WordPress is a popular target amongst hackers and often has the notion of not being secure. I want to explain how WordPress sites get hacked and what you can do about it. Even without touching code or complicated plugins, it’s quite manageable to protect your site.
The challenge for most WordPress users is that they don’t even know whether their site is getting attacked by hackers or not. Attacks often start with bots trying to find a valid username and password, simply by enumerating hundreds of thousands of username/password combinations on your wp-login.php URL. Those attacks are called brute-force attacks or dictionary attacks. WordPress doesn’t tell you about this type of event out of the box, so how are you supposed to know if attacks like that happen?
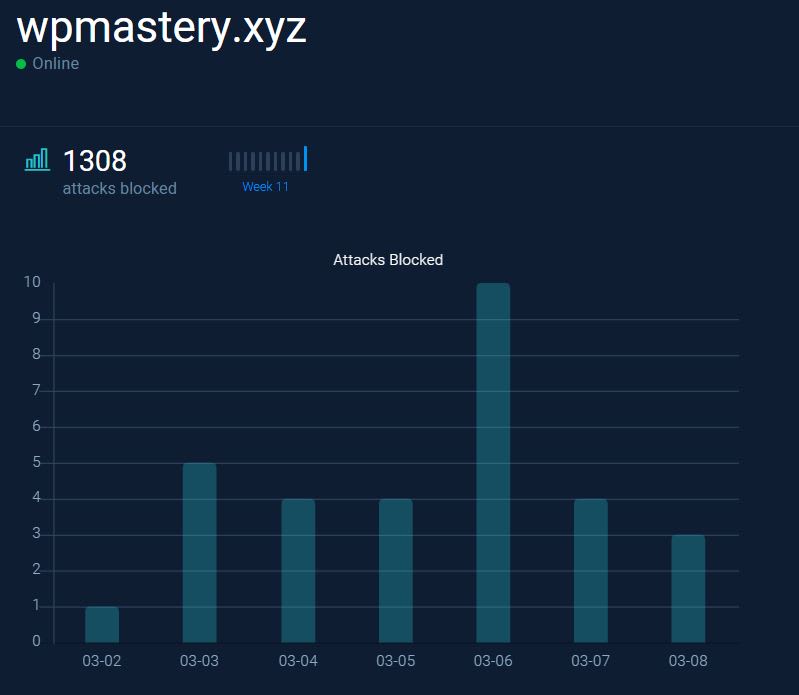
If you don’t have a firewall in place or a plugin that measures those attacks, you won’t recognize if you’re under attack unless it’s too late and a hacker gets access. In this screenshot, you can see that my WP Mastery site is under attack daily. These numbers are very low, but over time they pile up. Since October 2018, my site has been attacked 1,308 times.
I’m not trying to paint a dark picture here, but I assume that attacks trying to hack WordPress sites will increase rather than decrease. The reason is economic: the number of WordPress sites steadily increases and thus it becomes a more and more popular target for hackers. As most hacks are performed by automated software, it can be a lucrative endeavor to write a bot that can hack hundreds of thousands of sites at once.
WordPress sites are not unsafe by default, and good web hosting companies take active measures to protect their customer’s sites. Liquid Web certainly does take security seriously and has put effective protection mechanisms in place. It’s similar to how Windows PCs get hacked over time. As Windows does not get properly maintained (e.g. pending updates don’t get installed or unused software doesn’t get uninstalled), WordPress also requires a bit of work to stay secure. But if you do put in that work, you’ll be fine.
How WordPress Sites Get Hacked
Enough of background information, let’s dive into how WordPress sites get hacked and how hackers think. There are a number of entry points that hackers can exploit to gain access to your website. You’ll learn about the most important in this article, so you don’t accidentally leave a door open on your site.
First of all, you have to understand that attacks will happen no matter how big or small you consider your site to be. Hackers write automated scripts that scan the entire Internet for WordPress sites and analyze every site they find automatically. Those scripts will scan your site for the common weaknesses I listed below - and they won’t skip your site just because you only have 1,000 visitors per month. In this world, there is no puppy license for small or young sites.
Weak Passwords
Popular attacks against WordPress sites are the above-mentioned brute-force and dictionary attacks. How do WordPress sites get hacked with those? Let me break it down.
First, a hacker scans your website for usernames or email addresses of registered users. Those can easily be found on author archive pages. Hackers know that the last piece in the URL represents the username of the given user. Sometimes, hackers don’t even put in the work to scan for usernames and simply try common logins like “admin”, “administrator”, or “root”.
Knowing which usernames to try in their attacks, hackers launch the second phase. Brute-force attacks try random combinations of characters, numbers, and special characters to find a valid password. In these cases, finding a valid password is pure luck.
Dictionary attacks, on the other hand, are structured a bit differently. Hackers have text files containing millions of words from dictionaries (hence the name). Their scripts try logging in to your site by combining each word in those files with a given username.
Both attacks run millions of login tries against your site in a short amount of time. But unless your site notifies you about failed logins, you’d never know that a hacker script is trying to break into your site. Those failed logins simply would pile up in the background and you’d know your site got hacked when a hacker got access and did something bad with your site.
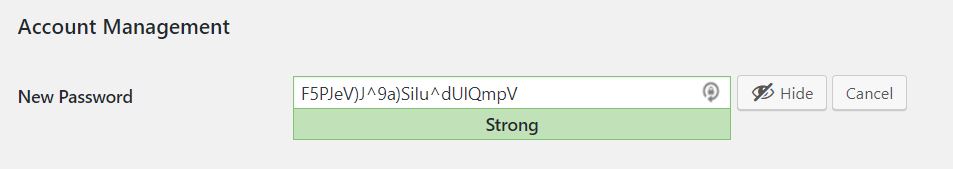
It’s a pity that sites still get hacked this way, especially since WordPress comes with a password generator that lets you create secure passwords and since it’s easy to enforce strong passwords.
Outdated WordPress Core, Themes, or Plugins
A second common weakness that hackers love to exploit is when sites run outdated versions of WordPress, themes, or plugins. You don’t have to search long before finding an example for this type of attack, just look into vulnerabilities patched in the WP Cost Estimation plugin version 9.644, a bug in WordPress version 4.9.8 that can lead to remote code execution, or a security issue with WooCommerce versions earlier than 3.5.4.
Even though those sites are somewhat technical, don’t fall into the trap of thinking that they don’t matter because you don’t understand them. Hackers actively exploit those security issues already. So, you should better create a backup of your site and update it right now if one of these examples matches your site. I’m serious, do it now and come back to the article once the update is done.
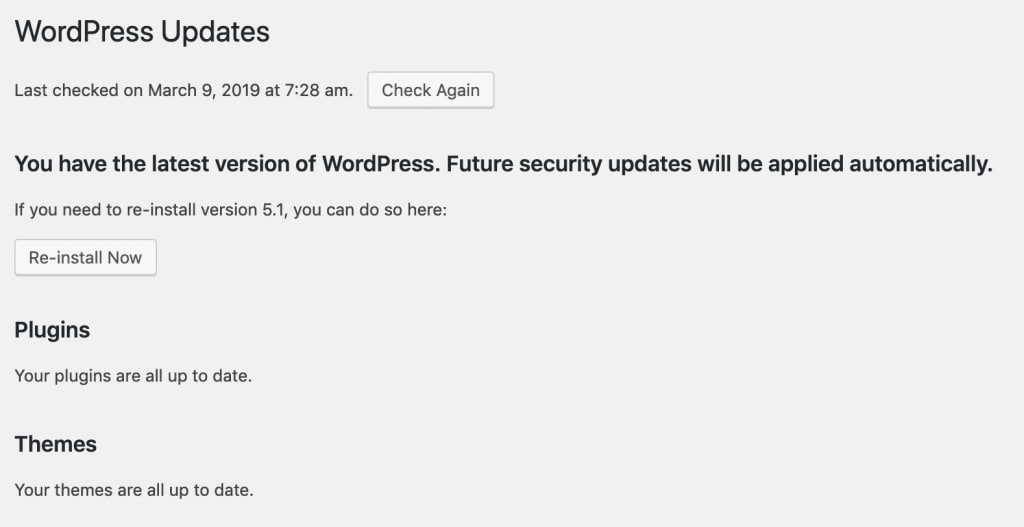
Does your “WordPress Updates” screen now look like this? Great!
Even with automatic updates, I still see many WordPress sites that are outdated. When talking to their owners, I often hear that non-techy WordPress users worry about updates breaking things. If that is the case, get your hands on Liquid Web’s Managed WordPress Hosting. Have the developers of Liquid Web test all updates and verify the updates won’t break your site. Investing in managed hosting is much cheaper than fixing a hacked site (if fixing it is even possible).
Regardless of whether you can code or not, you need your site to be updated regularly. Managed Hosting or WordPress platforms like our sister brand, Nexcess, are the best options you have if you don’t feel confident handling updates yourself.
Social Engineering
We all know social engineering from our email inboxes. Whenever we receive an email that looks like it’s from PayPal but has a few mistakes like typos or weird URLs in it, we (hopefully) recognize that and delete it. We know that PayPal would never send an email like that and understand that a hacker just tried phishing for our PayPal login. Similar emails go out for bank logins, shopping logins, etc.
Potentially, this can happen to your website too. By scanning through your site, hackers can be able to identify the email addresses of your users and then send phishing emails to them. Sometimes, hackers will pretend to be WordPress developers, security analysts, employees of your hosting company, or any other service that could need a login to your website. We have to be very cautious with emails like that. WordPress sites get hacked not only by exploiting their code but also by exploiting their users with emails like that.
While you might think this cannot happen to you because you’re the only user, you might be right. You, personally, may be aware of this security threat. But what about other users? Say, for example, you’re running a successful WooCommerce store and have hundreds or even thousands of customer logins in your database. Would they also be aware of social engineering trying to compromise their login?
If you want to understand how social engineering works, there are very interesting books on the topic - even on sites like Amazon. One is “Social Engineering: The Science of Human Hacking”, a highly interesting read not only for (aspiring) hackers or security professionals. If you want to get an insight into how hackers think, I highly recommend it!
Outdated PHP Versions
PHP is the programming language in which big parts of WordPress are written. It’s also software running on your web host, which converts the programming language into the website you see in your browser. And yes, even if you cannot code, you need to care about using an updated version of PHP.
You might have gotten a message from your hosting company a few weeks ago that you need to update your PHP version. With the latest WordPress update (5.1), you’ll even see a message about outdated PHP versions in your dashboard - that’s how important this topic is.
The problem originates from PHP version 5 being released in August 2004. Remember, that’s when the song “Yeah” by Usher was number one, Windows XP was at its pinnacle being only three years old, and the United States economy recovered from the DotCom bubble. That’s how old PHP version 5 is.
On December 31st, 2018, PHP 5.6 reached its end of life. That means if you’re still using it, you will not receive any further security patches. Vulnerabilities that are publicly known will NOT get fixed anymore. You’re literally inviting hackers to break into your site if you’re still using PHP 5.6 or even PHP 7.0 (which reached its end of life on Dec. 3rd, 2018).
Updating to PHP 7.1 or 7.2 will likely be a smooth process. It’ll bring you better loading speed and more security. Even though you might have to hire a developer to make (really old) legacy features of your site compatible, there really is no way around the PHP upgrade if you care about a stable and secure website.
How To Avoid That Your Site Gets Hacked
You’ve just learned about four ways WordPress sites can get hacked. Let’s equip you with the knowledge necessary to avoid that hack from happening on your site. Especially if you’re not a web developer, these tips can literally save your site.
Try this simple checklist to stay protected:
- Enforce strong passwords for your users. WordPress has a mechanism built-in to create strong passwords, and password managers help you manage passwords securely. I recommend at least 16 characters for any password.
- Invest in secure hosting and have your host update PHP to at least version 7.1. If in doubt about which host to choose, you can’t go wrong with Liquid Web.
- Install pending updates at least weekly. This is part of my standard WordPress maintenance checklist for 2019 as well.
- Raise awareness for social engineering attacks amongst your users by explaining how those attacks work. Feel free to copy the paragraph from this article.
- Remove plugins and themes you’re no longer using.
- Install tools like Solid Security from SolidWP to protect your site. I do not recommend WordFence as we found it caused issues on a number of client sites we manage.
- Ensure you always have a backup of your site. Liquid Web takes backups for you, but you can also install free plugins like Updraft Plus or BackWPUp.
This article is by no means an exhaustive list of how WordPress sites get hacked but is intended to give you an overview of the common WordPress security risks. Similarly, the checklist just covers the basics too, there are many more things you can do to harden your WordPress site.

Jan Koch
Jan is a WordPress developer and runs an agency that specializes in building and improving WordPress websites. He writes at WP Mastery and is working with businesses and entrepreneurs across the globe.
Keep up to date with the latest Hosting news.



