Overview
Joomla’s latest update addresses a critical remote command-execution vulnerability that has been actively exploited in the wild since at least Dec. 12, 2015.
Impact
The vulnerability affects every version of Joomla from 1.5 to 3.4.5, and Sucuri reported that nearly every site they checked had been targeted when Joomla 3.4.6 was released to address the issue.
Summary
- CVE-2015-8562 was made public Dec. 12, 2015.
- The vulnerability allows an attacker to remotely execute commands by exploiting Joomla’s method of writing session data to its database.
- Every version of Joomla from 1.5 to 3.4.5 is vulnerable.
- Joomla 3.4.6 has been released to address the vulnerability, and patches have been released for unsupported versions of the software.
As first reported by Sucuri, the vulnerability allows an attacker to exploit the way session data is processed before it’s stored in the database. In several reported cases, a php shell installed via the exploit has been used to modify core files, with one result being unwanted email (spam) being sent from the server.
In line with Sucuri’s findings, we also noticed these attacks shortly after the updates were announced by the Joomla team. On a sample set of servers, we noted about 10 attack attempts per server by Dec 15. As of 2 p.m. on Dec. 16, that number was more than 50 attempts per server, and likely to keep increasing as attackers continue their efforts.
Liquid Web’s Fully Managed cPanel servers include our ServerSecure package by default, and were protected against various versions of this exploit by our ModSecurity rules. While this certainly is good news, it is not a reason to put off updating your software to the latest version.
Has Your Joomla Site Been Targeted?
To check whether your site was targeted by this attack, you can search for a specific string in your domain access logs.
- On a cPanel server, the access logs for each domain are stored in /home/accountname/logs and /home/accountname/access-logs.
- Alternately, the most recent logs for all domains on the server should be in the directory /usr/local/apache/domlogs/.
Once you have located the relevant log files, you can use the grep command to check them. For example, this command checks for attempts to exploit the Joomla vulnerability on sites under the cPanel account joe over the last day:
egrep -H '}__|JDatabaseDriverMysql' /home/joe/access-logs/*
And this command checks for exploit attempts on any of joe’s site logs older than 24 hours, if available:
zgrep -E -H '}__|JDatabaseDriverMysql' /home/joe/logs/*
If any log entries are returned, then you’ll know your site has been targeted. Assuming that Joomla actually is installed on the targeted site, you should check for any recently updated files in the installation or scan it with a tool such as ClamAV or Linux Malware Detect (maldet).
Was Your Joomla Site Protected?
If your site was targeted and you are a Liquid Web customer, you can take the IP address(es) from the log output you found above and check them against Apache’s error_log to see whether the requests were blocked by ModSecurity. In this sample command, we’re checking the IP address 123.123.123.123:
grep 123.123.123.123 /usr/local/apache/logs/error_log
If the requests from that IP address were blocked, you will see a log entry containing something like:
[Tue Dec 15 23:20:25 2015] [error] [client 123.123.123.123] ModSecurity: Access denied ...
If the log does show that ModSecurity blocked the requests, it is likely your site could not be breached. However, regardless of the result, you should proceed with updating your site as soon as possible.
Resolution: Update or Patch Your Joomla Site
The process for protecting your Joomla site against the remote command-execution vulnerability depends on your Joomla version. You can check the current version by logging into your Administration panel. If the version number is not displayed at the bottom of the page in the footer, select Joomla! Update from the Components menu to see your current version.
Joomla 3 Sites Require an Update
If you have not done so already, back up your site and the site database now before proceeding, or check your automated backup solution to ensure that you have a recent backup from which you would be comfortable restoring the site if necessary.
- Log into your Administration panel.
- You should see a banner indicating that version 3.4.6 is available. If so, and if you have backed up your site and the site database, click the Update Now button to update to the latest version.
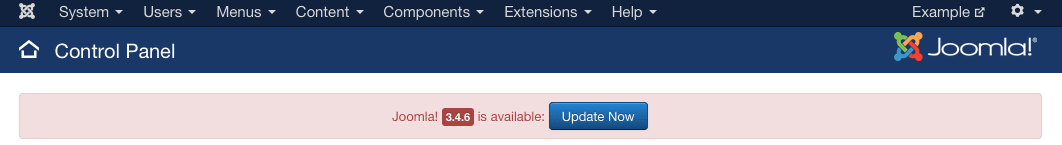
- On the Update page, you are reminded to ensure that your installed extensions are available for the version you’re updating to. Once you have verified that, and have confirmed that you have a backup of the working site, click Install the Update to update Joomla.
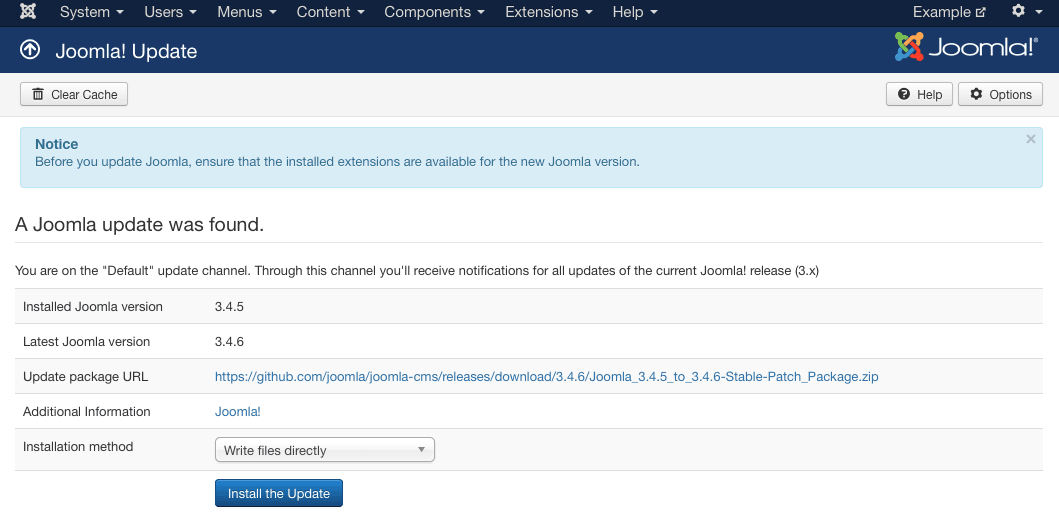
- Once complete, you will see a success page.
- Now select Joomla! Update from the Components menu to confirm that you are on version 3.4.6 (occasionally, the update can sometimes fail to reflect the new version in the Update Success confirmation message).
Joomla 1.5 and 2.5 Sites Require a Patch
Users on unsupported versions are encouraged to consult their developers about migrating to Joomla 3 so that they can receive all security updates.
However, due to the nature of this exploit, Joomla has chosen to make patches available for Joomla versions 1.5 and 2.5 to address this specific issue. The patches can be downloaded directly from Joomla. Applying the patch is as simple as replacing the existing session.php file which is included in the download.
It’s important to note that Joomla’s decision to release patches for unsupported versions of its software in this specific case is due only to the scope and impact of the current vulnerability, and does not mean that any future patches also will be released for legacy versions. Joomla continues to encourage users to migrate to the current version as soon as possible.
- Download the appropriate zip file for your Joomla version from Joomla and unzip it. The extracted archive will contain three nested folders leading to a single file, session.php.
- Connect to your site via FTP, SFTP as the cPanel user, or SSH as the cPanel user and navigate to libraries/joomla/session inside your site’s document root to locate the existing session.php file.
- On a cPanel server where www.yourdomainname.com loads the main Joomla site, the file would be located in the directory /home/accountusername/public_html/libraries/joomla/session.
- On a cPanel server where www.yourdomainname.com/blog loads the main Joomla site, the file would be located in the directory /home/accountusername/public_html/blog/libraries/joomla/session.
- Now back up the existing session.php file on your server so that it can be restored if necessary. You can do that by simply renaming the existing session.php file on your server to something you’ll be able to remember later (you also could give the file a “.old” extension or add a period to the beginning of the file name.)
- To finish, upload the session.php file you downloaded from Joomla to replace the one you renamed, and check that it has the same ownership and permissions.
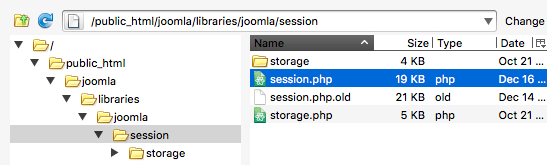 Note: If you uploaded the file while connected to the server as root, the file itself will be owned by root. You may need to change its ownership and group to match the other files in the directory.
Note: If you uploaded the file while connected to the server as root, the file itself will be owned by root. You may need to change its ownership and group to match the other files in the directory.
Related Articles:

About the Author: dpepper
Our Sales and Support teams are available 24 hours by phone or e-mail to assist.
Latest Articles
Change cPanel password from WebHost Manager (WHM)
Read ArticleChange cPanel password from WebHost Manager (WHM)
Read ArticleChange cPanel password from WebHost Manager (WHM)
Read ArticleChange cPanel password from WebHost Manager (WHM)
Read ArticleChange the root password in WebHost Manager (WHM)
Read Article


