Modern businesses are increasingly adopting cloud computing for its scalability, flexibility, and technological advancements.
A 2023 report by tech media firm Foundry report revealed that two-thirds of IT decision-makers default to cloud-based services when acquiring or upgrading new technical capabilities.
This growing dependence on cloud technologies necessitates the adoption of strong security practices to protect sensitive data and ensure compliance with regulations. Foregoing proper security measures leaves businesses vulnerable to costly breaches and devastating cyberattacks.
This may be why 46% of those surveyed by Foundry also mentioned that cloud-based security is their second-highest priority when adopting cloud capabilities.
This article will examine the process of creating and implementing effective cloud security policies for organizations. From key considerations for policy development to best practices for implementation and strategies for ongoing maintenance and enforcement, you’ll learn everything that goes into strengthening your cloud security posture.
Key points
- A comprehensive cloud security policy is essential for data protection and compliance.
- Key components of a cloud security policy include purpose, risk assessment, access controls, and incident response.
- Best practices include shared responsibility, least privilege, automation, and detection tools.
- Regular employee training fosters a culture of security awareness.
- Partnering with a reputable managed service provider like Liquid Web enhances cloud security.
What is a cloud security policy?
A cloud security policy is a detailed set of guidelines, procedures, and best practices designed to safeguard an organization’s data, applications, and infrastructure when leveraging cloud computing services. It outlines the necessary measures to safeguard sensitive information, block unauthorized access, and maintain compliance with relevant regulations and industry standards.
The core components of a robust cloud security policy include:
- Access control: Defining user roles, permissions, and authentication methods to prevent unauthorized access to cloud resources.
- Data protection: Encrypting sensitive data, implementing backup and recovery procedures, and establishing data retention policies.
- Incident response: Creating a strategy to identify, investigate, and address security incidents in the cloud environment.
- Compliance: Ensuring adherence to relevant regulations, such as HIPAA, GDPR, or PCI DSS, depending on the organization’s industry and jurisdiction.
⚠️ A one-size-fits-all cloud security policy is ineffective. Each organization must tailor its policy to align with its unique needs, risk tolerance, and compliance requirements, taking into account factors like the type of data stored in the cloud, the cloud service models (IaaS, PaaS, or SaaS), and the specific threats and vulnerabilities it faces.
Why do you need a cloud security policy?
Without proper security measures in place, your business faces significant risks, including:
- Data breaches: Unauthorized access to sensitive information can lead to financial losses, reputational damage, and legal consequences.
- Cyberattacks: Malicious actors can exploit vulnerabilities in cloud infrastructure to disrupt operations, steal data, or deploy malware.
- Compliance violations: Failing to adhere to industry-specific regulations, such as HIPAA for healthcare or GDPR for data privacy, can result in substantial fines and legal action.
Conversely, a well-defined cloud security policy helps your business:
- Mitigate risks by establishing clear guidelines for secure cloud usage, access control, and incident response.
- Build trust with customers and stakeholders by demonstrating a strong commitment to data protection, ultimately enhancing your brand reputation.
- Improve operational efficiency by streamlining security processes and providing better visibility into cloud resources.
- Increase transparency, allowing for more effective governance and risk management.
Essential elements of an effective cloud security policy
Building a rock-solid cloud security policy involves weaving together the following components:
Purpose
Define a clear purpose for your cloud security policy that outlines the goals and objectives for secure and efficient use of cloud services within your organization. This purpose is the foundation for all cloud-related activities, guiding employees, contractors, and third-party vendors in ensuring your data and systems’ availability, integrity, and confidentiality.
Risk assessment
The next step in creating a strong cloud security policy is determining what could go wrong. This means assessing risks by looking for any weak spots that bad actors might try to exploit.
Here’s what you should do:
- List everything that could threaten your cloud services, like hackers and viruses.
- Use special tools to check for holes in your cloud setup that these threats could break through.
- Consider how each risk could affect your business, data, and reputation if it happens.
- Figure out how likely each risk is to happen based on your existing protections and what has happened before.
- Give each risk a grade (like low, medium, or high) by looking at how bad it would be and how likely it is.
- Put the risks in order, starting with the ones most likely to happen and which would cause the most trouble.
- Come up with plans to make the risks less likely or less harmful, like using better encryption or being pickier about who can access what.
Data protection
Aside from the security benefits, data protection is an important part of maintaining customer trust and legal compliance. Here’s what goes into safeguarding your data from when it’s created to when it’s deleted:
- Classification: Put your data into clear groups based on how sensitive and important it is. Explain how your policies should handle and protect each group.
- Minimization: Only collect, store, and share the data you really need. Regularly check and safely delete any data you no longer need.
- Retention and disposal: Establish rules for how long you need to keep different types of data to comply with the law and keep your business running smoothly.
- Backup and recovery: Back up your data often, test those backups, and store copies in different places.
- Portability: Plan how to safely move or export your data, especially if you switch to a different cloud provider.
🔐 Make sure to encrypt all data both at rest and in transit for even more coverage with endpoint protection systems such as SSL and VPNs.
Access control
You have to implement access control to manage who can access which resources, what actions they can perform with that access, and how to verify their identity.
Using Multi-Factor Authentication (MFA), like a password plus biometrics, makes it harder for unauthorized users to get in. The principle of least privilege, i.e., only giving people as much access as they need, helps prevent accidental or intentional data leaks.
Tools like Cloud Access Security Brokers (CASBs) and Identity and Access Management (IAM) systems let you monitor and control who can access what, ensuring your cloud environment stays secure.
Threat detection and response
When it comes to safeguarding your cloud, you can’t afford to be passive. 24/7 vigilance is key. That’s where threat detection and response come in.
You need tools to identify and warn you about emerging threats and a plan for dealing with them. That’s your incident response plan, your playbook for what to do when things hit the fan.
Your incident response plan should encompass the following:
- Threat detection methods.
- Containment strategies to prevent the problem from escalating.
- Investigation procedures to determine the root cause.
- Remediation steps to resolve the issue.
- Post-incident review to improve preparedness for future incidents.
Leverage security tools like Security Information and Event Management (SIEM) systems, Intrusion Detection and Prevention Systems (IDPS), and Cloud Workload Protection Platforms (CWPP) to strengthen your efforts in this area.
Establish clear roles and communication channels for every team member beforehand. In the event of a threat, confusion and lack of coordination can make a bad situation worse.
Additionally, run regular security audits to identify and address vulnerabilities before attackers can exploit them.
Compliance and privacy
Ensure your cloud security policy complies with all pertinent legal and regulatory requirements, such as HIPAA for healthcare, PCI DSS for credit card data, or GDPR for personal data from the EU.
Implement data sovereignty by storing and processing data in compliance with relevant laws. Strong controls, such as encryption and access controls, make protecting your data easier.
Include clear procedures for handling personal and sensitive data throughout its lifecycle. Regular reviews and updates are necessary for continuous compliance as laws and regulations evolve, helping you maintain trust with customers and stakeholders.
Cloud security architecture
If attackers do manage to penetrate your defenses, segmentation and isolation techniques, such as Virtual Private Clouds (VPCs) and separate accounts, can limit the damage they can inflict on your cloud environment.
Secure APIs also ensure that different parts of your cloud can communicate safely using strong authentication, authorization, and encryption. A well-designed architecture reduces your attack surface and enables quicker detection and response to threats.
Review and enhance your architecture regularly to align with your business’s changing needs. Collaborate closely with your security team and cloud provider to consistently prioritize and strengthen security measures in every phase of development.
Vendor management
If you’re working with external cloud service providers, investigate their security features and track records. Establish clear policies for vendor risk management, including regular security assessments and strict access controls.
Consider a provider like Liquid Web, which offers secure hosting solutions with built-in protection against DDoS attacks, malware, and other threats. A team of security experts continuously monitors and updates the systems to stay ahead of emerging risks.
To build a strong relationship with your service provider, implement a vendor management program with due diligence, contractual safeguards, and ongoing oversight.
Responsibilities and ownership
The Responsible, Accountable, Consulted, Informed (RACI) matrix helps assign roles and decision-making authority for key tasks, such as adding applications, modifying infrastructure, or migrating data.
The RACI chart should also specify who’s responsible for auditing the cloud security policy, detailing what information is logged and who has access to these logs. This ensures that the right people are involved in making decisions, implementing changes, and monitoring the security policy’s effectiveness.
By documenting these responsibilities and ownership structures, you can improve accountability, reduce confusion, and ensure critical security tasks are performed consistently and effectively. This will ultimately strengthen the overall security posture of your cloud environment and protect sensitive data from unauthorized access.
Employee training and awareness
Just because your policy receives approval from higher-ups doesn’t mean your work is finished. Equipping employees with knowledge of your cloud security practices is the final step in building an effective security policy. After all, you’re only as strong as your weakest link.
🔎 Did you know that human error is cited as the leading cause in an astounding 55% of breaches? This puts it well ahead of hackers, who account for only 21%.
With this in mind, it’s important to:
- Have regular training sessions to teach your employees the best ways to keep your cloud secure.
- Update your training materials often to cover the latest security threats and policy changes.
Best practices for implementing cloud security policies
Strengthen your cloud security posture and protect your valuable assets by keeping these essential best practices in mind:
Shared responsibility
To ensure solid cloud security, you need to adopt a model of shared responsibility, a framework that distributes security responsibilities between the cloud service provider and the customer.
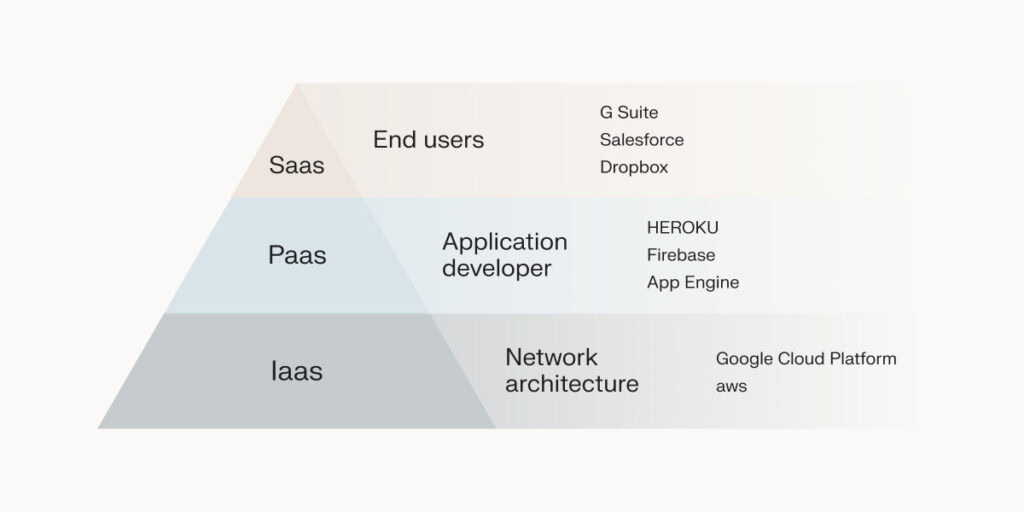
The specifics of this model vary depending on the type of cloud service:
- Infrastructure-as-a-Service (IaaS): The provider secures the physical infrastructure while the customer secures the operating systems, middleware, and applications running on virtual machines.
- Platform-as-a-Service (PaaS): The provider secures the infrastructure and the platform while the customer secures their applications and data.
- Software-as-a-Service (SaaS): The provider takes on most security responsibilities while the customer manages user access and protects their data.
Least privilege access
The principle of least privilege access states that users should only be given the minimum level of access needed to perform their required tasks. Use IAM solutions to define granular permissions for each user based on their role and responsibilities, minimizing the risk of data breaches and unauthorized access.
Combine this with just-in-time access, which grants users temporary access to certain resources for a limited time before automatically revoking it. Regularly review and update user permissions, especially when roles change or employees leave the company.
Automating IAM policies can help ensure consistent enforcement of least-privilege access across your cloud environment.
Automation
You also need automation to consistently apply security policies, reduce human error, and provide a scalable solution for cloud management. Implement automation to ensure that security configurations are applied uniformly across your cloud environment, minimizing the risk of misconfigurations.
Use Infrastructure as Code (IaC) tools to automatically deploy and configure cloud resources securely. Leverage Security Orchestration, Automation, and Response (SOAR) platforms to automate incident response and remediation processes.
Optimize your cloud environment for compliance by automating checks and audits to adhere to regulatory standards continuously.
Automation isn’t a silver bullet, but combining it with human expertise and oversight will significantly enhance your cloud security strategy’s consistency, efficiency, and scalability.
Detection tools
Cloud Security Posture Management (CSPM) and Cloud Workload Protection Platforms (CWPPs) let you detect misconfigurations and non-compliance in real time.
CSPM tools continuously monitor your cloud infrastructure and configurations, comparing them against predefined security best practices and compliance standards and alerting you to deviations.
CWPP tools focus on protecting cloud workloads, such as virtual machines, containers, and serverless functions, offering features like vulnerability scanning, network segmentation, and runtime protection. They can detect and respond to threats in real time, automatically quarantining compromised resources to prevent threats from spreading.
When selecting CSPM and CWPP tools, ensure they integrate well with your existing cloud environment and provide real-time alerts and remediation guidance to strengthen your cloud security posture.
Recommended resources
Consult resources from trusted cybersecurity organizations for the most current and detailed information on cloud security best practices.
For instance, the Cloud Security Alliance (CSA) offers whitepapers, research reports, and training programs focused on secure cloud computing. Aside from this, the National Institute of Standards and Technology (NIST) provides cybersecurity standards, guidelines, and best practices, including the NIST Cybersecurity Framework (CSF) and the NIST Cloud Computing Standards Roadmap.
Similarly, cybersecurity journals and publications also keep you informed about the latest cloud security trends and threats.
Managed services
Leveraging fully managed cloud services can help enforce your security policies by offloading day-to-day security tasks to a trusted provider. When selecting a managed service provider, choose one with a strong security and compliance track record, relevant certifications like SOC 3, and industry experience.
Liquid Web is one such provider, with fully managed hosting services that offer everything you need for secure and reliable cloud computing. Experienced professionals handle everything from patch management to threat intelligence in accordance with your standards.
Their services also include backups and disaster recovery, as well as 24/7 proactive monitoring, ensuring data availability and integrity.
By partnering with a reputable managed service provider, you can enhance policy enforcement, reduce operational overhead, and access advanced security capabilities while focusing on your core business.
Refine your cloud security approach
A well-crafted cloud security policy should include access control, data protection, incident response, and compliance. It should also be tailored to your organization’s unique needs, risk tolerance, and industry-specific regulations.
Implementing best practices like zero-trust, shared responsibility, least privilege access, automation, and detection tools can significantly enhance your cloud security posture. Equally important is regularly reviewing and updating your policies, investing in employee training, and fostering a culture of security awareness.
Partnering with a reputable managed service provider like Liquid Web can be a game-changer. With advanced security features, a team of experts, and fully managed hosting services, Liquid Web empowers you to focus on your core operations while they handle the complexities of cloud security.
Prioritize cloud security and adopt a proactive approach to harness the full potential of cloud computing, safeguard your data, maintain customer trust, and drive your business forward with confidence. Don’t wait – start strengthening your cloud security with Liquid Web today!

 Luke Cavanagh
Luke Cavanagh