The threat of a security breach is omnipresent, and it’s no different for bare metal infrastructure.
According to a survey among chief information security officers, three out of four businesses in the U.S. were at risk of a cyberattack in 2023. This is not surprising, as malicious software programs have skyrocketed in recent years.
The AV-Test Institute, an independent IT security firm, detects more than 450,000 new malware daily. What’s more, recent research conducted at the University of Sheffield reveals that cybercriminals use the latest technology, like artificial intelligence and machine learning, to create malware from plain-language instructions.
This high volume of sophisticated malware poses many threats to organizations, including data leaks, noncompliance with privacy rules, and loss of revenue and goodwill. To ensure maximum data security and regulatory compliance, you must proactively detect and mitigate malware in your computer systems.
This guide dives into bare metal malware analysis and reveals why it’s the best method for evasive malware detection.
Here’s what you’ll learn:
- What is malware analysis?
- Malware analysis methods
- What is bare metal malware analysis?
- How does bare metal analysis detect malware?
- Bare metal analysis vs other malware analysis methods
- Disadvantages of bare metal analysis
- Final thoughts: Bare metal malware analysis
Key points
- Organizations use malware detection techniques like static and dynamic analysis to mitigate malicious attacks.
- Sandboxing is a cybersecurity technique that allows you to run malicious files in an isolated virtual environment.
- Stealthy malware uses evasion techniques to beat the sandbox method.
- In bare metal analysis, you detonate malware in a real machine, increasing its chances of exhibiting its true behavior.
- Since virtual machine-based malware detection has limitations, bare metal systems offer a more efficient solution.
What is malware analysis?
Malware analysis is the practice of examining the design and run-time behavior of malicious software to understand how it attacks a system or network.
It reveals how malware works, helping security teams develop defensive mechanisms to mitigate attacks.
Malware analysis has two primary goals. First, it aims to understand the category and source code of the malicious software. Second, it tries to estimate the damage malware can cause to the computers on an enterprise network.
Based on these goals, there are two primary types of malware analysis:
- Static malware analysis — This involves studying malware behavior without running it on a machine. To do this, an expert examines the malware’s signature and source code. Static analysis doesn’t need an execution environment; hence, it’s a quick and cheap malware detection method.
- Dynamic malware analysis —This method executes the malware program in a controlled environment to study how it behaves in real time. It is more in-depth than static analysis, but it needs a test environment and is potentially time-consuming.
Malware analysis methods
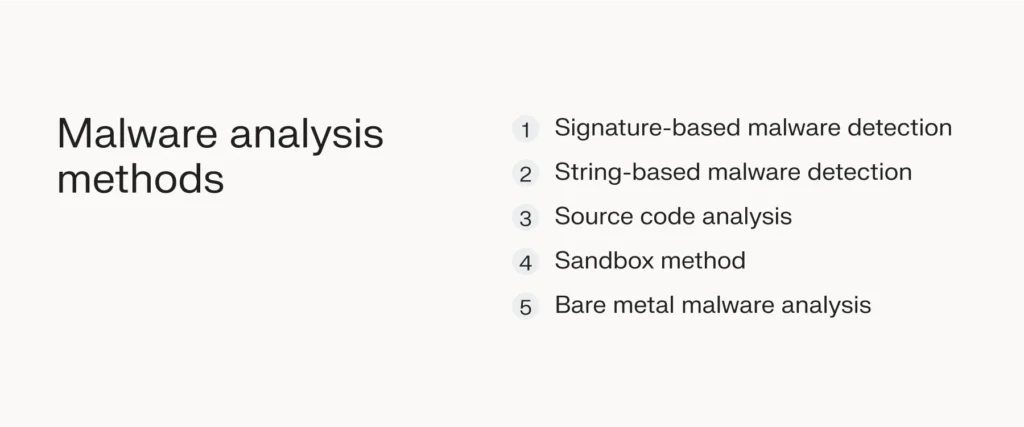
Most cybersecurity teams use a hybrid analysis technique, which means they combine static and dynamic methods to detect malicious behavior effectively.
Let’s explore the most common malware analysis methods using these techniques.
Signature-based/string-based malware detection
In the signature-based method, an analysis tool, like an antivirus, looks for a unique series of bytes or patterns in suspicious software. In string-based malware detection, the antivirus tries to detect strings, like a specific command, URL, or file path in a malicious program.
If the software under inspection has a similar string or pattern to known malware, the antivirus will flag it.
Limitations: While these techniques are highly effective in detecting malicious attacks similar to known malware, they can’t detect new malicious programs with unique signatures.
Source code analysis
The source code analysis is a quick and cost-effective cybersecurity practice that involves studying the malware’s source code to understand its design.
To achieve this, a cybersecurity expert recreates the source code from a malware’s executable file, typically using software tools like a disassembler or debugger.
Limitations: Malware creators often obfuscate the source code through convoluted coding, encryption, packing, and restructuring. So, it’s a challenge to re-engineer the source code from the binary.
Sandbox method
Cybersecurity experts often execute malware in an isolated and controlled test environment. This is known as dynamic malware analysis, and it helps IT teams understand how malware behaves in a real target machine.
The sandbox method is an example of dynamic analysis, where the malware code is executed on a virtual machine. During malware detonation, the computer security team observes the system and network activity to identify:
- The files malware modifies or erases.
- The registry entries malware rewrites.
- The servers malware connects.
This information helps cybersecurity experts understand the malware’s mode of attack.
You can quickly create a virtualized environment using virtualization software like VMware and system emulators like Quick Emulator (QEMU). The virtual machines allow snapshots, so if the machine’s operating system or data files are compromised after a malware attack, they can be restored to an earlier state.
Limitations: Cybercriminals are aware of sandbox testing, so they design new malware in such a way that it can detect a sandbox and mask its behavior.
We can address this issue by running malware on real hardware, which is what bare metal analysis does.
What is bare metal malware analysis?
Bare metal malware analysis involves examining suspicious software by executing it on a bare metal server — a physical server dedicated to one tenant.
The security team observes the bare metal server to understand the malware’s mode of operation, its adverse effects, and how it spreads.
Bare metal malware analysis is the most effective detection technique since malware can’t differentiate a controlled bare metal environment from a real target machine. So, unlike in the sandbox method, malware won’t be able to mask its malicious behavior on a bare metal server.
How does bare metal analysis detect malware?
In bare metal analysis, suspicious software is allowed to run on an isolated bare metal server. With the help of a malware monitoring component installed on the bare metal, the security team observes the attack’s effects on the server.
Here’s how bare metal analysis detects malware.
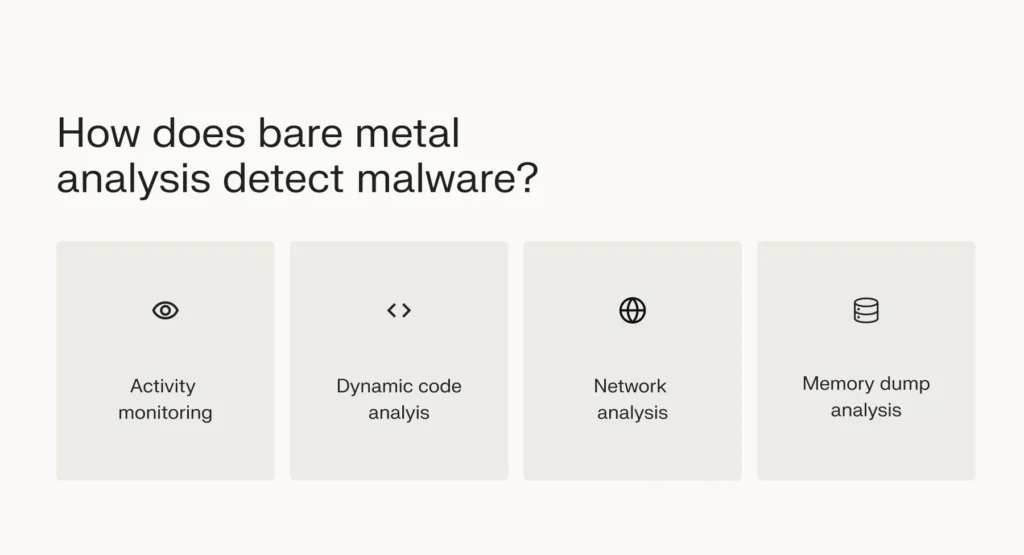
Activity monitoring
The cybersecurity team monitors malicious activities within the test environment. Malware might make system calls to create or delete files, change registry entries, and open new network connections.
Activity monitoring helps the cybersecurity team understand the malware’s mode of operation and the parts of the machine it targets.
Network analysis
During an attack, malware might copy files from the target machine and send them to a remote server.
The security team monitors the network connections and data exchange between malware and external servers, which helps them identify the malware’s source and the data it’s trying to steal.
Dynamic code analysis
Dynamic code analysis uses a debugger to run the malware code step by step. Security experts monitor the execution of each line of code, helping them understand the malware’s behavior, design, and potential impact.
Memory dump analysis
During malware execution, security experts take snapshots of the system’s memory using tools like WinPMem for Microsoft Windows and Avml for Linux. They dump memory into files, analyzing how malware injects itself into the server and how it behaves.
Cybersecurity teams use bare metal malware analysis results to identify the symptoms of a malware attack on real machines, quarantine and debug affected files, and deploy server security measures to prevent further damage.
Bare metal analysis vs other malware analysis methods
Bare metal analysis has many benefits compared to signature/string-based malware analysis and the sandbox method. Let’s explore the differences between these methods.
Bare metal analysis vs signature/string-based analysis
Signature-based malware analysis relies on unique patterns or arrays of bytes within the malware code. These patterns are then compared with the patterns of known malware.
However, malware designers have upgraded their approach — they ensure the new malware has a different signature and doesn’t contain any strings similar to existing malware.
With bare metal analysis, cybersecurity teams are not limited by the malware’s signature. Instead, they observe how it behaves in a real machine. This makes the detection rate higher in bare metal analysis.
Bare metal analysis vs sandbox method
While the sandbox method uses an isolated environment, advanced malware can detect this environment and mask their actual behavior on the sandbox, thereby evading detection.
Malware may use the attributes of a host system to determine if it’s running on a real machine or a test environment. These include storage space, CPU speed, internet connectivity, and the operating system’s source code.
A bare metal server is identical to a real target machine, so it’s impossible for malware to detect if it’s running in a test environment or on a target machine.
As a result, it won’t be able to mask its actual behavior.
Drawbacks of bare metal analysis
While bare metal analysis is the best malware analysis method in terms of its success rate, it has certain drawbacks.
Expensive
A bare metal server is often more expensive than a virtual machine. Malware under test could potentially damage the bare metal server, rendering it unusable. So, if you have a high volume of malware to analyze, using a new bare metal server every time could be costly.
Time-consuming
After every cycle of malware analysis, the bare metal server needs to be restored to a previous stable state. Most system restore solutions use the disk restore method and need a system reboot.
This may cause considerable downtime for the server, thus consuming a lot of time if there are a lot of malware samples to inspect.
An efficient malware analysis technique leverages static and dynamic methods to increase the possibility of detection.
Final thoughts: Bare metal malware analysis
Modern malware is clever enough to evade analysis and detection tools. Hence, looking for a known signature or running it on a virtual machine might not be sufficient to detect malware.
Unlike other malware detection methods, bare metal analysis creates a controlled environment that’s an exact copy of the target system, leading to a higher detection rate.
However, this method is potentially time-consuming, especially if you have large volumes of malware samples but only a few machines to analyze them.
Bare metal cloud, which combines bare metal efficiency with cloud scalability, can help you speed up your analysis.
If you’re ready to mitigate malware attacks using highly secure and scalable bare metal servers, check out Liquid Web’s cloud metal or bare metal hosting plans today, or contact us to discuss which plan would be the right fit for your needs.

 Maddy Osman
Maddy Osman