Your data is the backbone of your business, so keeping it secure is extremely important. This is where the concept of data isolation comes into play.
Data isolation is the process of separating and protecting individual transactions within a database. Preventing these transactions from interfering with one another helps maintain integrity, consistency, and security.
In this article, we’ll explore different levels of data isolation, the techniques used to achieve them, and how the cloud can further enhance data security through isolation. Let’s get started!
Key points
- Data isolation is essential for business security, protecting against internal and external threats, meeting regulatory requirements, and maintaining customer trust.
- Common methods for achieving data isolation include physical isolation, logical isolation, network isolation, virtualization, and encryption.
- The increased popularity of cloud computing has revolutionized data isolation, with cloud providers implementing logical isolation techniques to keep data secure and segregated in multi-tenant environments.
- Cloud dedicated servers offer superior data isolation by providing a private, single-tenant environment, which is critical for industries with strict regulations like healthcare and finance.
Understanding data isolation
At its core, data isolation is all about keeping individual database transactions separate and secure.
The key objective is to maintain the reliability and integrity of your data. When transactions are properly isolated, they can’t interfere with one another, even if multiple users are accessing the same information simultaneously.
That’s why ‘ACID’ (Atomicity, Consistency, Isolation, and Durability) properties are crucial. The ‘I’ in ACID stands for Isolation, and it’s this principle that safeguards your data, guaranteeing consistent and trustworthy operations, whether you’re working locally or in the cloud.
By isolating transactions, you can ensure that changes made by one transaction are not visible to other transactions until committed, preventing conflicts.
Exploring the four levels of data isolation
Databases can employ four distinct data isolation levels, each impacting transaction management and data integrity. Let’s break them down:
- Read Uncommitted: This is the lowest level, where transactions can see data that hasn’t been committed yet. While this may be acceptable in some scenarios, it also opens the door to “dirty reads,” where you could be working with incomplete or inaccurate information.
- Read Committed: This level is more commonly used. Read Committed ensures that transactions can only see data that has been committed, avoiding the pitfalls of the previous level. This offers a good balance between data security and performance.
- Repeatable Read: This level prevents “non-repeatable” or “phantom” reads, where the same query executed twice within a transaction could return different results. However, this increased isolation comes at the cost of higher resource consumption.
- Serializable: The highest level of data isolation, Serializable provides total separation between transactions by locking resources. This eliminates any possibility of interference, but it can also significantly impact database performance due to the serialization of transactions.
Concurrency control: Balancing isolation and performance
There’s often a delicate balance between maintaining data integrity through isolation and maximizing system performance.
“Concurrency control is an essential component of database management systems (DBMS). It guarantees multiple transactions can access and modify data simultaneously without compromising reliability. However, the isolation level you choose can significantly impact your system’s performance.”
Ryan MacDonald, Chief Technology Officer at Liquid Web
Higher isolation levels, like Serializable, provide the most robust protection by strictly separating transactions. But this comes at the cost of reduced transaction throughput and increased latency.
On the other hand, lower isolation levels, such as Read Uncommitted, offer better performance but leave you more vulnerable to interference.
The importance of data isolation in business security
A data breach can be devastating for your brand’s reputation and customer trust. Imagine the fallout if sensitive information fell into the wrong hands. It could lead to financial and legal consequences and damage your company’s credibility.
That’s why data isolation is a critical component of business security. By separating and protecting your data, you safeguard against internal and external threats. It’s is also essential for meeting regulatory requirements like the Health Insurance Portability and Accountability Act (HIPAA) and the General Data Protection Regulation (GDPR).
These standards demand strong data protection measures, and failing to comply can result in hefty fines and other penalties. Investing in proper data isolation practices shows your customers and governing bodies that you take data security seriously.
Securing your data: Methods for isolation
Here’s a look at some commonly used methods of achieving effective data isolation:
Physical isolation
This involves physically separating servers, databases, or hardware components that store sensitive data. Access to these isolated systems is restricted, reducing the likelihood of external threats. Examples include air-gapped networks, secure data centers, and physically secured server rooms.
Logical isolation
This method uses software-based mechanisms to segregate data within a system. It includes access controls, encryption, and partitioning to keep data compartmentalized.
Even if a breach occurs, logical isolation minimizes the impact by limiting it to the compromised segment. Examples include Role-Based Access Controls (RBAC), encryption of sensitive data, and database partitioning.
Network isolation
By creating distinct network segments or virtual local area networks (VLANs), this method isolates data traffic. It prevents unauthorized entities from intercepting sensitive information through the segregation of network communication. Network isolation can be achieved through firewalls, subnetting, and network segmentation.
Virtualization
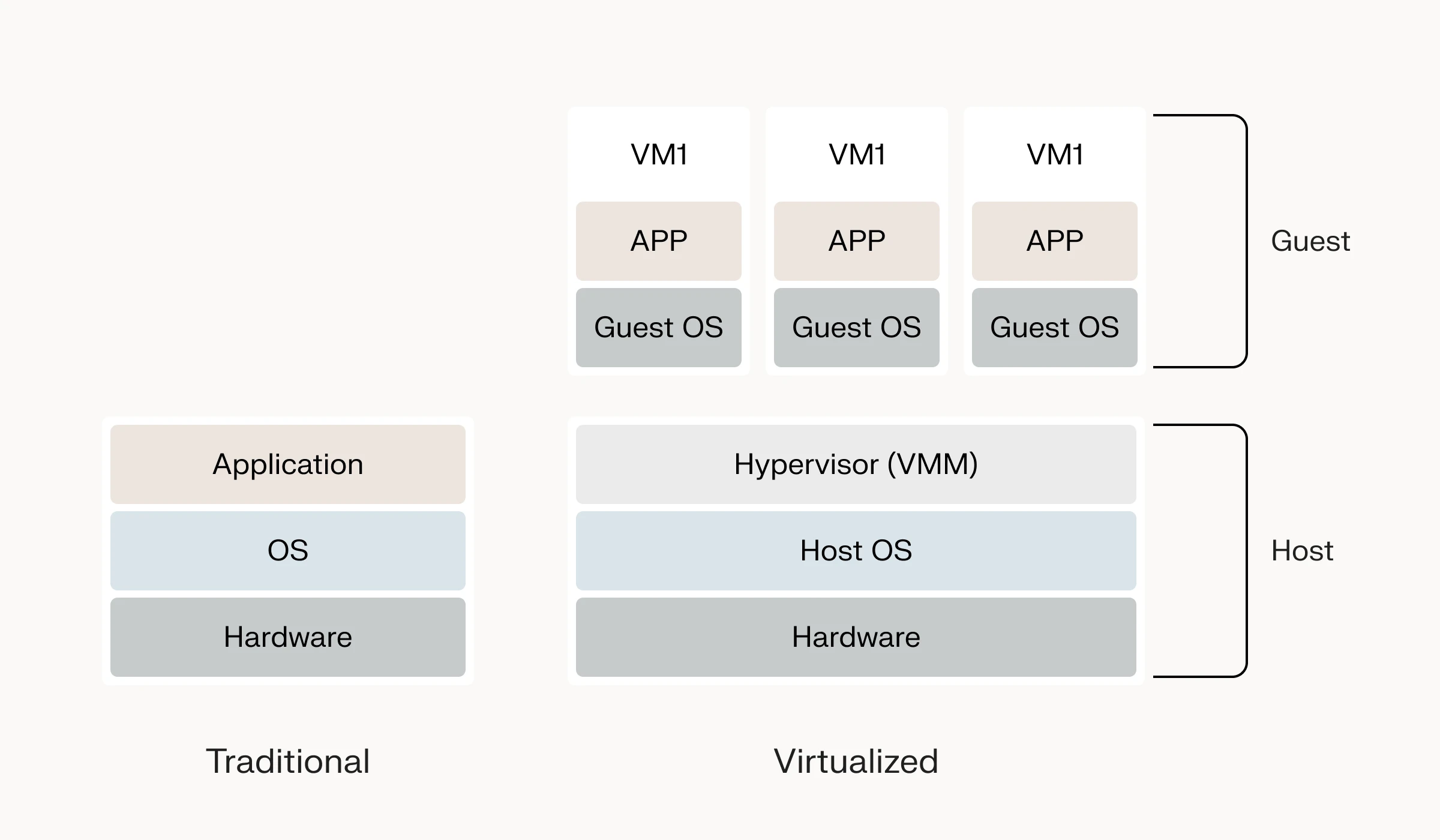
Virtualization technologies create isolated instances or containers for individual users or applications. Each virtualized environment operates independently, ensuring data separation and minimizing the risk of unauthorized access. Virtualization platforms, such as virtual machines (VMs) and containers, provide an effective means of data isolation within a shared infrastructure.
Encryption
Encryption involves encoding data and ensuring that only authorized parties with the appropriate decryption key are able to decode it. Three main types of encryption play a crucial role in data isolation:
- At rest: Protects data stored on servers, databases, or other storage media.
- In transit: Secures data as it moves between different systems or networks.
- In use: Safeguards data while it’s being processed or accessed.
Encryption technologies like Advanced Encryption Standard (AES) and Secure Sockets Layer (SSL)/Transfer Layer Security (TLS) play a crucial role in data isolation.
The fundamentals of data isolation in cloud environments
The emergence of cloud computing has transformed our approach to data isolation, offering new ways to safeguard sensitive information.
- Bringing context to data isolation: In a cloud environment, data isolation has a whole new meaning. Instead of relying solely on physical separation, cloud providers implement logical techniques to keep your data secure and segregated from other users on the same infrastructure.
- Impact on business operations: Maintaining data integrity and security is essential for businesses of all sizes. The relationship between data isolation and regulatory compliance is critical, as inadequate isolation can lead to costly data breaches and severe legal consequences.
- Technical methods of isolation in the cloud: Cloud providers employ various technical measures to facilitate data segregation, such as encryption, access controls, and physical data center security. They also implement logical isolation through multi-tenancy, so your data remains isolated from other users on the same cloud infrastructure.
Challenges of data isolation in multi-tenant systems
Multi-tenancy is a fundamental aspect of cloud services, allowing multiple customers to utilize the same underlying infrastructure. While this can be cost-effective and scalable, it also introduces some tricky challenges, such as:
- Data leakage risks: Keeping data completely separate in a shared environment can be tough. Any vulnerabilities or mistakes could lead to unauthorized access or mixing of sensitive information.
- Compliance challenges: When data overlaps between tenants, the chances of compliance violations increase, especially in highly regulated industries.
- Performance impact: If tenants compete for resources like the central processing unit (CPU), memory, or storage, it can be harder to isolate data efficiently. This can lead to performance issues and possible security risks.
Enhancing data isolation with cloud dedicated servers
If you want to take your data isolation to the next level, cloud dedicated servers may be the solution you need. These specialized resources can help address the challenges of multi-tenant environments and provide superior data protection.
The key idea behind cloud dedicated servers is that you get your own private, single-tenant environment. This means your data is completely isolated from other customers, eliminating the risks of cross-contamination or unauthorized access.
With dedicated hardware, you can ensure the integrity of your data and have complete control over your computing resources. No more worrying about performance impacts or compliance issues due to shared infrastructure.
This is especially important for industries like eCommerce, healthcare, or finance, where stringent data protection is necessary. A dedicated server can meet the most rigorous regulatory requirements and give your customers the peace of mind they deserve.
Take your data isolation strategy to the next level with cloud dedicated servers
Enhancing your data isolation strategy should be a top priority as your business continues to grow. Without proper data isolation, breaches, compliance issues, and performance problems can disrupt your business operations.
Liquid Web’s Cloud Dedicated Servers offer a great solution to these common challenges. With these dedicated resources, you get a more controlled and secure environment to keep your sensitive information safe.
The key is virtualization technology, which creates isolated spaces within the server. This effectively protects your data sets, ensuring they don’t bleed into one another. With added security measures like firewalls, distributed denial-of-service (DDoS) protection, and regular updates, you can feel confident knowing your data is safe.
Besides security, Cloud Dedicated Servers also deliver improved flexibility, performance, and scalability. Plus, you’ll have an easier time staying compliant with industry regulations. It’s a win-win all around.
As you evaluate your current data isolation approach, consider the potential improvements that Liquid Web’s Cloud Dedicated Servers can offer. By switching or upgrading to a Cloud Dedicated Server, you can strengthen your data isolation, mitigate risks, and unlock new opportunities for your business!

 Luke Cavanagh
Luke Cavanagh