, intrusion detection, and WAFs reduce the operational burden on your team. Centralized logging and SIEM visibility make it easier to validate continuous monitoring.
Growing ecommerce brands often use a combination of cloud and dedicated servers. See how Liquid Web’s secure ecommerce hosting solutions helped Home Depot do exactly that. →
Best practices for staying compliant at every level
- Use MFA for all administrative access
- Encrypt all data in transit and at rest
- Apply secure configurations consistently
- Segment the cardholder data environment
- Monitor logs daily and retain them for compliance timelines
- Limit vendor and third-party access
- Patch systems quickly
- Train staff regularly
- Document every control as you implement it
PCI compliance FAQs
Getting started with PCI compliance levels
PCI levels help you understand your organization’s responsibilities, resource needs, and validation workload. Knowing where you fall makes compliance smoother and more predictable.
Your next step is simple: verify your annual transaction totals and connect with your acquiring bank to confirm your PCI level. That clarity informs every technical and compliance decision that follows.
When you’re ready to upgrade your ecommerce infrastructure, Liquid Web can help. Our solutions include hardened servers, network segmentation, dedicated firewalls, WAF protection, centralized logging, and audit-ready infrastructure designed for PCI workloads. These controls shrink your compliance scope and reduce operational overhead.
Click through below or start a chat now with a financial services hosting expert to learn more.
Additional resources
What is Ecommerce? →
A complete beginner’s guide
PCI non-compliance fees →
… and how to avoid them
PCI-DDS compliance audit guide →
Costs, processes, and common mistakes

David Gibb is the Financial Controller at Liquid Web. He has over 20 years of experience working in Finance. He is a CPA in Canada, CGMA in the United Kingdom, and a CPA in Australia.